The Protectimus On-Premise Two-Factor Authentication Platform can be installed on your private servers or in your private cloud.
- Private server installation requirements: Java (JDK version 8); PostgreSQL DBMS, version 10 or later.
- Private cloud installation requirements: CPU: 2 cores, memory: 8 GB; OS: Linux; cloud disk: 20 GB; load balancer.
To ensure uninterrupted operation of your multi-factor authentication server, deploy it to a cluster of several servers (we recommend using at least three nodes). Use a load balancer to distribute the load among them.
To install the Protectimus On-Premise Platform, you can use the installer for Windows or create a Docker Image.
How to Get Started with the Protectimus MFA Platform
- Install the Platform creating a Docker Image or using the installer for Windows.
- Register and activate your license.
- Set up user synchronization with your user directory (or manually add/import users).
- Configure basic settings, including adding resources and tokens.
- Issue and import a trusted SSL certificate.
- Integrate the platform into your infrastructure.
For additional guidance, check these important resources:
1. Protectimus Platform Installation Using a Docker Image
- To start installing the Protectimus On-Premise Platform, first of all, download and install docker and docker-compose:
- Then clone the git repository: https://github.com/protectimus/platform-linux.git
- Go to the platform-linux/platform directory and run:
docker-compose up -d
- You can monitor the process of platform deployment using the command:
docker-compose logs -f
- After the deployment process is complete, the platform will be available at: https://localhost:8443
2. Protectimus Platform Installation on Windows
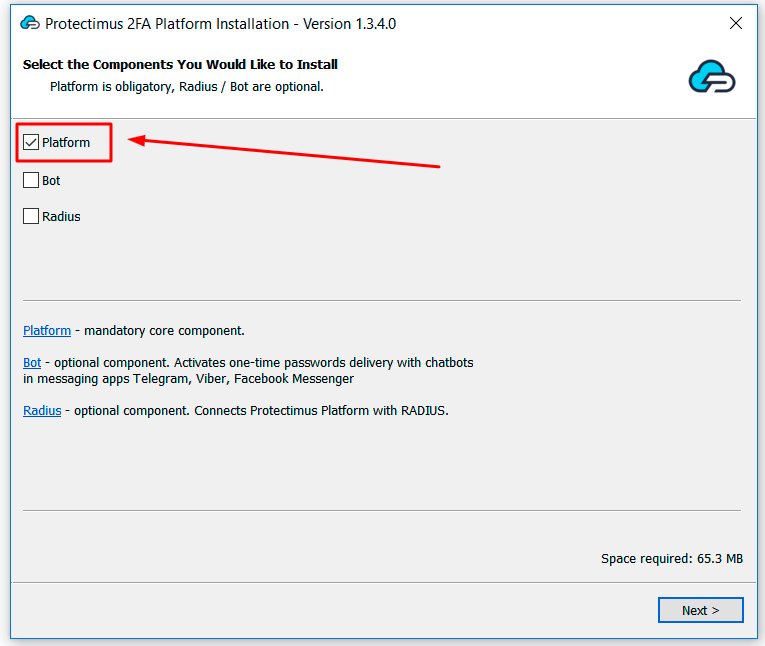
- Download and run the Protectimus Platform installer using the button below.
Check the Platform box and click Next.
If you are going to use RADIUS integrations, and/or OTP delivery via chat-bots in messaging apps Telegram, Facebook Messenger, or Viber, also check the appropriate boxes.
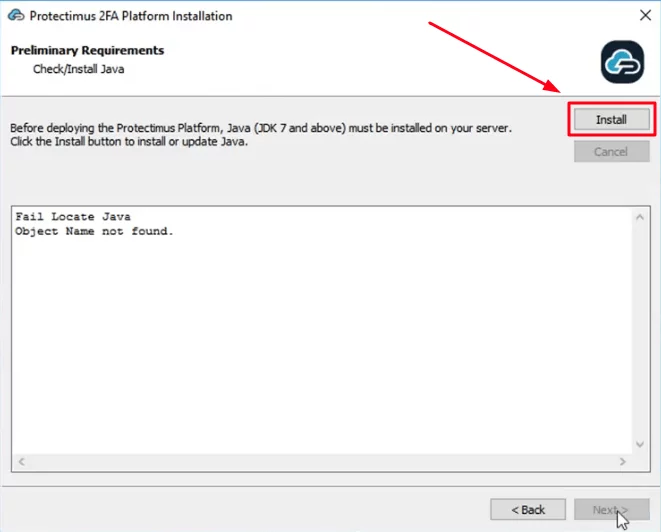
- Before deploying the Protectimus Platform, Java must be installed on your server. Click the Install button to check for Java. If it’s not installed yet, the latest JDK version will be installed automatically.
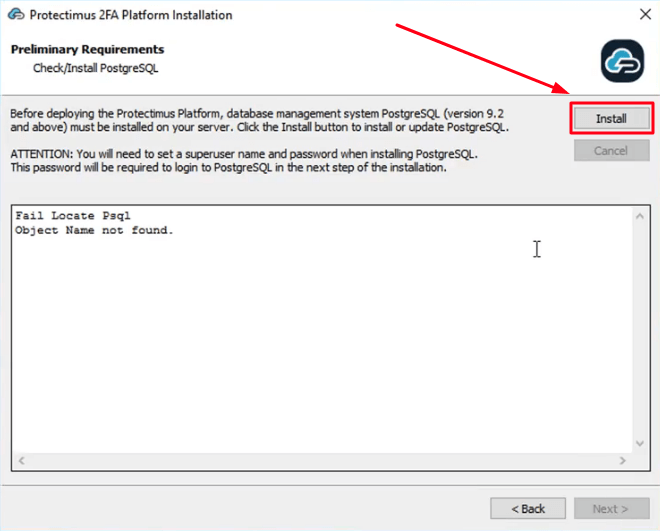
- Also, database management system PostgreSQL (version 9.2 and above) must be installed on your server. Click the Install button to check for PostgreSQL. If it’s not installed yet, the latest PostgreSQL version will be installed automatically.
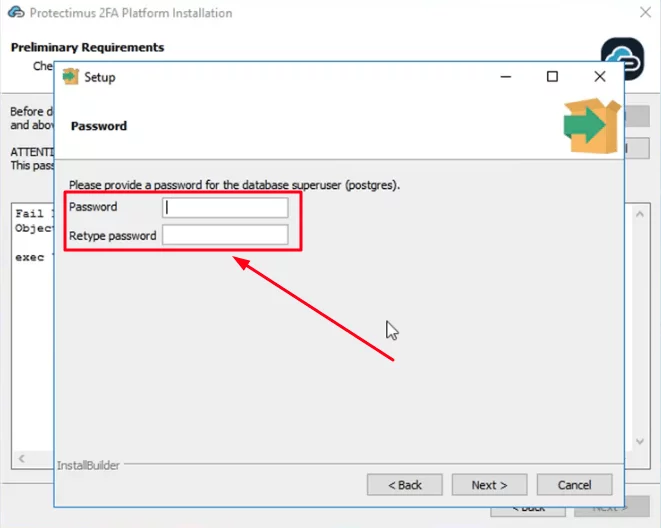
ATTENTION: You will need to set a superuser name and password during installation. You’ll need this password to login to PostgreSQL later.

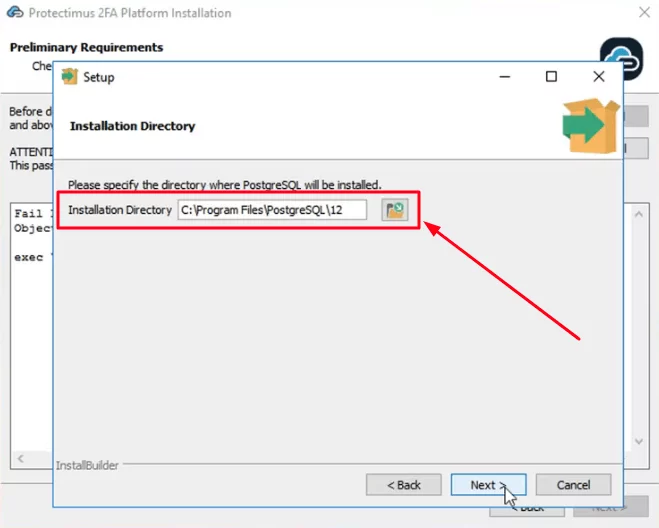
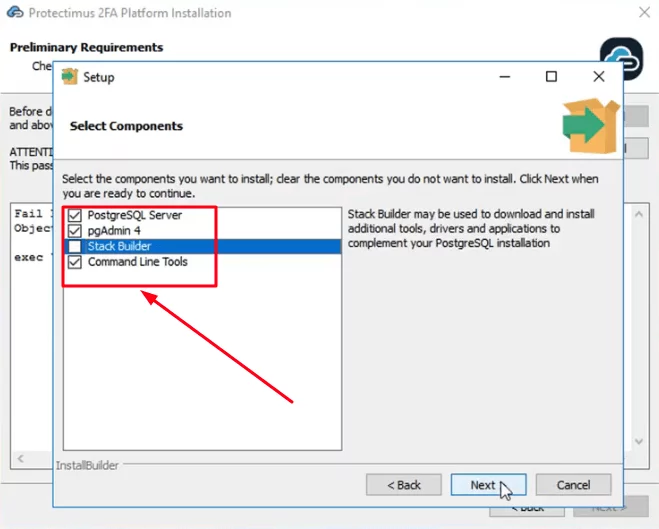
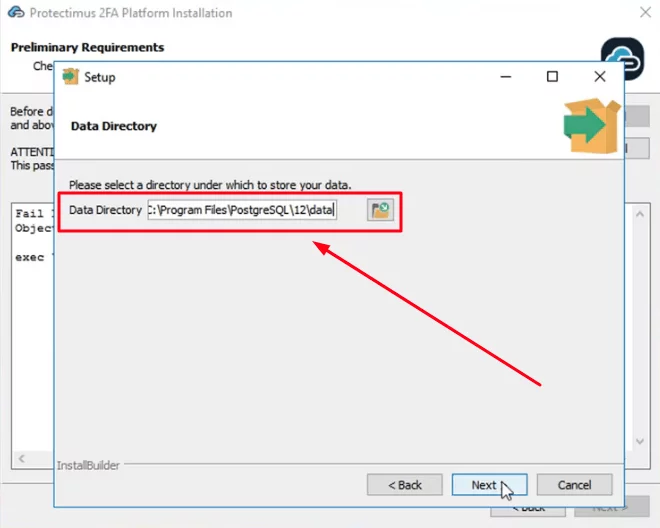
Please, remember your superuser name (postgres) and the password you’ll add on this step. This name and password will be required to login to PostgreSQL later.
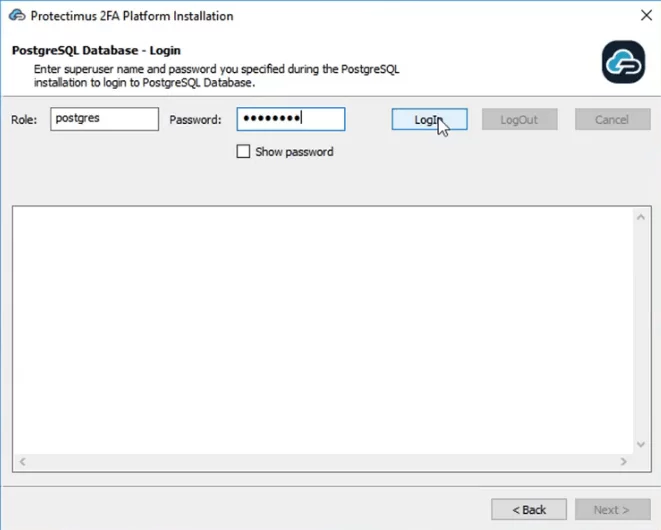
- Login to PostgreSQL Database. Enter the superuser name and password you specified during the PostgreSQL installation and click LogIn. Then click Next to continue the installation.
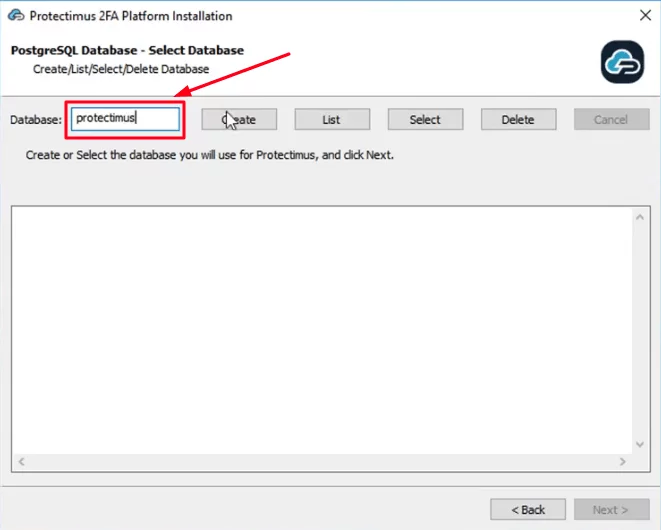
- Create and Select the database you will use for Protectimus On-Premise Platform.
- Create a new database. Enter the desired database name and click Create.
- Check whether it is created or not using the button List.
- Click the Select button, choose the database you’ve just created, and click Next.
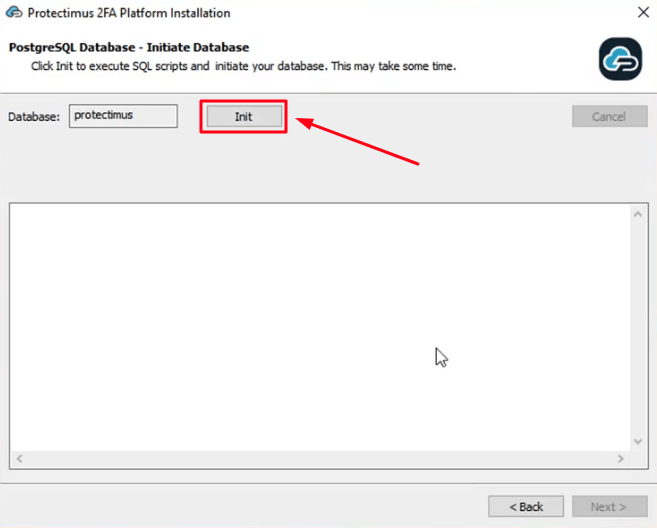
- Initiate the database. Click Init to execute SQL scripts and initiate your database. This may take some time.
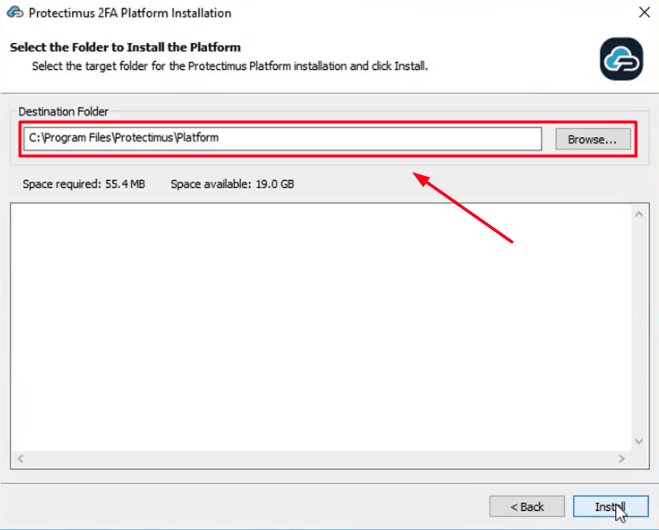
- Select the folder to install the Protectimus Platform and click Install.
The server will be started on port 8080 or 8443, and the platform will be available from the address
http://localhost:8080 or
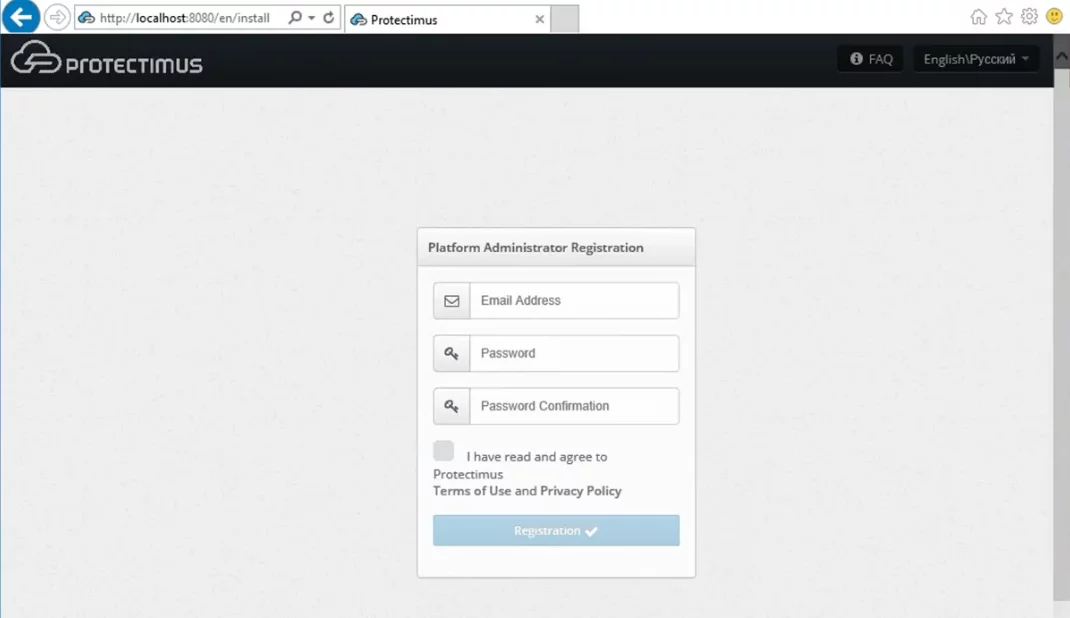
https://localhost:8443. It will be opened automatically after the installation. After launching the platform, you’ll need to register in the system.
3. How to Get Registered in Protectimus System
The installer will automatically open the registration form at
http://localhost:8080 or
https://localhost:8443.
Please, create an account and log in to configure the necessary settings.
4. How to Pay and Activate the License
After testing the Protectimus Platform successfully, you’ll need to get a license. To do so, go to
http://platform_path/licensing, select the option you require and get the license key.
Using the key you received, you can pay for and download your license online. To do so:
- Go to https://service.protectimus.com/en/platform and click Purchase License.
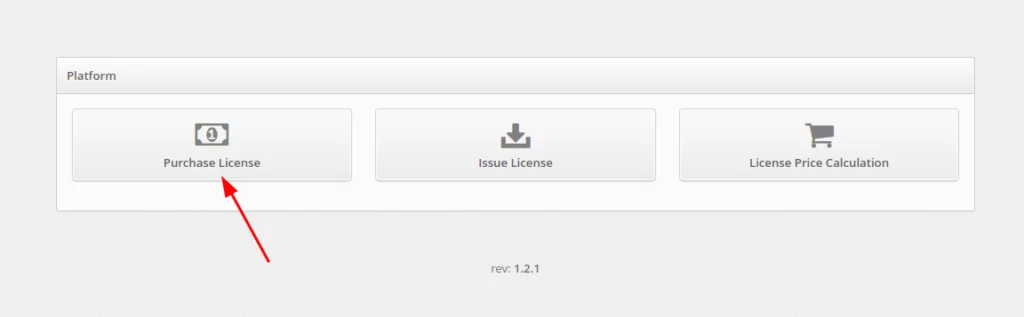
- Enter your license key into the Licensing Key field and click Submit.
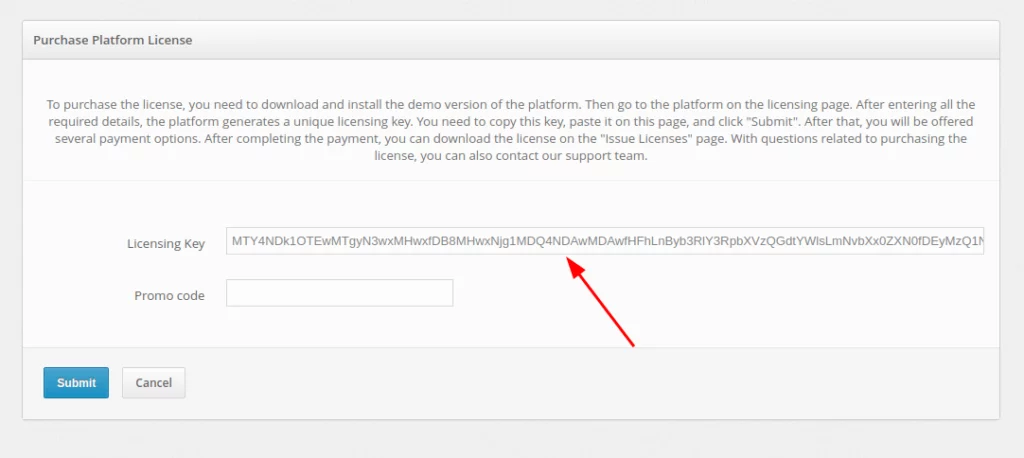
- On the next step, click on the Pay button.
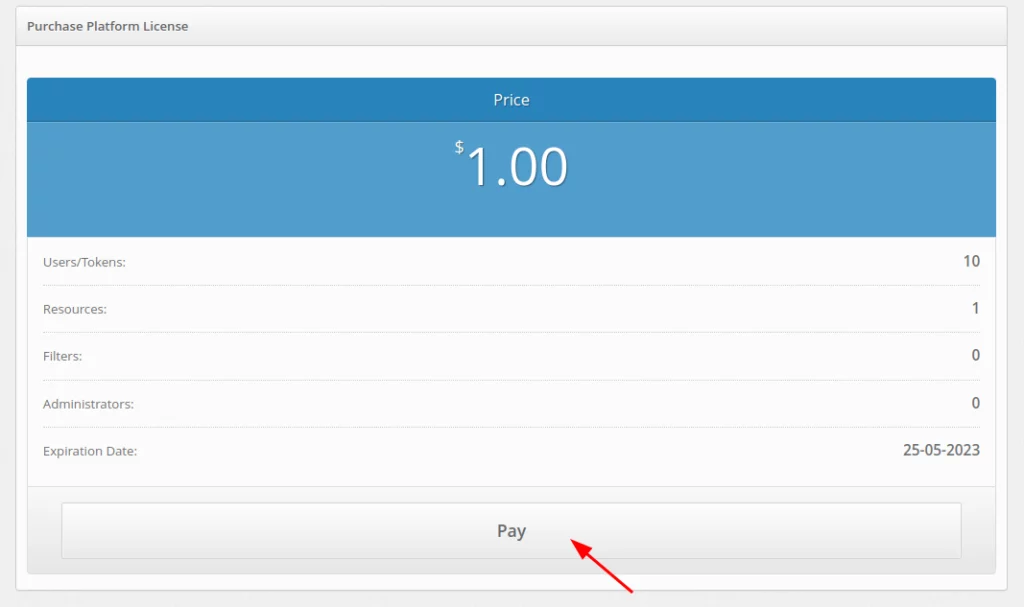
- Choose a payment method. If you require an alternate payment method, contact Protectimus customer support.
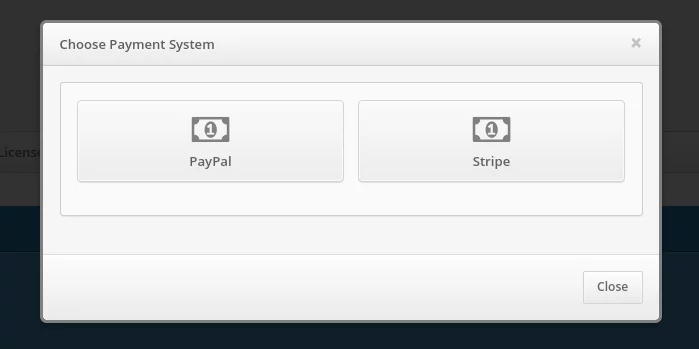
- After successful payment click on the Issue Platform License button.
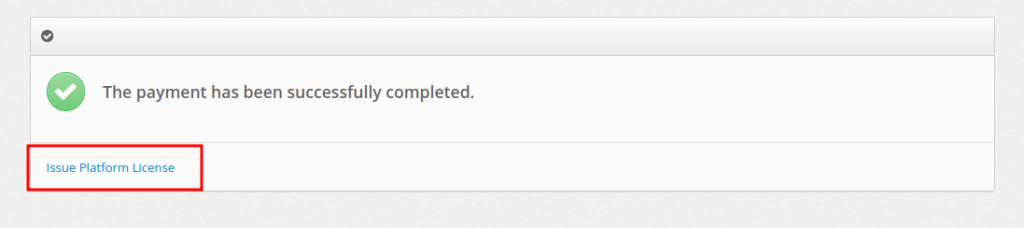 You can also do this on the page https://service.protectimus.com/en/platform by clicking the Issue License button.
You can also do this on the page https://service.protectimus.com/en/platform by clicking the Issue License button.
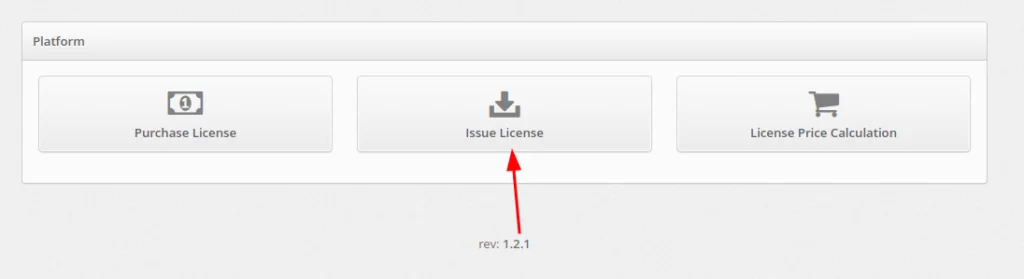
- Enter the key into the Licensing Key field and click Submit. After that, the license file will be downloaded.
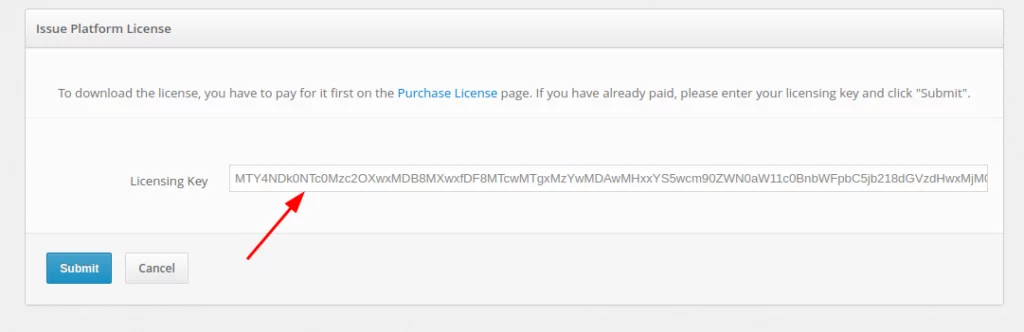
- After receiving the license file, download it to the server and provide the path to the license file in the licence.file.path parameter, in the file named protectimus.platform.properties. Please note that the path to the license file should be indicated with double backslashes
(eg. C:\\some\\path\\file).
5. How to Enable Users Synchronization With Your User Directory
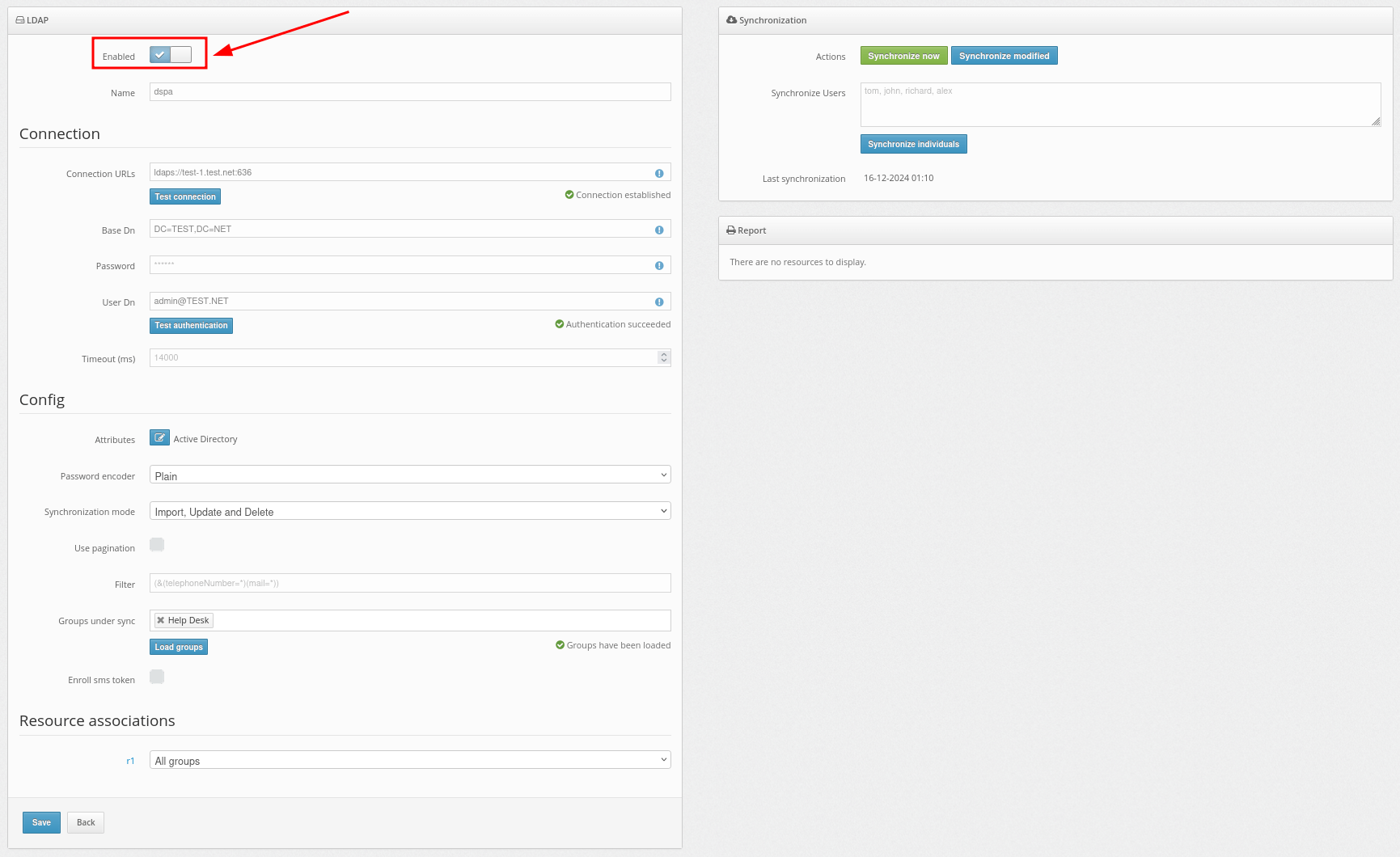
- Login to your Protectimus account, and click: Users – Synchronization – Add LDAP user provider
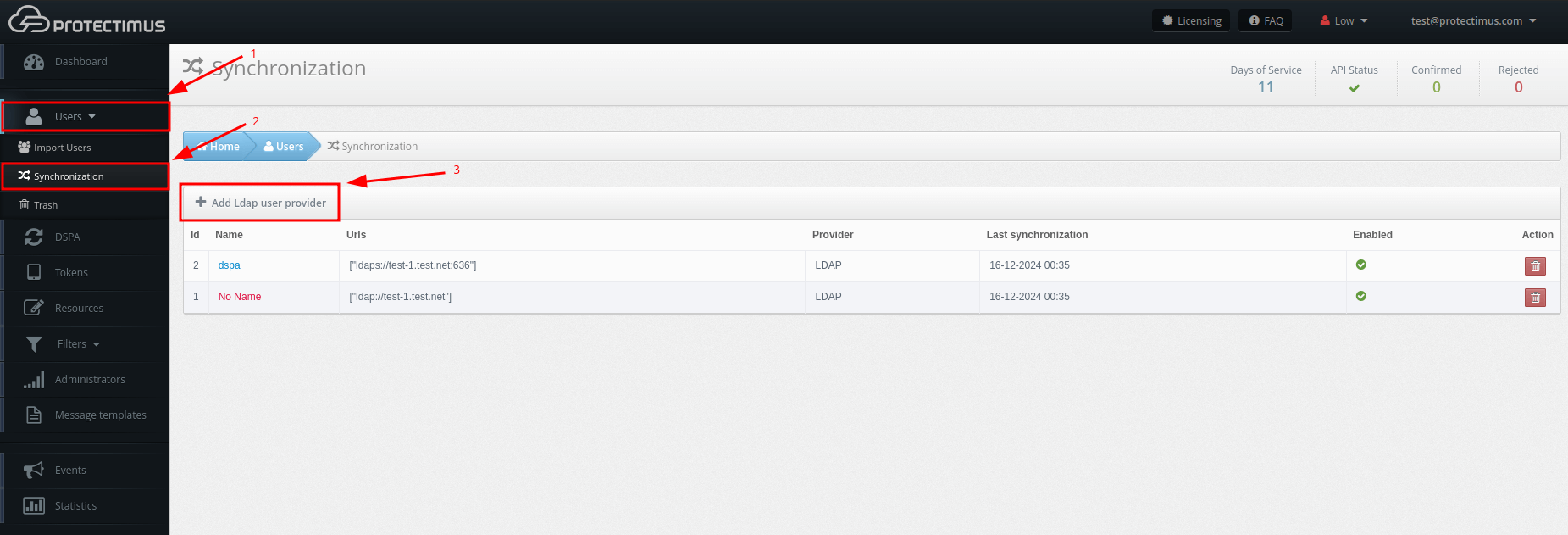
- In the Connection section, fill in the details about your user directory.
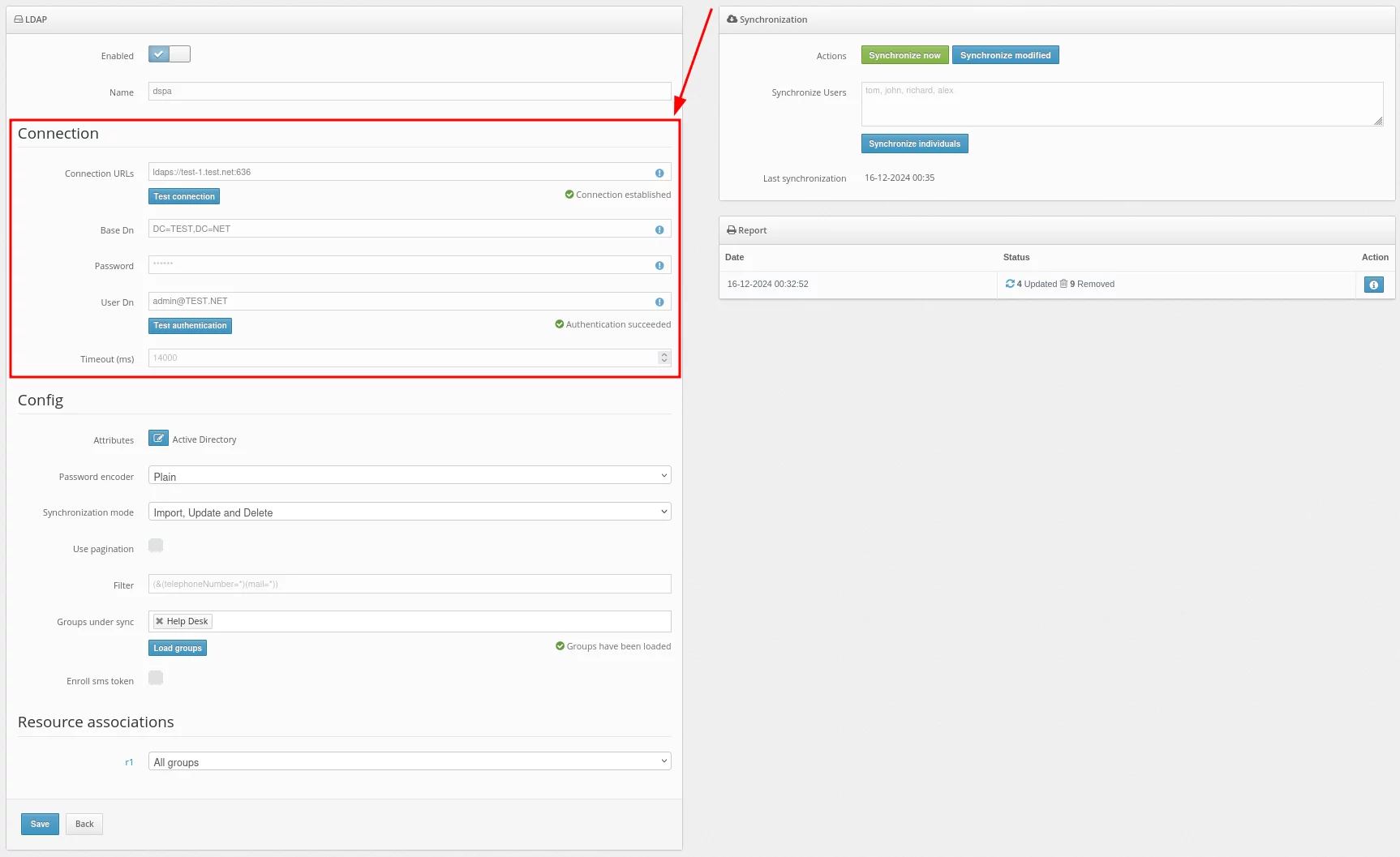
Basic settings:
| Field |
Value |
Note |
| Connection URLs |
URL to connect to your LDAP server |
Example: ldaps://dc1.domain.local:636
For DSPA, you need to use the LDAP connection, and you also need to import the SSL certificate.
A standard way:
keytool -import -alias ___ -file '___.cer' -keystore 'C:\Program Files\Java\jre___\lib\security\cacerts' -storepass changeit
|
| Base DN |
Full DN of the directory in which your users are stored |
Example:
DC=domain,DC=local
|
| Password |
The password of the specified user |
|
| User DN |
DN or userPrincipalName of the administrator or user who has access to user information |
Example:
CN=Administrator, CN=Users, DC=demo, DC=domain, DC=local
administrator@domain.local
For DSPA, the user must have rights to change passwords
|
| Timeout (ms) |
Connection timeout |
|
- After filling in details about your user directory, add synchronization attributes.
Click on the Attributes button.
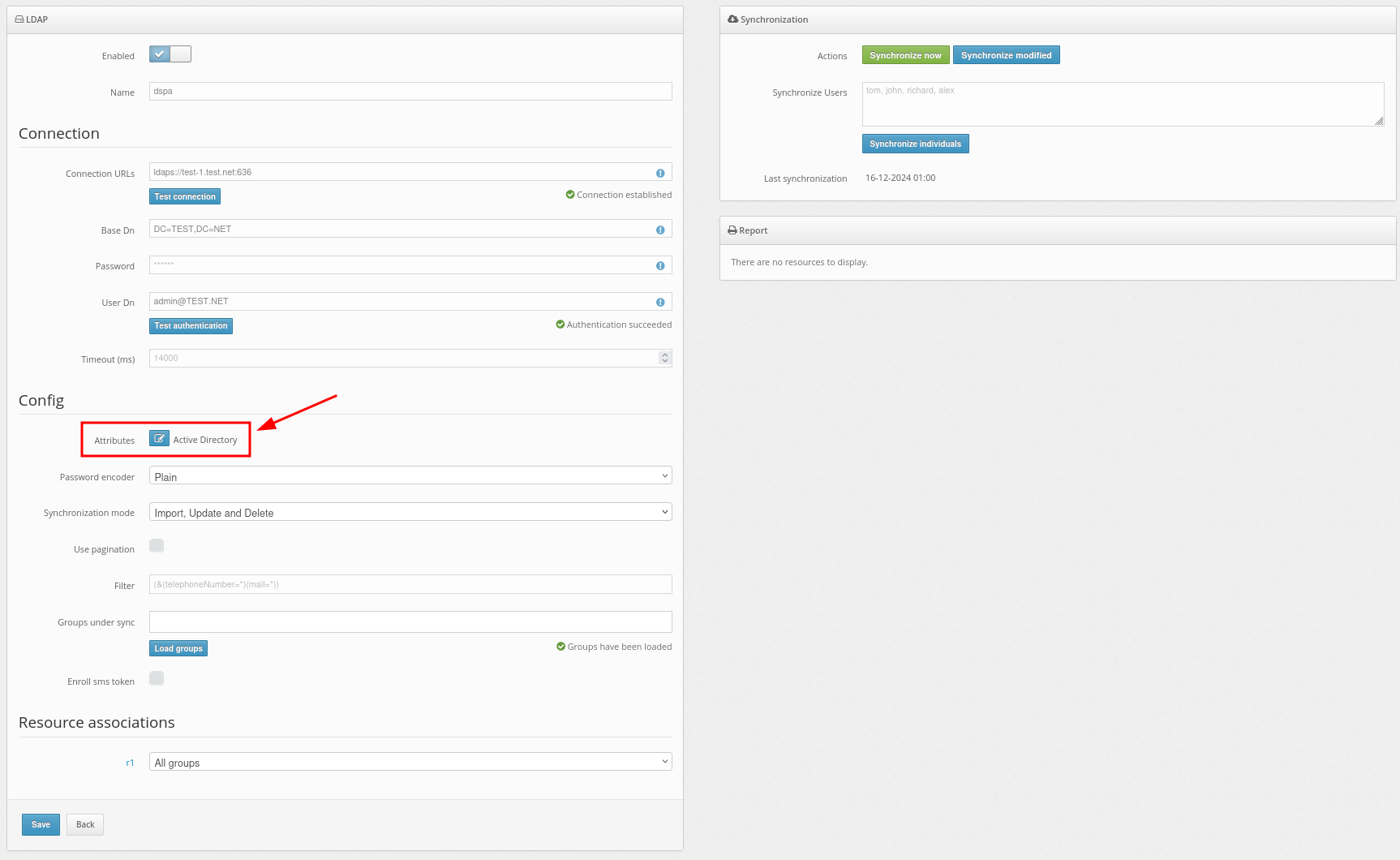 Then add your attributes as shown in the example.
Additionally, the OpenLDAP configuration is available from the provided vendors. You can select it in the Vendor field.
Then add your attributes as shown in the example.
Additionally, the OpenLDAP configuration is available from the provided vendors. You can select it in the Vendor field.
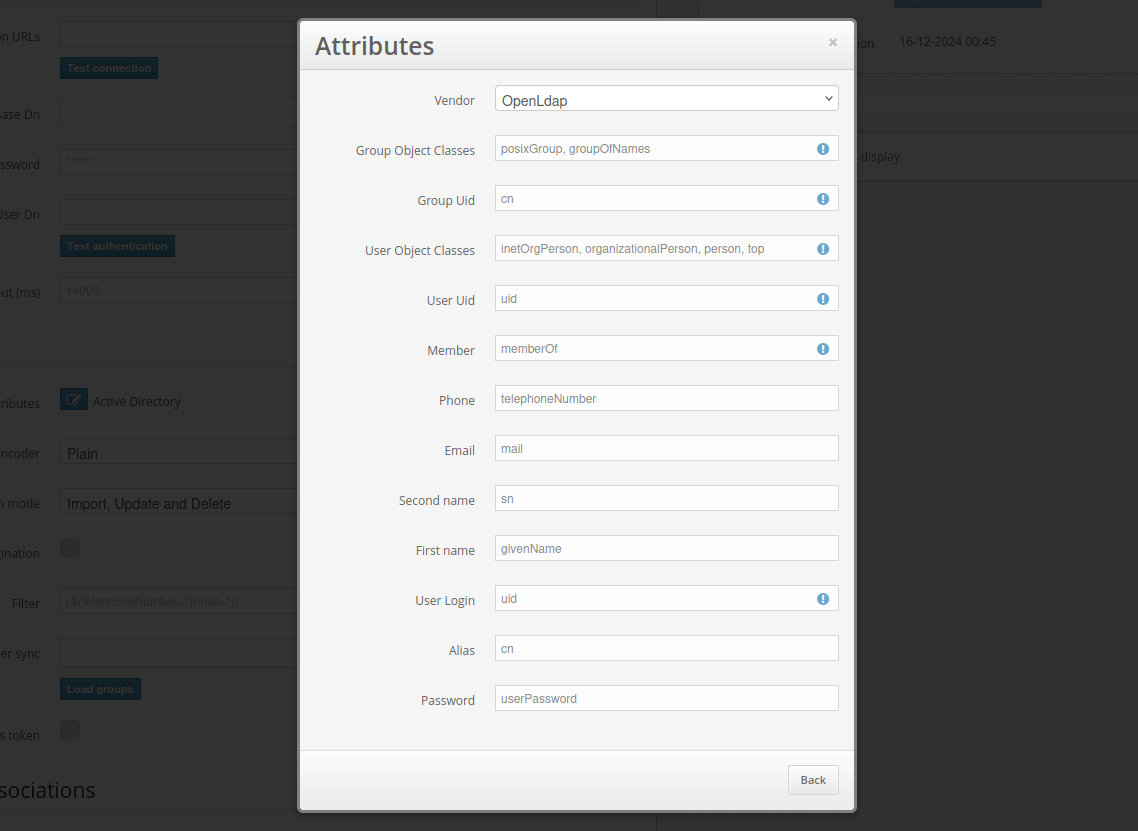
- Now configure the Password Encoder setting.
Select an algorithm that matches your configuration. Available algorithms: AD-specific (UTF-16LE), Plain, BCRYPT, SHA256, SSHA256, SHA512, SSHA512, MD4, MD5, SMD5, SHA, and SSHA.
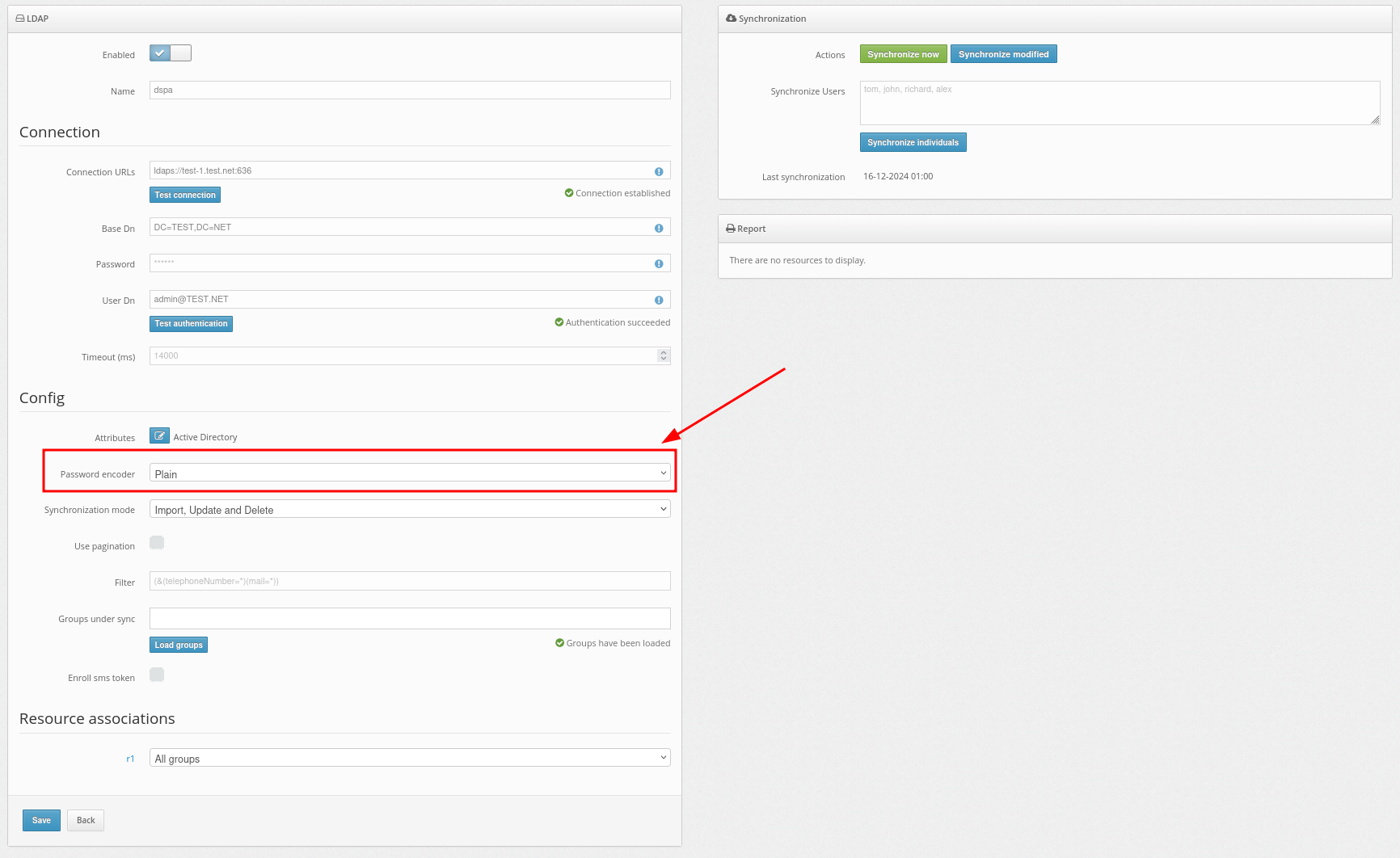
- After successfully adding the user provider, you need to import the users into the Protectimus system and synchronize them with your user directory.
In the Synchronization mode field, you should choose how you would like to import your users.
Importing users can be set up in three ways:
- Import – will never update user data.
- Import and Update – will always update user data when possible.
- Import, Update and Delete – will always update user data when possible. Protectimus users, as well as the software tokens assigned to them, will be removed upon the user’s removal from external user storage.
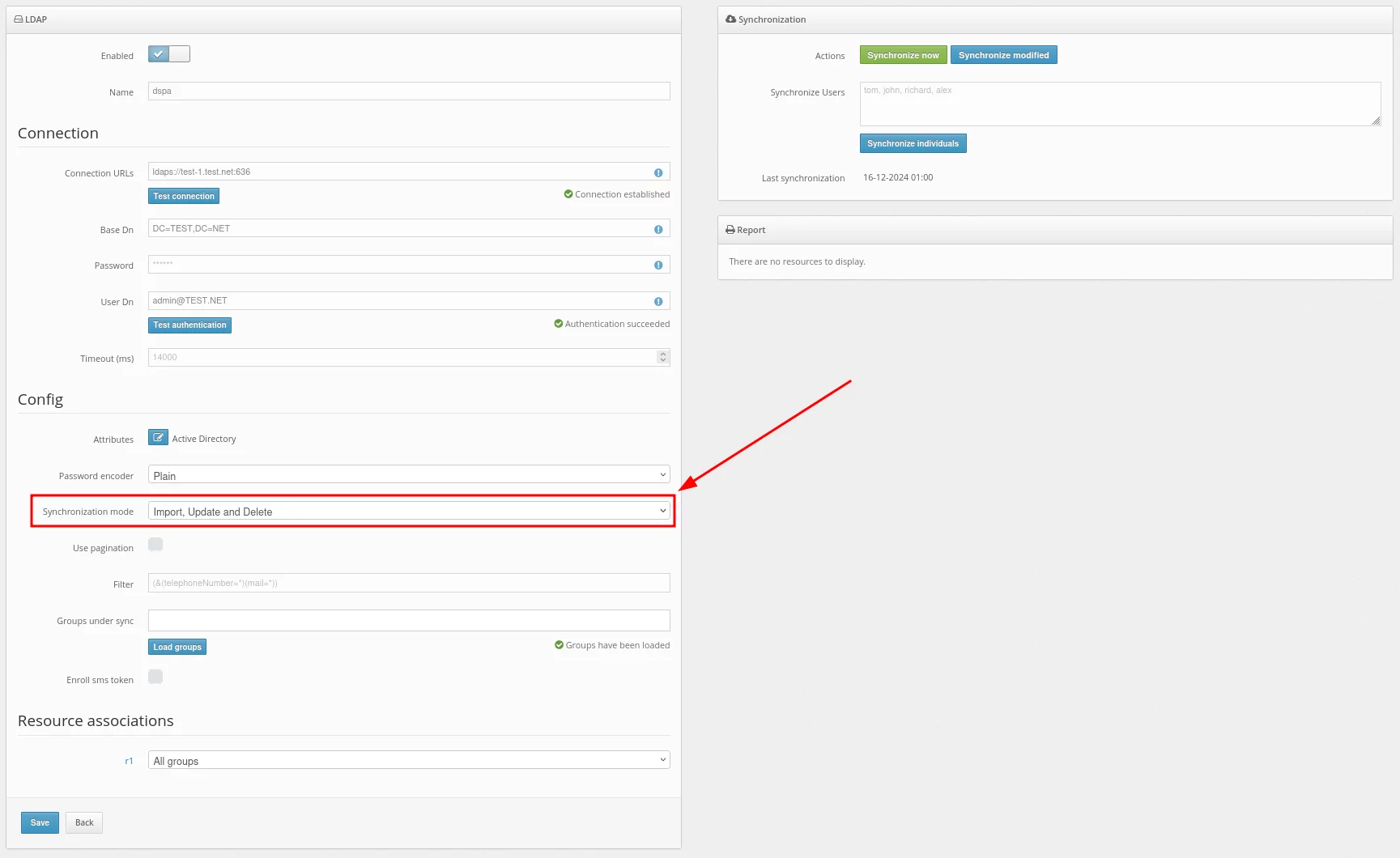
- Now configure the Use pagination setting.
When Use pagination is activated, it means that if the number of records exceeds 200 or 500, multiple queries will be used for retrieval. This is due to LDAP typically returning a limited number of entries by default.
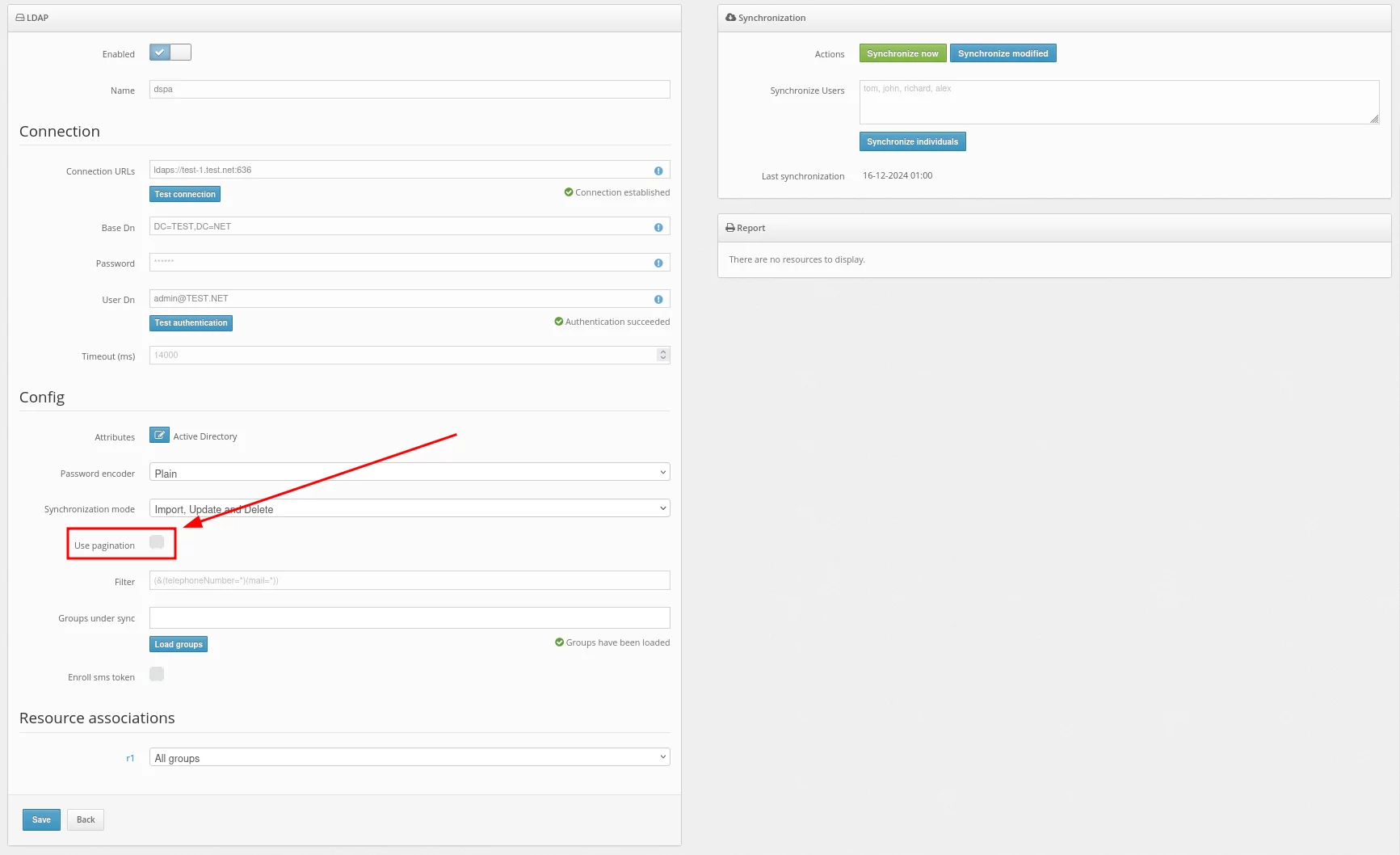
- Set up a filter to be applied during synchronization.
Use this filter to select only the users you want to synchronize.
For example, to import only those users who have the telephoneNumber and mail attributes specified, set up such a filter:
(&(telephoneNumber=*)(mail=*))
To import users from a specific group, choose the required group. In our example, it is the Users group.
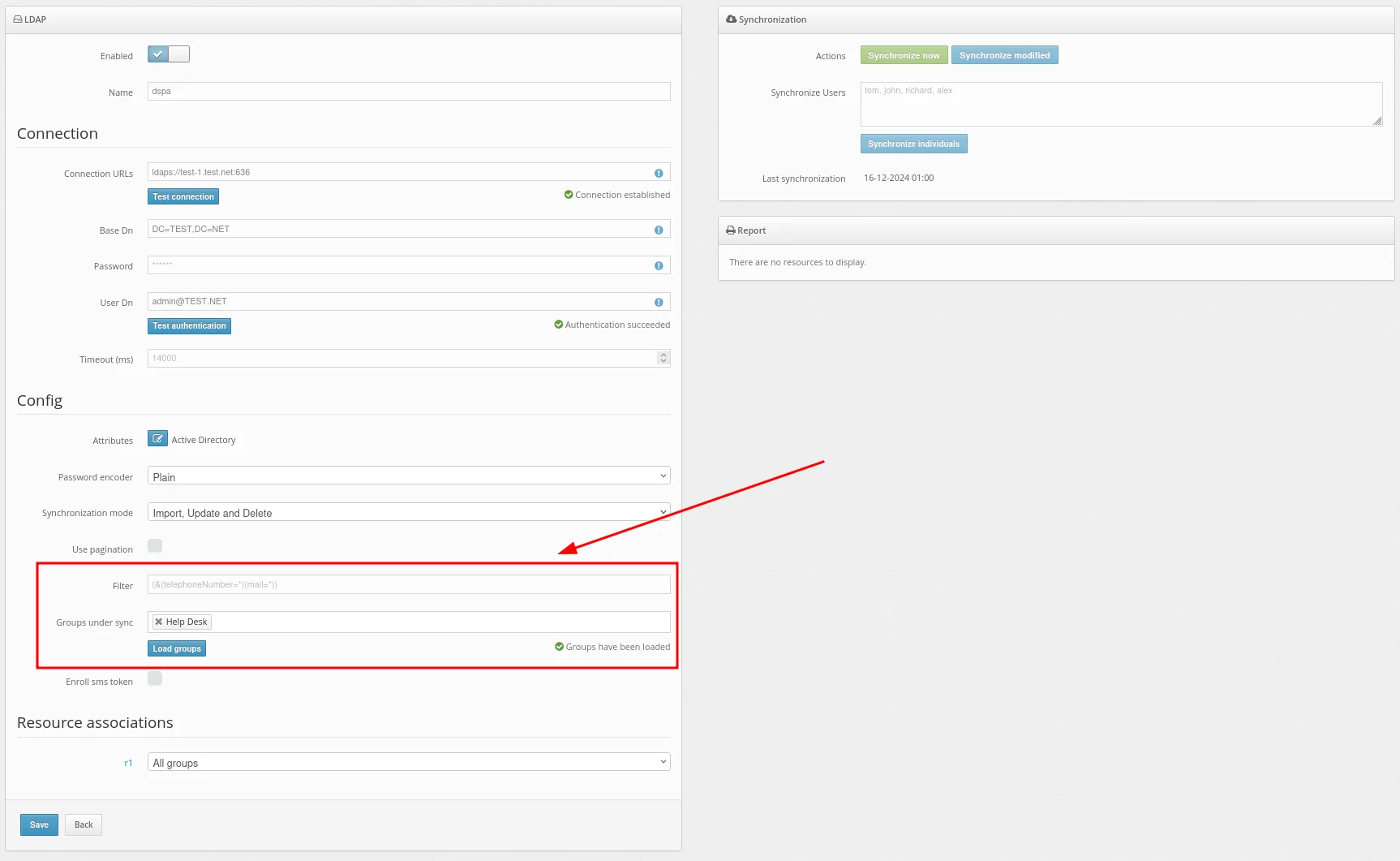
- Now configure the Enroll SMS token setting.
When Enroll SMS token is activated, SMS tokens will be enrolled and assigned to your users during synchronization.
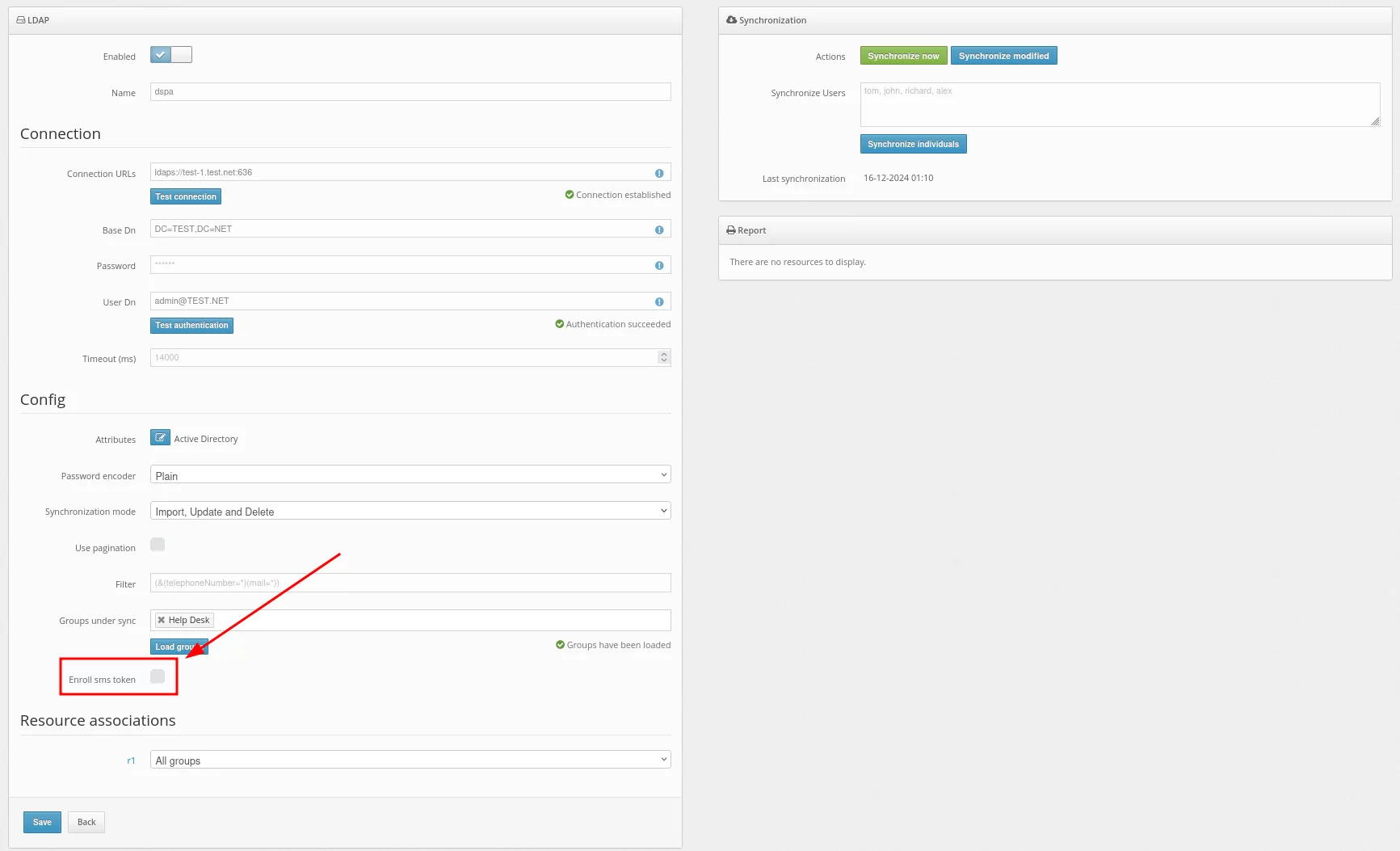
- In the Resource associations section, you can choose the resource to which the users will be assigned during synchronization.
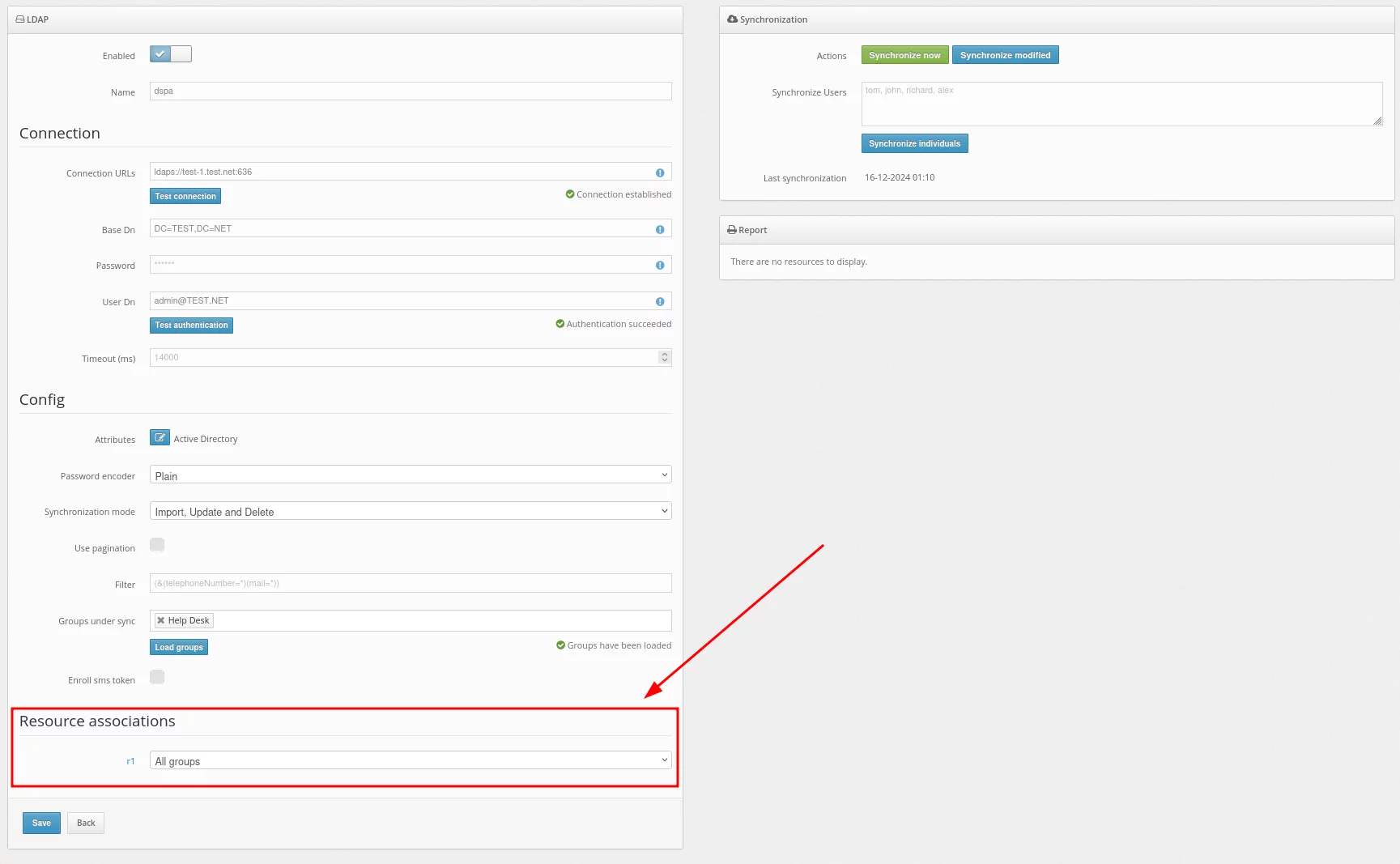
- The next step is to enable user synchronization. This can be accomplished in three ways:
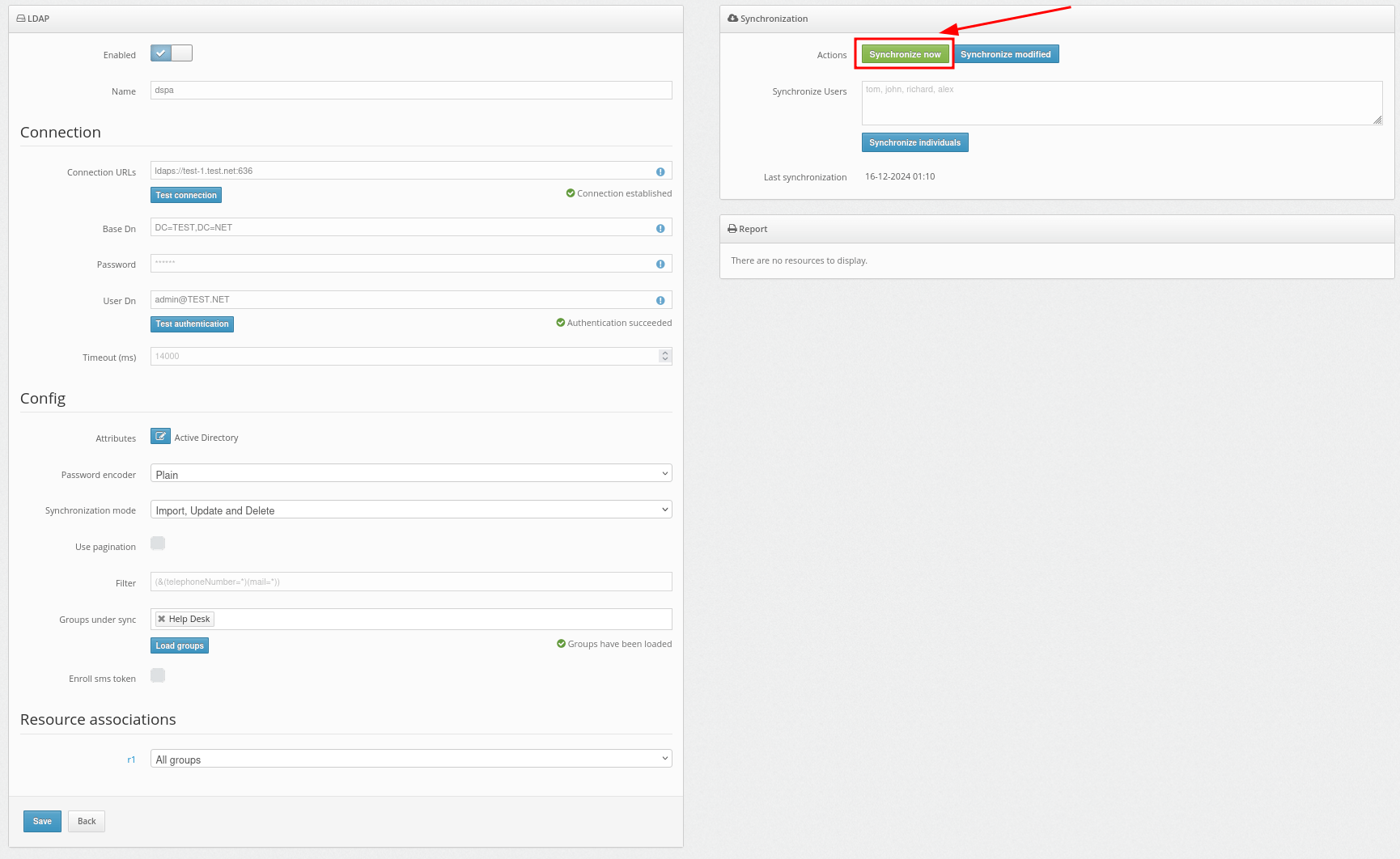
- Use the Synchronize now button to synchronize all users at once.
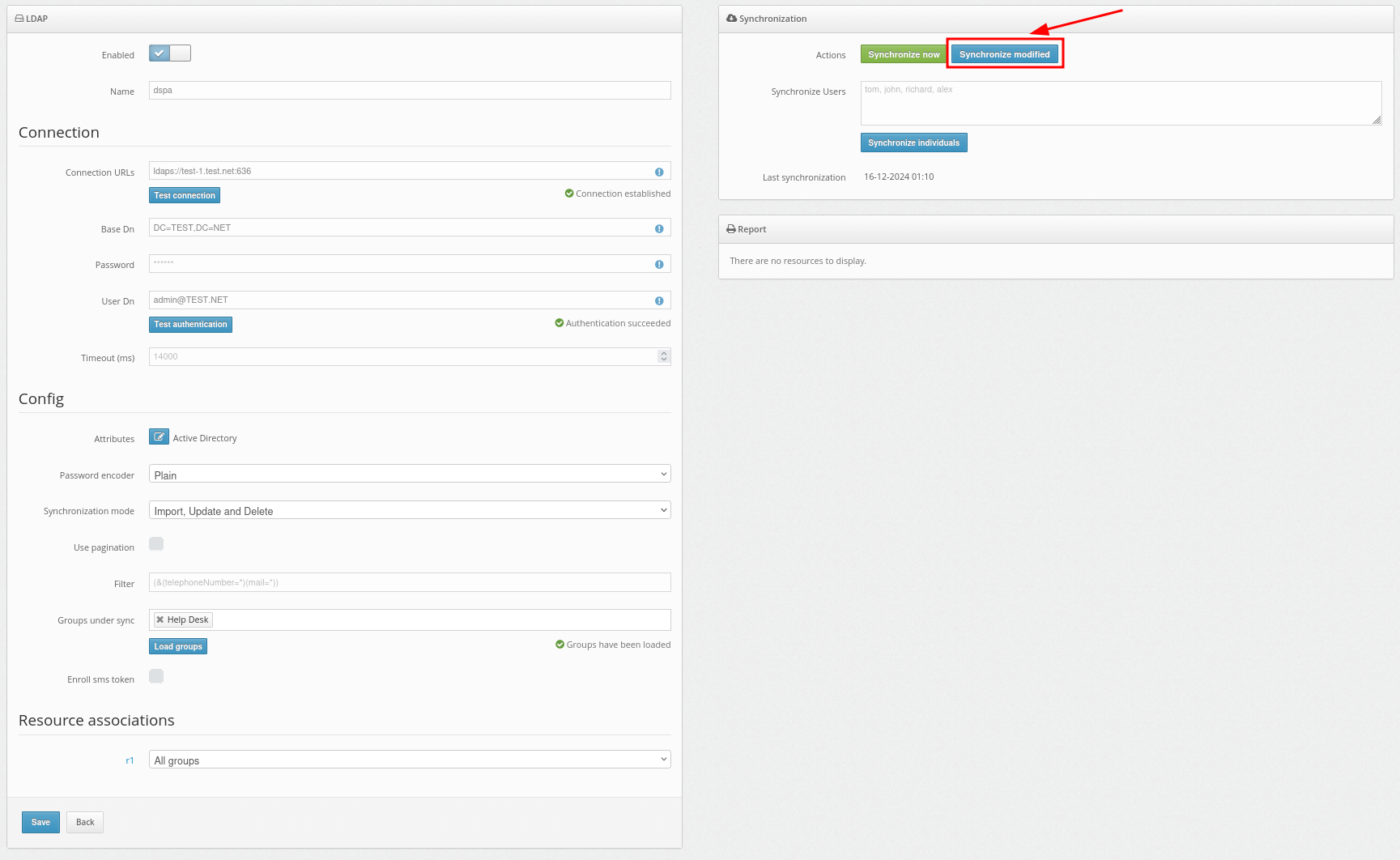
 You can also select the Synchronize modified button to synchronize only the users who have been modified since the last synchronization.
You can also select the Synchronize modified button to synchronize only the users who have been modified since the last synchronization.
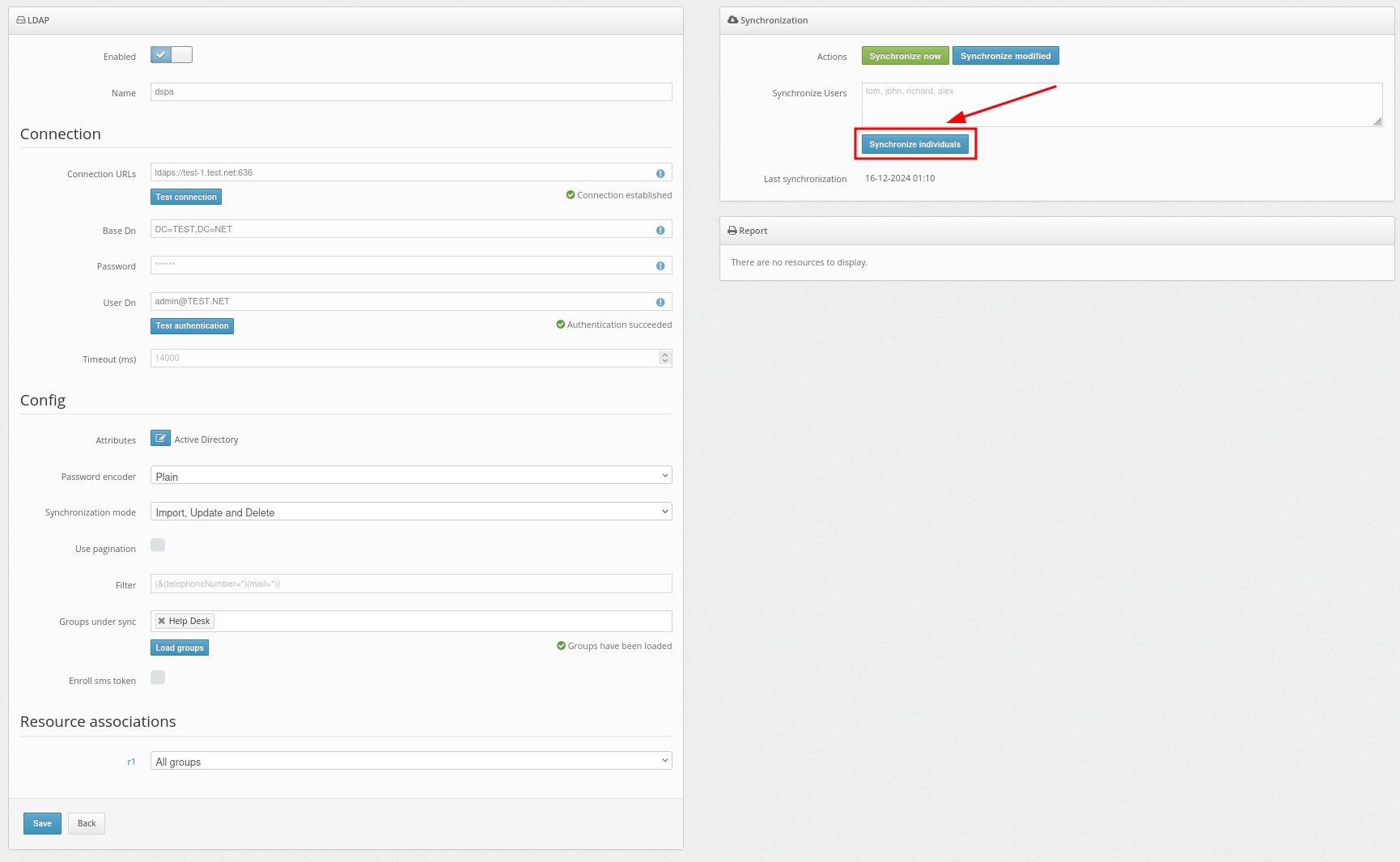
- Use the Synchronize individuals feature to synchronize only the selected users from your user directory.
- Or enable automatic user synchronization by activating the Enabled option at the top of the page.
6. How to Configure Basic Settings
Basic settings, required for the operation of Protectimus Two-Factor Authentication Platform, include:
- Adding Resource.
- Adding Users. You can enable user synchronization with your directory or add/import users manually.
- Adding Tokens.
PLEASE NOTE: If you plan to use Protectimus BOT, Protectimus MAIL, or Protectimus SMS tokens to deliver one-time passwords to your users, follow these instructions to set up the OTP delivery methods:
Additionally, you can enable the Users’ Self-Service Portal, allowing users to enroll, register, and manage their tokens independently.
- Assigning Tokens to Users;
- Assigning Tokens with Users to a Resource.
Also, some additional features are available:
7. How To Integrate and Configure the Protectimus On-Premise Platform
Integrate the Protectimus On-Premise MFA Platform with the system you want to secure with two-factor authentication. To do this, find the relevant integration guide on the
Integrations page.
If you can’t find the required guide of have any questions, contact our
support team — we’ll be happy to assist you with the integration.











 The server will be started on port 8080 or 8443, and the platform will be available from the address http://localhost:8080 or https://localhost:8443. It will be opened automatically after the installation. After launching the platform, you’ll need to register in the system.
The server will be started on port 8080 or 8443, and the platform will be available from the address http://localhost:8080 or https://localhost:8443. It will be opened automatically after the installation. After launching the platform, you’ll need to register in the system.





 You can also do this on the page https://service.protectimus.com/en/platform by clicking the Issue License button.
You can also do this on the page https://service.protectimus.com/en/platform by clicking the Issue License button.


 Basic settings:
Basic settings:
 Then add your attributes as shown in the example.
Additionally, the OpenLDAP configuration is available from the provided vendors. You can select it in the Vendor field.
Then add your attributes as shown in the example.
Additionally, the OpenLDAP configuration is available from the provided vendors. You can select it in the Vendor field.







 You can also select the Synchronize modified button to synchronize only the users who have been modified since the last synchronization.
You can also select the Synchronize modified button to synchronize only the users who have been modified since the last synchronization.





