Программируемый TOTP-токен в формате карты, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой SHA-1
Программируемый TOTP-токен в формате брелока, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой алгоритма SHA-256
Программируемый TOTP-токен в формате карты, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой SHA-1
Программируемый TOTP-токен в формате брелока, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой алгоритма SHA-256
Бесплатное 2FA-приложение с облачным бэкапом, удобным переносом токенов на новый телефон, PIN-кодом и биометрической защитой
Бесплатная доставка OTP с помощью чат-ботов в мессенджерах
Доставка одноразовых паролей через SMS
Бесплатная доставка OTP на email
Бесплатная доставка одноразовых паролей через push-уведомления
Бесплатное 2FA-приложение с облачным бэкапом, удобным переносом токенов на новый телефон, PIN-кодом и биометрической защитой
Бесплатная доставка OTP с помощью чат-ботов в мессенджерах
Доставка одноразовых паролей через SMS
Бесплатная доставка OTP на email
Бесплатная доставка одноразовых паролей через push-уведомления
Guides
Please Note:Prerequisites:
- The certificate of Certification Authority (CA) has to be installed on the clients machines in your domain to integrate the On-Premise Platform with such solutions as OWA.
- The Common Name (CN) for which the certificate was issued has to be accessible in your domain to integrate the On-Premise Platform with such solutions as OWA.
- AD CS installed with Web Enrollment feature.
- You need to have access to the Web Server template in certsrv.
- Keytool and OpenSSL tools are required.
openssl genrsa -out test-server.key 2048Copyopenssl req -new -key test-server.key -out test-server.csrCopyhttp://CA-Server-Name/certsrvCopy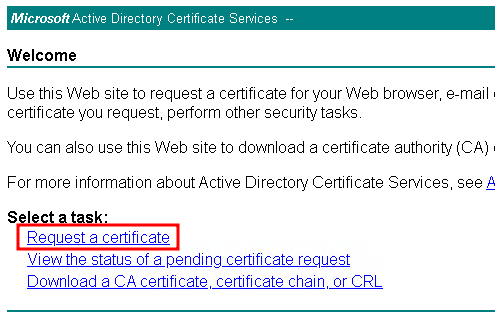
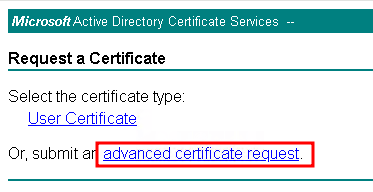
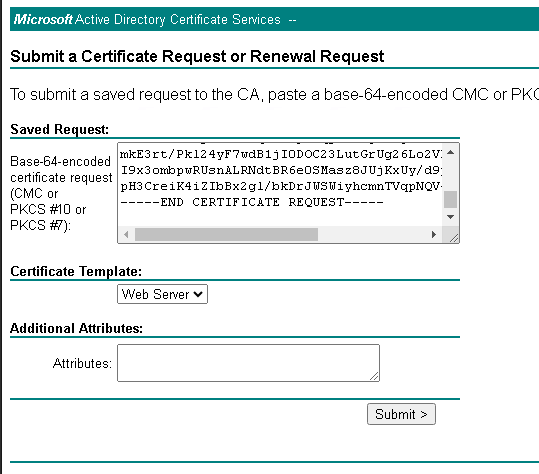
openssl pkcs12 -export -in test-server.cer -inkey test-server.key -out test-server.pfxCopykeytool -importkeystore -srckeystore test-server.pfx -srcstoretype PKCS12 -destkeystore “C:\Program Files\Protectimus\Platform\keystore.jks” -deststoretype JKSCopy| PROPERTY NAME | PROTERTY STANDS FOR |
|
Port on which your application listens for HTTPS requests. Typically, platform uses port 8443 by default. |
|
Type of keystore used to store SSL certificates and private keys. Types: JKS, PKCS12. |
|
Password required to access the keystore. |
|
Full path to the keystore file containing SSL certificates and private keys. Please note that the keystore file should be located in the ..\\Protectimus\\Platform folder, in the same place as the .war and .properties files. The path should be indicated with double backslashes, for example C:\\Program Files\\Protectimus\\Platform\\keystore.jks. |
https.port = 8443
https.keystore.type = JKS
https.keystore.password = **********
https.keystore = C:\\Program Files\\Protectimus\\Platform\\keystore.jksCopy| PROPERTY NAME | PROTERTY STANDS FOR |
|
SMTP server’s hostname or IP address. |
|
Port number for SMTP server. |
|
Username or email account for authentication. |
|
Password associated with the username or email account. |
|
Allows you to set the address from which emails will be sent to the user. |
smtp.host = smtp-server.com
smtp.port = 25
smtp.user = user@example.com
smtp.password = **********CopyPLEASE NOTE! Additionally, you can configure settings for SMSC and ALIBABA as well.
| PROPERTY NAME | PROTERTY STANDS FOR |
|
SMPP server login. |
|
SMPP server password. |
|
Host or IP address of the SMPP server. |
|
Port for the SMPP server. |
|
Encoding for SMPP messages. |
|
Source or sender address for SMPP messages. |
smpp.server.login = login
smpp.server.password = **********
smpp.server.host = smpp.example.com
smpp.server.port = 12000
smpp.message.encoding = UTF-8
smpp.from.address = ProtectimusCopyProtectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ирландия: +353 19 014 565
США: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ирландия: +353 19 014 565
США: +1 786 796 66 64


