Programmable TOTP token that fits any authentication system
Classic SHA-1 TOTP hardware token: high-strength and water-resistant
Programmable hardware TOTP token in a key fob format
Classic hardware TOTP token with SHA-256 algorithm support
Free 2FA app for iOS and Android with encrypted cloud backup, PIN, and biometric protection
OTP delivery via messenger — easy, secure, convenient. The service is available on Telegram, Viber and Facebook Messenger
Delivery of one-time passwords via SMS messages
Free delivery of one-time passwords via email
Free one-time password delivery through push notifications in the Protectimus Smart 2FA app - simply press a button to confirm your login
This way, the CentOS account becomes protected with two different authentication factors. Even if the hacker steals the users’s password using phishing, brute force, social engineering, data spoofing, or any other attack, they can’t access the CentOS account without the one-time password from a user’s 2FA token.
This guide shows how you can set up CentOS two-factor authentication (2FA) using Protectimus RADIUS 2FA component for the integration with Protectimus Cloud 2FA service or Protectimus On-Premise MFA Platform.
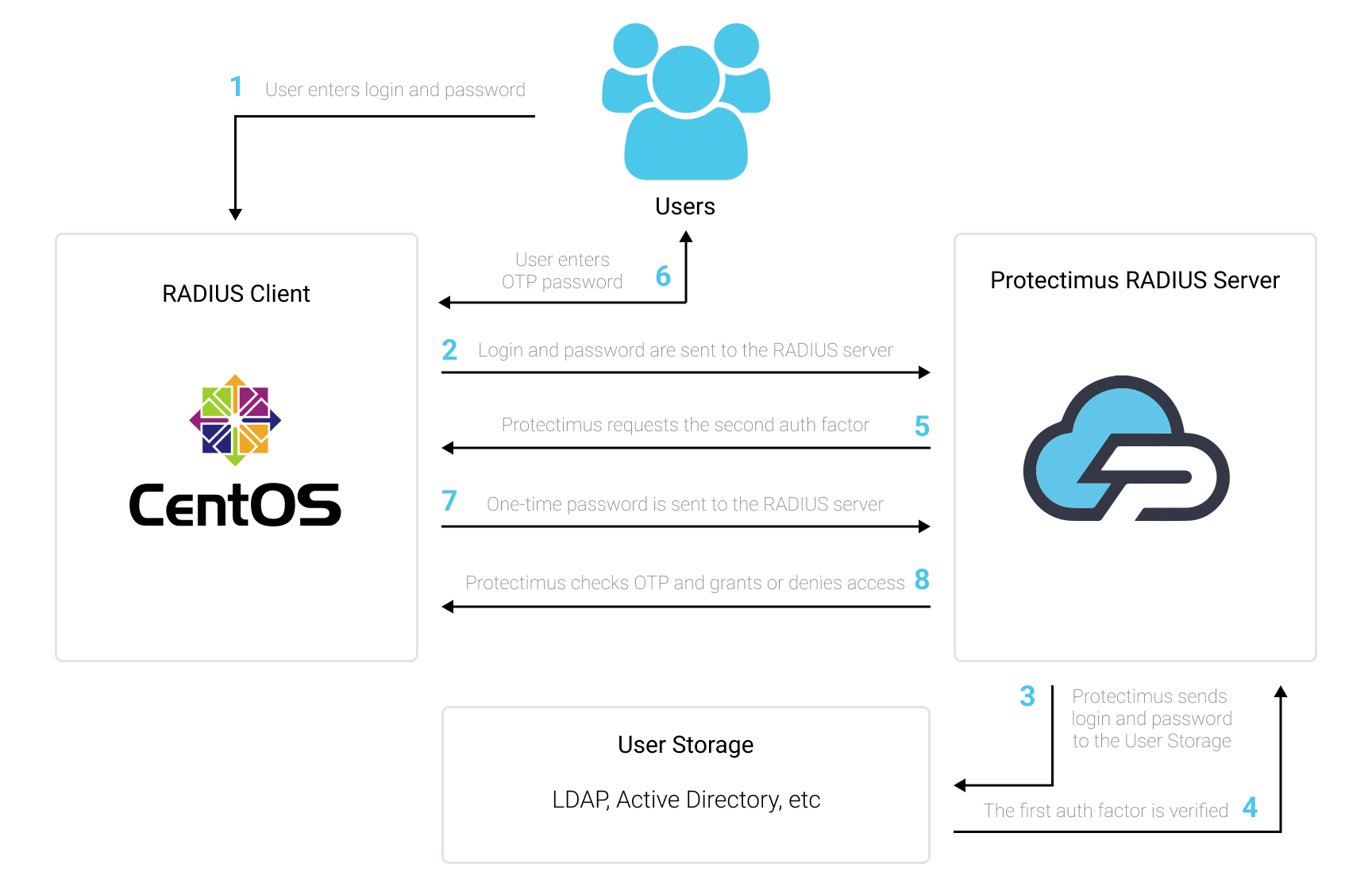
You can set up CentOS two-factor authentication (2FA) with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS 2FA Service or On-Premise 2FA Platform and configure basic settings.
- Install Protectimus PAM module for CentOS 2FA
- Install and configure Protectimus RADIUS Server module.
yum -y install epel-release
yum -y install pam_radius
git clone https://github.com/protectimus/platform-linux.git
cd platform-linux/radius
edit config/radius.yml
docker compose up -d
Configure radius.yml file.
Configure Protectimus RADIUS Server settings in the radius.yml file. It must be located in the same directory as the executable.
You will find detailed instructions on available properties that you can add to the radius.yml file in our Protectimus RADIUS Server Configuration Guide.
The example of radius.yml file configuration:
radius:
secret: secret
auth-port: 1812
auth:
# Could be :
# - LDAP
# - PROTECTIMUS_PASSWORD
# - PROTECTIMUS_OTP
# - PROTECTIMUS_PUSH
providers:
- PROTECTIMUS_OTP
protectimus-api:
login: login@domain.com
api-key: aslkjdljsdlaskmWpXjT5K0xqLXkd3
url: https://api.protectimus.com/
resource-name: radius
resource-id: 723
# server[:port] shared_secret timeout (s)
127.0.0.1 secret 1
ChallengeResponseAuthentication yes
Configure PAM for SSH to use RADIUS
Add auth required pam_radius_auth.so after auth substack password-auth into /etc/pam.d/sshd
#%PAM-1.0
auth required pam_sepermit.so
# protectimus pam radius
auth substack password-auth
auth required pam_radius_auth.so
auth include postlogin
# Used with polkit to reauthorize users in remote sessions
-auth optional pam_reauthorize.so prepare
CentOS multi-factor authentication setup is now complete. If you have other questions, contact our customer support service.
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
USA: +1 786 796 66 64
Ireland: +353 19 014 565
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
USA: +1 786 796 66 64
Ireland: +353 19 014 565


