Programmable hardware TOTP token in a card format that fits any authentication system
Classic hardware TOTP token with SHA-1 algorithm support
Programmable hardware TOTP token in a key fob format that fits any authentication system
Classic hardware TOTP token with SHA-256 algorithm support
Programmable hardware TOTP token in a card format that fits any authentication system
Classic hardware TOTP token with SHA-1 algorithm support
Programmable hardware TOTP token in a key fob format that fits any authentication system
Classic hardware TOTP token with SHA-256 algorithm support
A free 2FA authenticator app with cloud backup, easy token transfer to a new phone, PIN and biometric authentication protection
Free OTP delivery with chatbots in messaging apps
Delivery of one-time passwords via SMS messages
Free delivery of one-time passwords via email
Free one-time passwords delivery via push notifications
A free 2FA authenticator app with cloud backup, easy token transfer to a new phone, PIN and biometric authentication protection
Free OTP delivery with chatbots in messaging apps
Delivery of one-time passwords via SMS messages
Free delivery of one-time passwords via email
Free one-time passwords delivery via push notifications
Guides
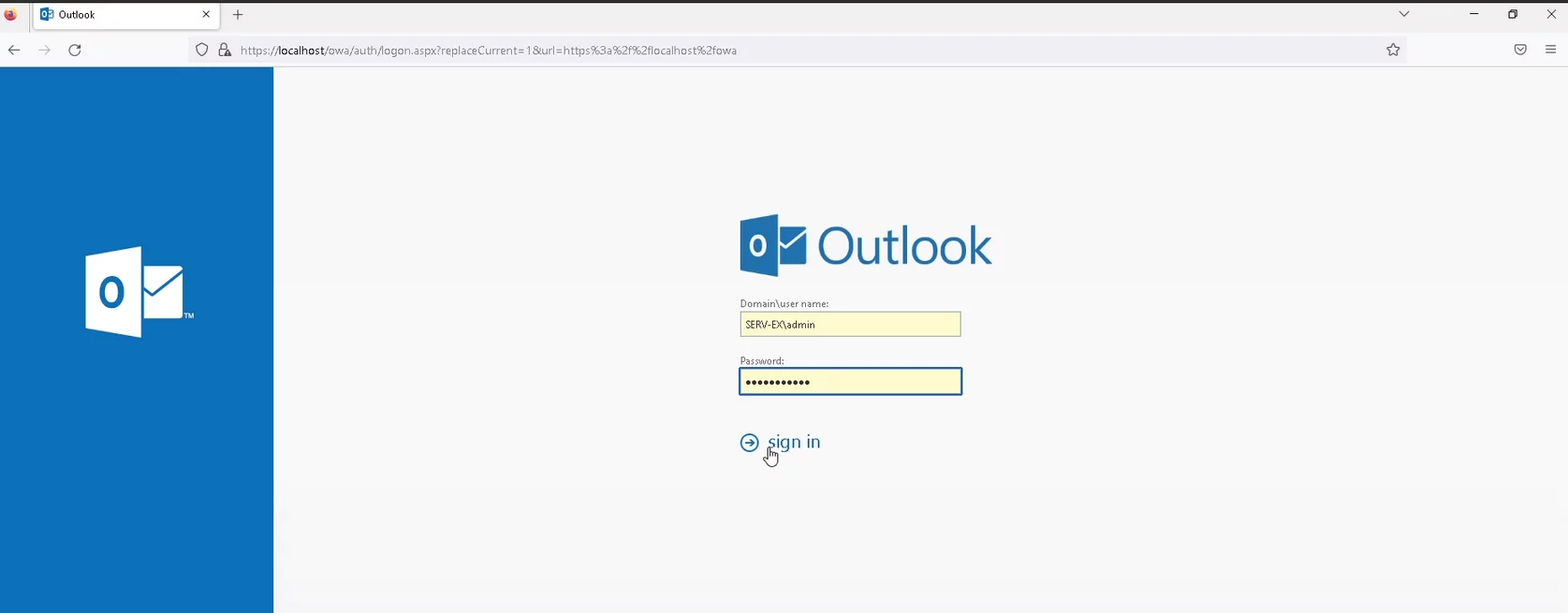
This guide shows how you can set up Outlook Web App two-factor authentication (OWA 2FA) using the Protectimus Cloud MFA service or Protectimus On-Premise MFA Platform.
Adding multi-factor authentication to the Outlook Web App protects users’ accounts from unauthorized access and such hacking attacks as brute force, data spoofing, phishing, social engineering, keyloggers, etc.
ATTENTION! .NET Framework 4.7.x is required.
PLEASE NOTE! An SSL certificate trusted on your network must be used to integrate OWA with the On-Premise Platform. An auto-generated certificate created during installation cannot be accepted by the Exchange Server. We recommend using a certificate issued by AD CS via certsrv.
ATTENTION! Users in the Protectimus system must have logins in the format user@domain or DOMAIN\user. For more details on the user login format, refer to section 5. Username Format Configuration.
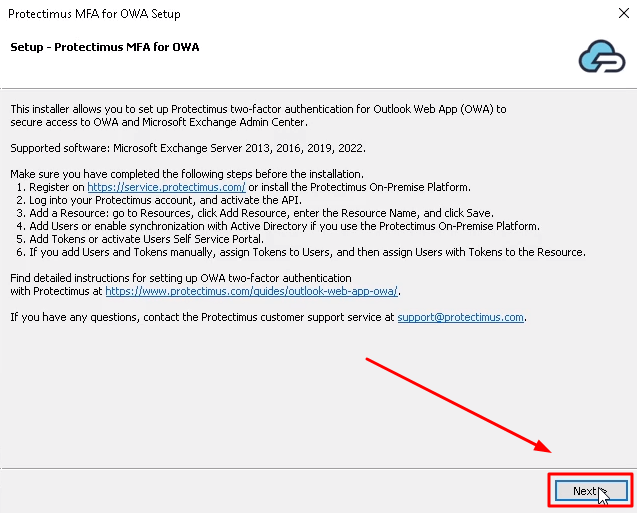
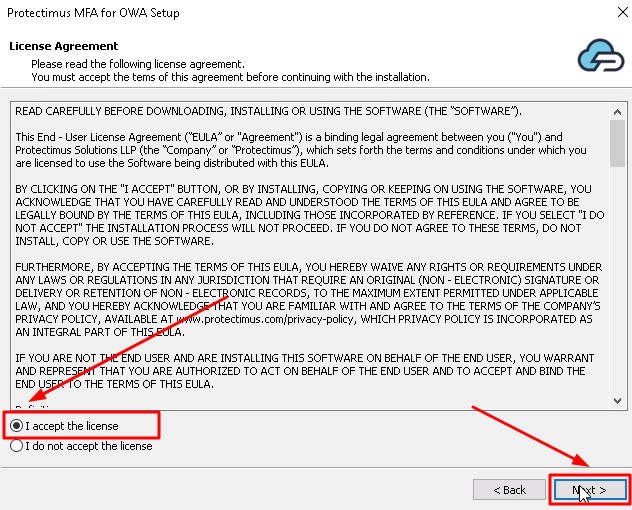
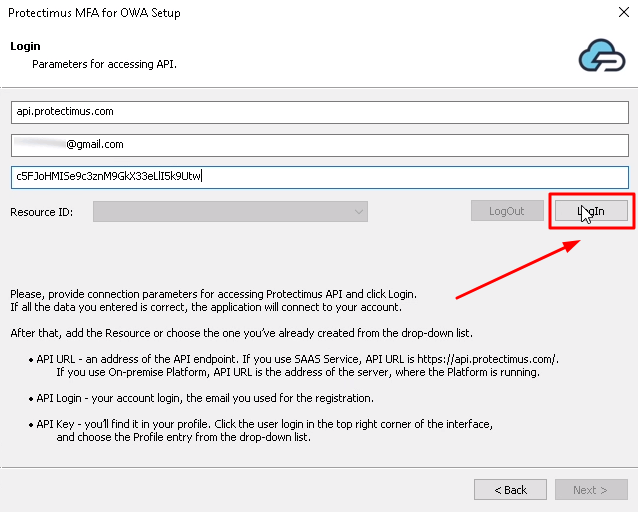
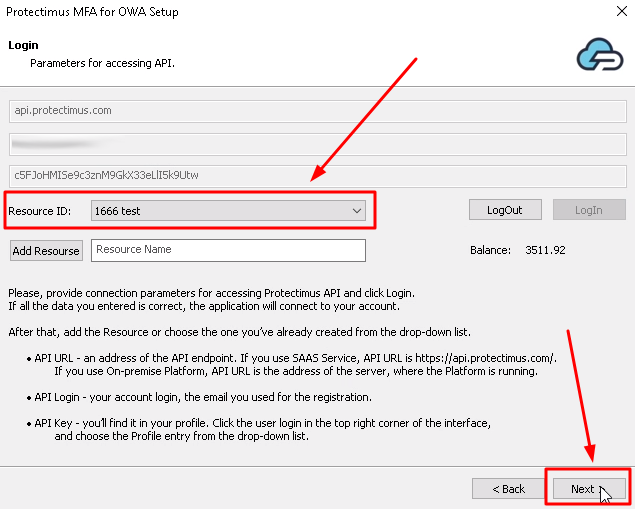
If you haven’t added the resource yet, add it now. Click Add Resource and enter any Resource Name you wish.
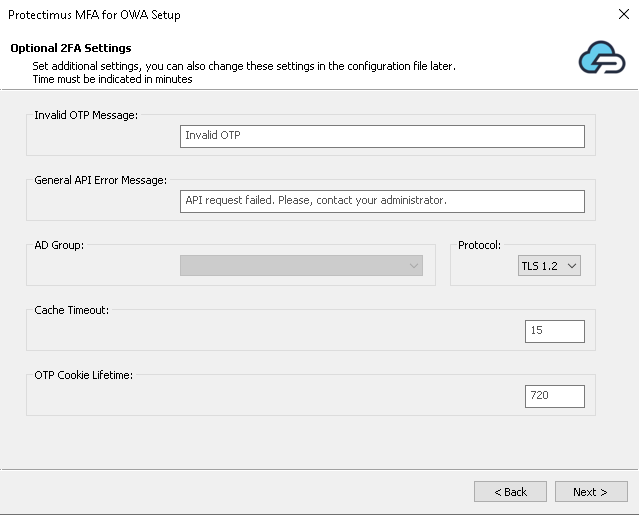
PLEASE NOTE! You can also change these settings in the configuration file later.
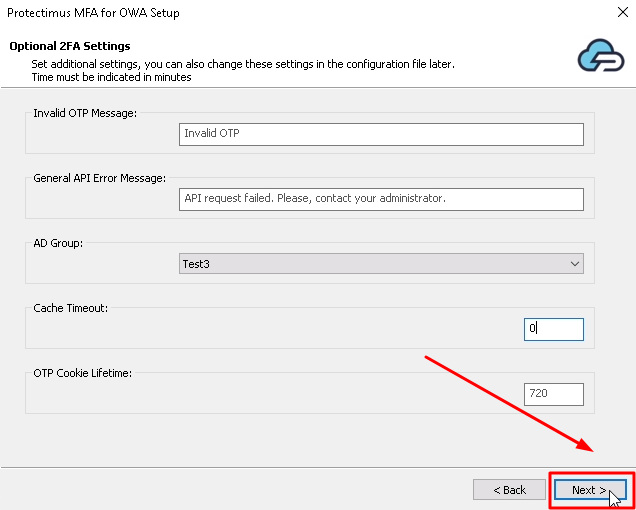
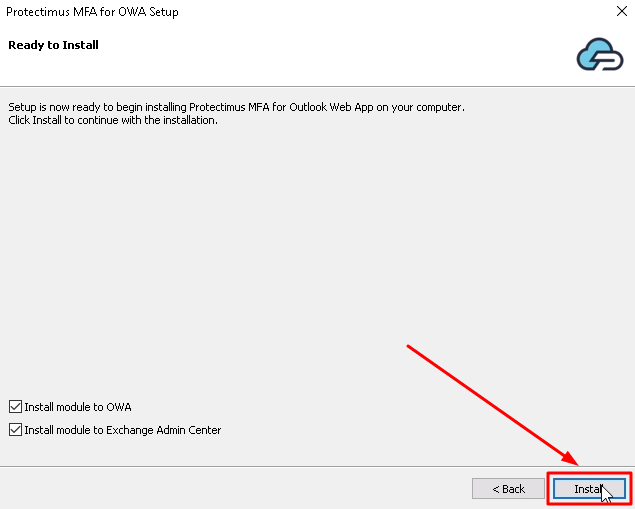
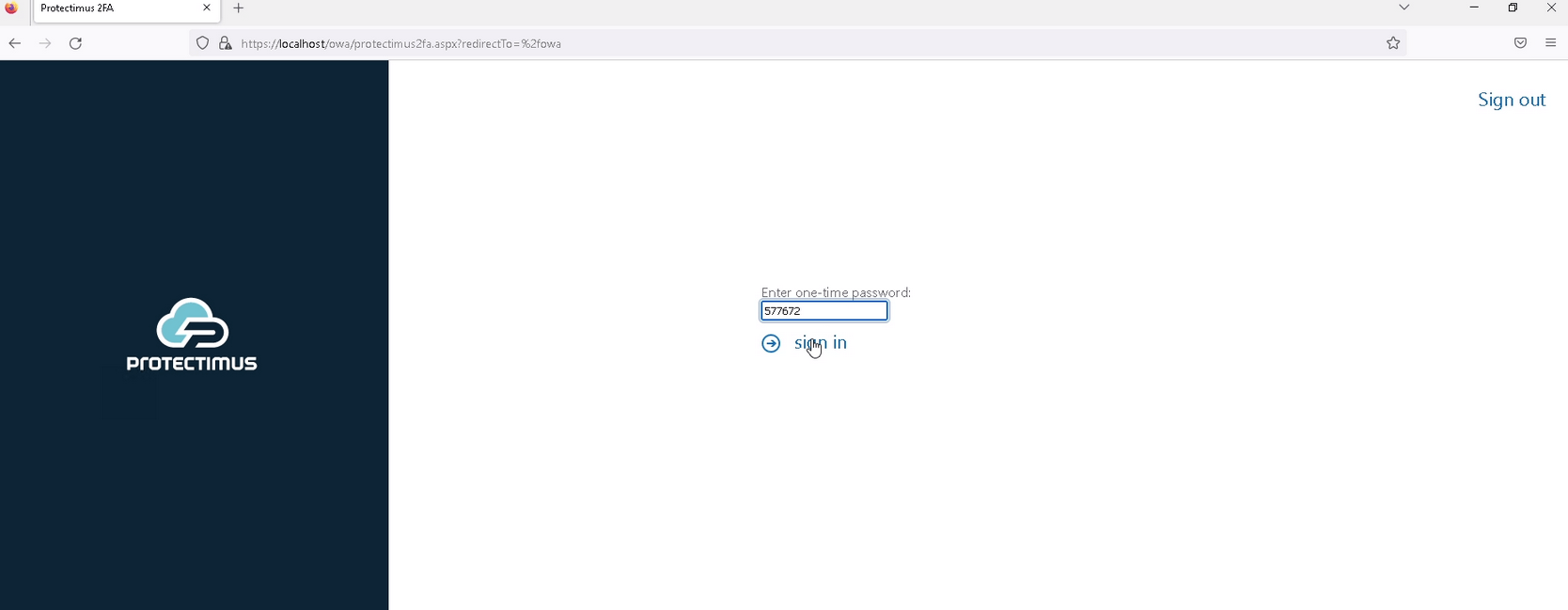
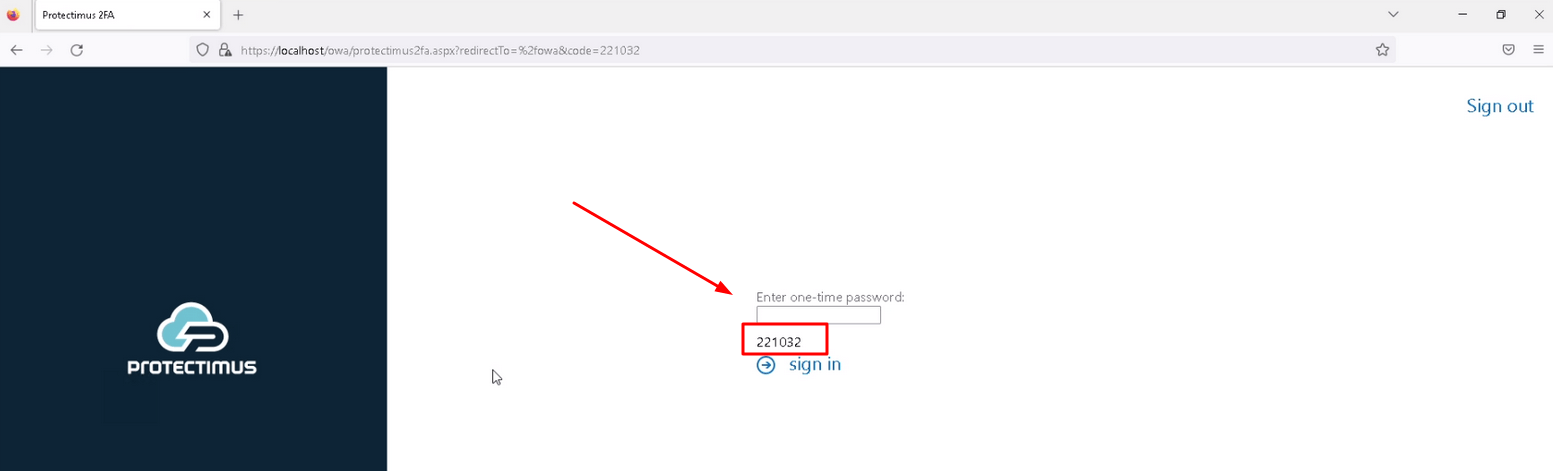
PLEASE NOTE! If you use an OCRA token, use the challenge you will see on the authentication page to generate a one-time password.
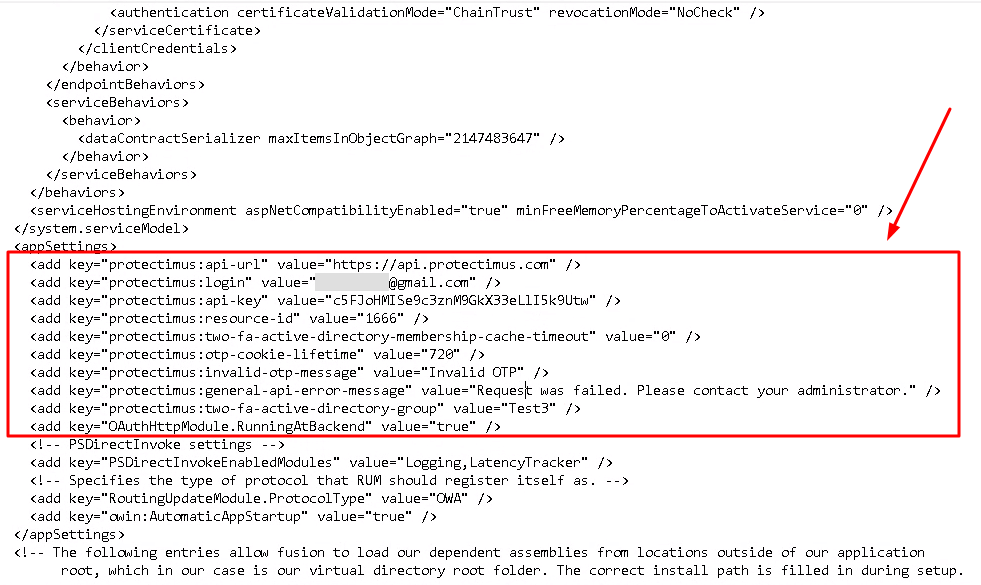
You can change any settings, including API URL, API key, Resource ID, Group settings and other optional settings, in the config file.
The configuration file is usually located at the following path:
C:\Program Files\Microsoft\Exchange Server\V15\ClientAccess\Owa
The user login in the Protectimus service should be in the format of user@domain or DOMAIN\user, where user is the username in AD, and domain is your corporate domain.
To transmit the user login in the desired format to the API, you can use the following parameter in the configuration file:
<add key="protectimus:is-owa-old-format" value="true" />The protectimus:is-owa-old-format parameter can have two values: true or false.
| PARAMETER VALUE | FUNCTION |
|
When the user enters the login in the format DOMAIN\user (netBiosName), the login is converted to the user@domain format (UserPrincipalName). |
|
When the user enters the login in the format user@domain, the login is converted to the DOMAIN\user format. |
|
The user’s login, entered during login, is transmitted to the API in its original format. |
Additionally, the user can enter the login in the format user@domain if the value is set to true, or DOMAIN\user if the value is set to false. In this case, no conversion will be performed as the login is already in the “correct” format.
If you have other questions, contact Protectimus customer support service.
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ireland: +353 19 014 565
USA: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ireland: +353 19 014 565
USA: +1 786 796 66 64


