Программируемый TOTP-токен в формате карты, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой SHA-1
Программируемый TOTP-токен в формате брелока, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой алгоритма SHA-256
Программируемый TOTP-токен в формате карты, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой SHA-1
Программируемый TOTP-токен в формате брелока, совместимый с любой системой аутентификации
Классический аппаратный TOTP токен с поддержкой алгоритма SHA-256
Бесплатное 2FA-приложение с облачным бэкапом, удобным переносом токенов на новый телефон, PIN-кодом и биометрической защитой
Бесплатная доставка OTP с помощью чат-ботов в мессенджерах
Доставка одноразовых паролей через SMS
Бесплатная доставка OTP на email
Бесплатная доставка одноразовых паролей через push-уведомления
Бесплатное 2FA-приложение с облачным бэкапом, удобным переносом токенов на новый телефон, PIN-кодом и биометрической защитой
Бесплатная доставка OTP с помощью чат-ботов в мессенджерах
Доставка одноразовых паролей через SMS
Бесплатная доставка OTP на email
Бесплатная доставка одноразовых паролей через push-уведомления
Инструкции
Решение двухфакторной аутентификации Protectimus RADIUS 2FA подходит для защиты любого программного обеспечения или оборудования, которое поддерживает протокол аутентификации RADIUS.
Коннектор Protectimus RADIUS Server работает как RADIUS сервер. Он передает запросы аутентификации от устройства или ПО, ктоторое подключено к Protectimus RADIUS Server по протоколу RADIUS, на сервер многофакторной аутентификации (MFA) Protectimus и возвращает ответ с разрешением или запретом доступа.
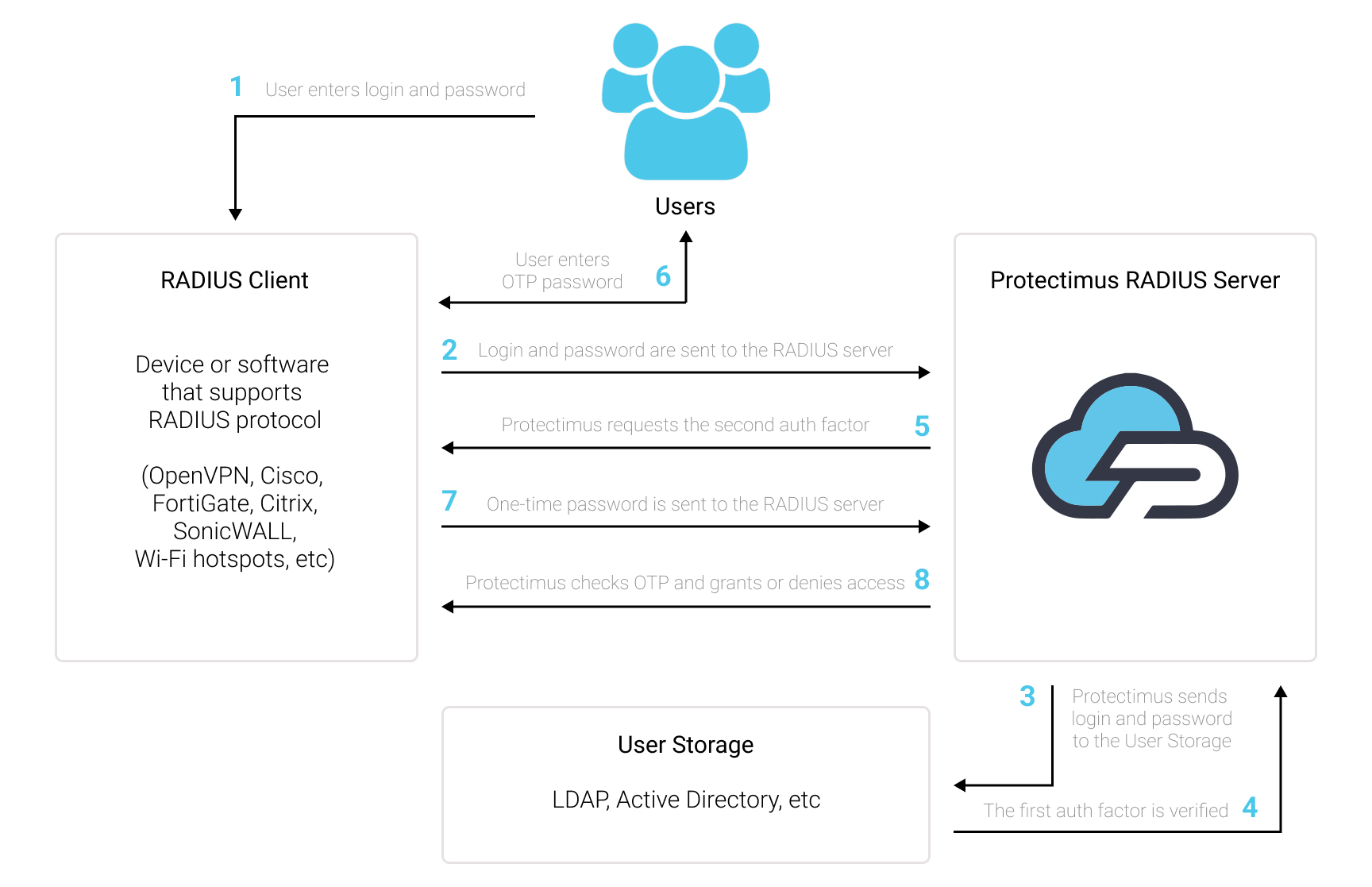
Подключите двухфакторную аутентификацию (2FA/MFA) к VPN, Wi-Fi и любому другому программному обеспечению или девайсу, поддерживающему RADIUS аутентификацию и защитите доступ к учетным записям пользователей от несанкционированного доступа. Для этого выполните интеграцию с Облачным сервисом двухфакторной аутентификации или Локальной платформой MFA Protectimus через протокол аутентификации RADIUS.
Список программного обеспечения и устройств, которые можно интегрировать с Protectimus по протоколу аутентификации RADIUS, включает, но не ограничивается:
Программное обеспечение Protectimus RADIUS 2FA легко настроить и интегрировать с вашей системой. Но если у вас возникнут вопросы, наша команда всегда готова помочь с интеграцией двухфакторной аутентификации (2FA) по RADIUS даже в самую сложную инфраструктуру. Просто свяжитесь с нашей службой поддержки.
Чтобы интегрировать решение Protectimus 2FA с устройством или программным обеспечением, поддерживающим RADIUS, необходимо установить и настроить Protectimus RADIUS Server, а затем настроить политики аутентификации на устройстве или в приложении, которое вы хотите интегрировать с Protectimus:
- Вы разрешаете передачу запроса на аутентификацию через протокол RADIUS на Protectimus RADIUS Server;
- Protectimus RADIUS Server принимает и обрабатывает этот запрос;
- Далее Protectimus RADIUS Server обращается к серверу аутентификации Protectimus для проверки одноразового пароля от пользователя.
docker-compose up -ddocker-compose logs -fВНИМАНИЕ!
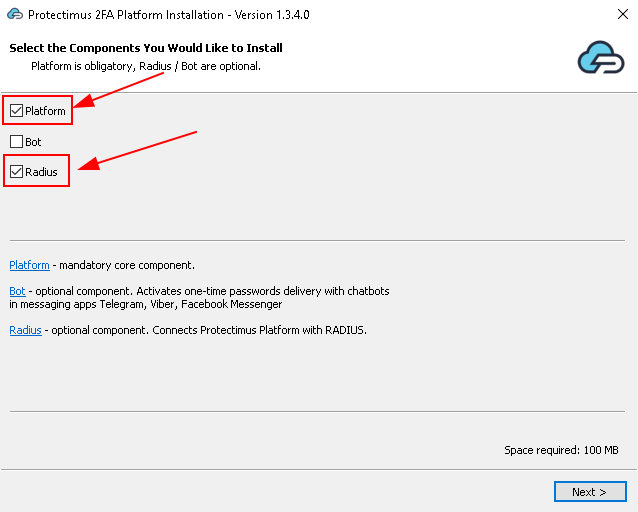
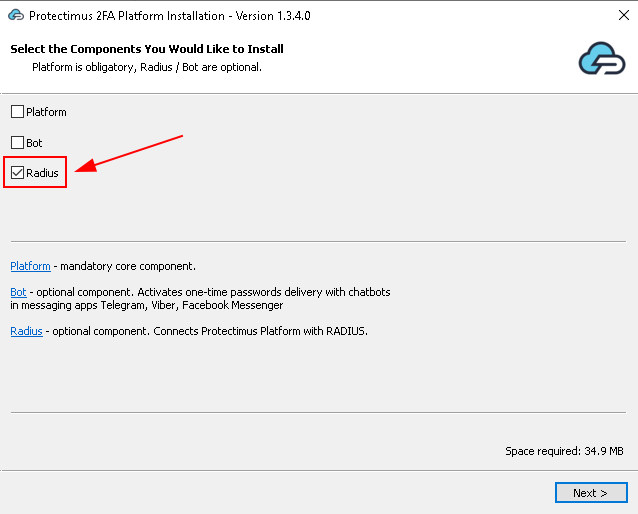
Если вы планируете использовать локальную платформу Protectimus, выберите пункт Platform.
Если вы планируете использовать облачный сервис Protectimus, снимите галочку с пункта Platform.
Если вы планируете использовать
|
Если вы планируете использовать
|
 |
 |
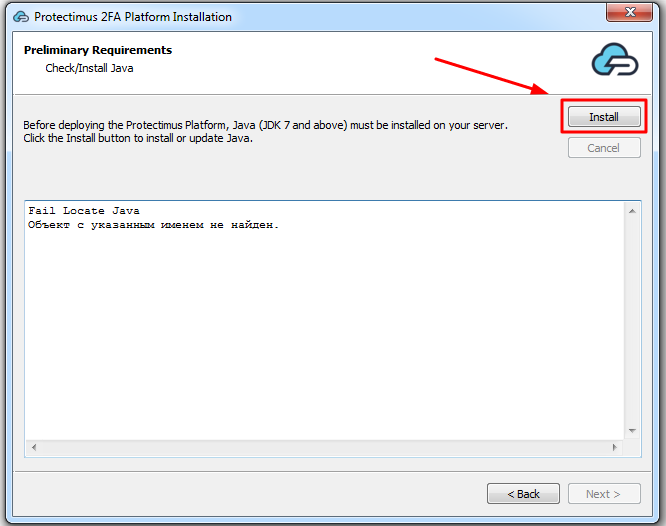
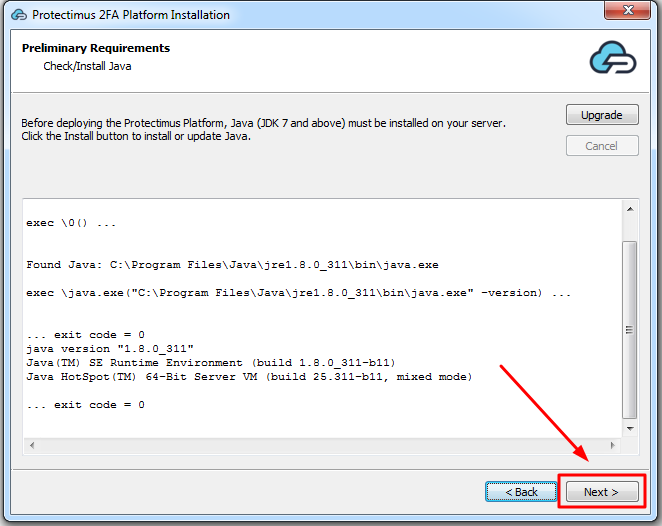
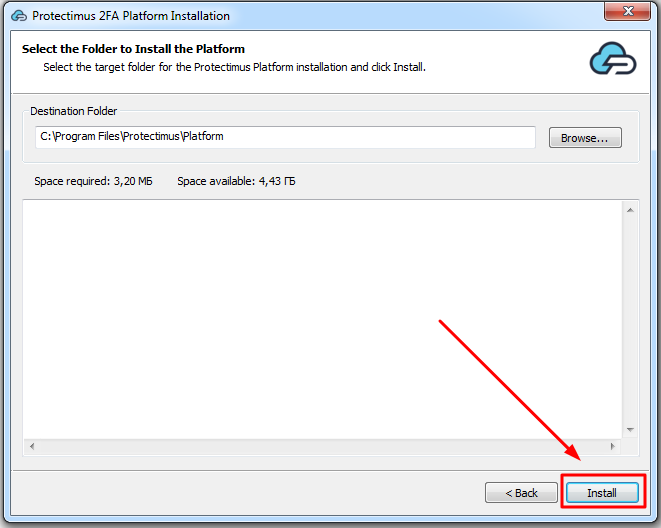
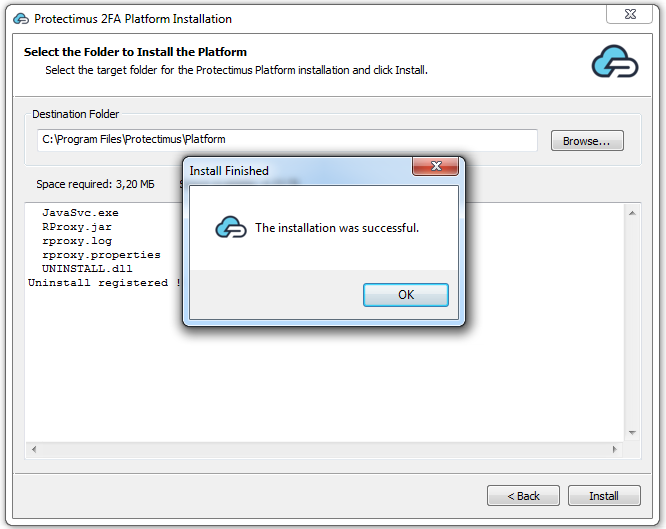
Конфигурирование Protectimus RADIUS Server выполняется путём задания настроек в файле radius.yml, который должен быть расположен в той же папке, что и запускаемый файл.
Задайте в файле radius.yml следующие значения:
auth:
providers:
- LDAP
- PROTECTIMUS_OTP
re-enter-otp: true
principal-normalization: true
bypass-otp:
ldap-filter: (memberOf=cn=bypass-otp,ou=groups,dc=test,dc=com)
usernames:
- john
- luci
inline-mode:
enabled: false
separator: ''
attributes:
NAS-Identifier:
- home-nas
- work-nas
| НАЗВАНИЕ ПАРАМЕТРА | ФУНКЦИЯ ПАРАМЕТРА |
|
Могут быть:
|
|
Когда параметр re-enter-otp активирован, статический пароль не запрашивается после неудачной проверки OTP-пароля. |
|
Когда параметр normalization активирован, любая информация о домене удаляется из имени пользователя, то есть независимо от того, как указано имя пользователя «username», «DOMAIN \ username», или «username@domain.com», оно будет преобразовано в одно «username». |
|
Когда опция bypass-otp включена, для указанных пользователей не требуется ввод одноразового пароля (OTP). |
|
Inline mode позволяет использовать 2FA в случае, когда Access-Challenge не поддерживается. Inline mode можно активировать с помощью ‘enabled: true’ или через соответствующие атрибуты запроса. В этом случае пароль должен быть в следующем формате ‘password,otp’, если используется разделитель: ‘,’. |
radius:
secret: secret
clients:
- name: vpn-client
secret: secret
ips:
- 10.0.0.0/24
auth-port: 1812
listen-address: 0.0.0.0
dictionaries:
- file:<some_path>/<some_name>.dat
attributes:
copy-state: true
defaults:
Service-Type: NAS-Prompt-User
for-users:
john:
Service-Type: Login-User
ldap:
memberOf:
'[cn=admins,ou=groups,dc=test,dc=com]':
Service-Type: Administrative
uid:
john_wick:
Class: Pro
conditional:
'[ldapUser.attributes["uid"] == "john"]':
Service-Type:
- Login-User
'[request.getAttributeValue("User-Name") == "john"]':
Class:
- RDP_HeadOffice_GP
ip-attributes:
- NAS-IP-Address
- NAS-IPv6-Address
| НАЗВАНИЕ ПАРАМЕТРА | ФУНКЦИЯ ПАРАМЕТРА |
|
Секрет, который будет использоваться вашим RADIUS сервером. |
|
Клиенты, использующие уникальные секреты (идентификация клиентов осуществляется по IP-адресу). Каждый клиент ОБЯЗАТЕЛЬНО должен иметь уникальное имя. |
|
Порт на котором будет запущен RADIUS сервер. |
|
IP-адрес, к которому подключается сервер. |
|
Расширение списка атрибутов для протокола RADIUS. Пример подобного списка атрибутов представлен в разделе Пример Dictionary. |
|
Атрибуты, которые будут возвращаться при успешной аутентификации. |
|
Копирует каждый возвращаемый атрибут в ответ. |
|
Aтрибуты для всех пользователей. |
|
Атрибуты для определенных пользователей. |
|
Атрибуты для конкретного пользователя или группы пользователей в LDAP. |
|
Когда параметр conditional активирован, вы можете указать скрипт, который будет проверять условия, при выполнении которых атрибут будет возвращаться. |
|
Атрибуты, которые возвращают IP-адрес входящего запроса, используя указанный атрибут. |
protectimus-api:
login:
api-key:
url: https://api.protectimus.com/
resource-id:| НАЗВАНИЕ ПАРАМЕТРА | ФУНКЦИЯ ПАРАМЕТРА |
|
Ваш логин в системе PROTECTIMUS. |
|
Ваш ключ API в системе PROTECTIMUS. |
|
Если Вы используете облачный сервис PROTECTIMUS, укажите следующий API URL: https://api.protectimus.com/
Если Вы используете on-premise платформу Protectimus, API URL будет выглядеть примерно так: protectimus.api.url=http://127.0.0.1:8080/ |
|
ID ресурса, созданного вами в системе PROTECTIMUS. |
ldap:
base: dc=test,dc=com
urls:
- ldap://127.0.0.1:389
username: admin@test.com
password: secret
principal-attribute: userPrincipalName
custom-filter: (memberof=cn=managers,ou=groups,dc=test,dc=com)
| НАЗВАНИЕ ПАРАМЕТРА | ФУНКЦИЯ ПАРАМЕТРА |
|
LDAP DN группы или подразделения, содержащего всех пользователей, которым вы хотите разрешить вход. |
|
Имя хоста или IP-адрес вашего контроллера домена. |
|
Используется для LDAP аутентификации по определенному атрибуту.
Если вы хотите аутентифицировать пользователя с помощью «sAMAccountName» вместо «userPrincipalName», укажите атрибуты «query-attribute» и «principal-attribute» соответственно. |
|
Используется для определения, какие пользователи имеют право проходить аутентификацию. |
proxy:
secret: secret
auth-port: 1812
remote-address: 192.168.1.1| НАЗВАНИЕ ПАРАМЕТРА | ФУНКЦИЯ ПАРАМЕТРА |
|
Секрет, который будет использоваться сервером RADIUS_PROXY. |
|
Порт на котором будет запущен RADIUS сервер. |
|
IP-адрес сервера PROXY_RADIUS. |
ad:
urls:
- ldap://127.0.0.1:389
domain: test.com
radius:
secret: secret
clients:
- name: vpn-client
secret: secret
ips:
- 10.0.0.0/24
auth-port: 1812
listen-address: 0.0.0.0
dictionaries:
- file:/.dat
attributes:
copy-state: true
defaults:
Service-Type: NAS-Prompt-User
for-users:
john:
Service-Type: Login-User
ldap:
memberOf:
'[cn=admins,ou=groups,dc=test,dc=com]':
Service-Type: Administrative
uid:
john_wick:
Class: Pro
conditional:
'[ldapUser.attributes["uid"] == "john"]':
Service-Type:
- Login-User
'[request.getAttributeValue("User-Name") == "john"]':
Class:
- RDP_HeadOffice_GP
ip-attributes:
- NAS-IP-Address
- NAS-IPv6-Address
auth:
providers:
- LDAP
- AD
- PROTECTIMUS_PASSWORD
- PROTECTIMUS_OTP
- RADIUS_PROXY
bypass-otp:
ldap-filter: (memberOf=cn=bypass-otp,ou=groups,dc=test,dc=com)
usernames:
- john
- luci
ips:
- 10.0.0.0/24
- 1::/64
re-enter-otp: true
principal-normalization: true
inline-mode:
enabled: false
separator: ''
ldap:
base: dc=test,dc=com
urls:
- ldap://127.0.0.1:389
username:
password:
principal-attribute: userPrincipalName
custom-filter: (memberof=cn=managers,ou=groups,dc=test,dc=com)
ad:
urls:
- ldap://127.0.0.1:389
domain: test.com
protectimus-api:
login: test@protectimus.com
api-key: secret
url: https://api.protectimus.com/
resource-id: 1
proxy:
secret: secret
auth-port: 1812
remote-address: 192.168.1.1
VENDOR 12356 fortinet
VENDORATTR 12356 Fortinet-Group-Name 1 string
VENDORATTR 12356 Fortinet-Access-Profile 6 string
Теперь вам нужно настроить ваше устройство или приложение для связи с Protectimus RADIUS Server по протоколу RADIUS.
Если у вас есть другие вопросы, свяжитесь с нашей службой поддержки клиентов.
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ирландия: +353 19 014 565
США: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ирландия: +353 19 014 565
США: +1 786 796 66 64


