Programmable TOTP token that fits any authentication system
Classic SHA-1 TOTP hardware token: high-strength and water-resistant
Programmable hardware TOTP token in a key fob format
Апаратний TOTP токен з можливістю програмування у формі брелока
Classic hardware TOTP token with SHA-256 algorithm support
Free 2FA app for iOS and Android with encrypted cloud backup, PIN, and biometric protection
OTP delivery via messenger — easy, secure, convenient. The service is available on Telegram, Viber and Facebook Messenger
Delivery of one-time passwords via SMS messages
Free delivery of one-time passwords via email
Free one-time password delivery through push notifications in the Protectimus Smart 2FA app - simply press a button to confirm your login
The Protectmus DSPA (Dynamic Strong Password Authentication) component allows integrating Protectimus two-factor authentication solution with Microsoft Active Directory or any other user directory (AD/LDAP, DBMS). After that, the 2FA dynamic passwords will be requested on all services connected to this directory (for example on Winlogon, RDP, ADFS, and OWA at once).
Protectimus DSPA adds six-digit time-based one-time passwords onto users’ static passwords. The resulting passwords look somehow like this: P@ssw0rd!459812. Where:
- P@ssw0rd! is the fixed part;
- 459812 is a TOTP one-time password that changes within a set time interval.
The administrator sets the one-time password change interval, which must be a multiple of 30 seconds.
From the end-user side, authentication will look like this: to access their accounts, a user must enter their fixed password and a one-time code in one line. To generate OTPs, users should use the app Protectimus SMART.
Get the Protectimus On-Premise Platform Windows installer to start the setup process.
The Protectimus DSPA component will be installed automatically.
Install the Protectimus On-Premise Platform using the Docker image. Refer to our step-by-step Docker installation instructions to get started.
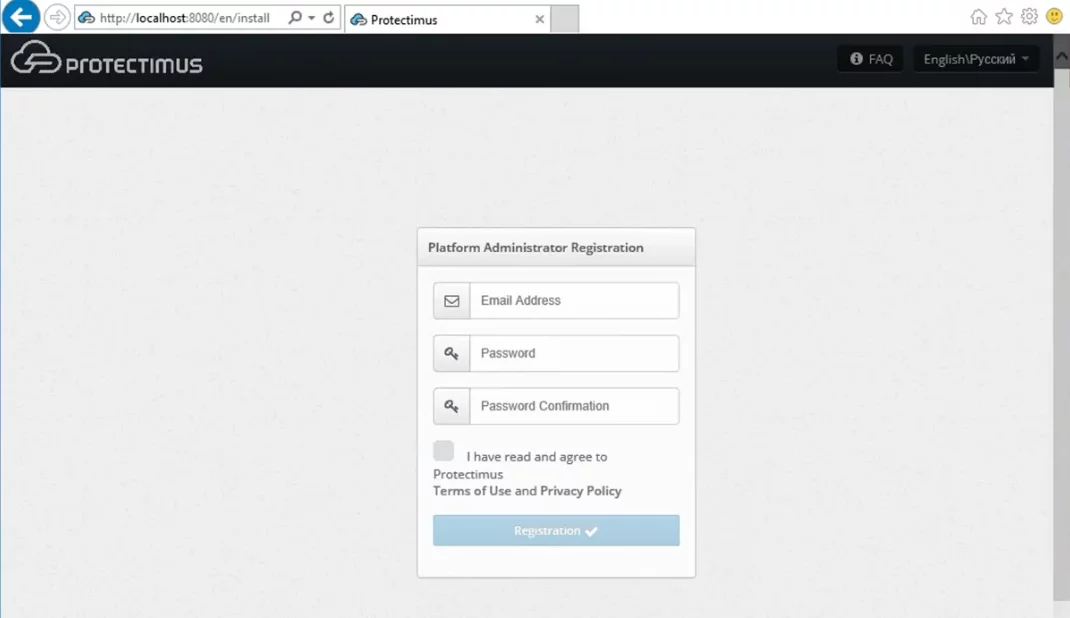
The Protectimus On-Premise Platform installer will automatically open the registration form at
http://localhost:8080.
Please, create an account and log in to configure the necessary settings.
Basic settings:
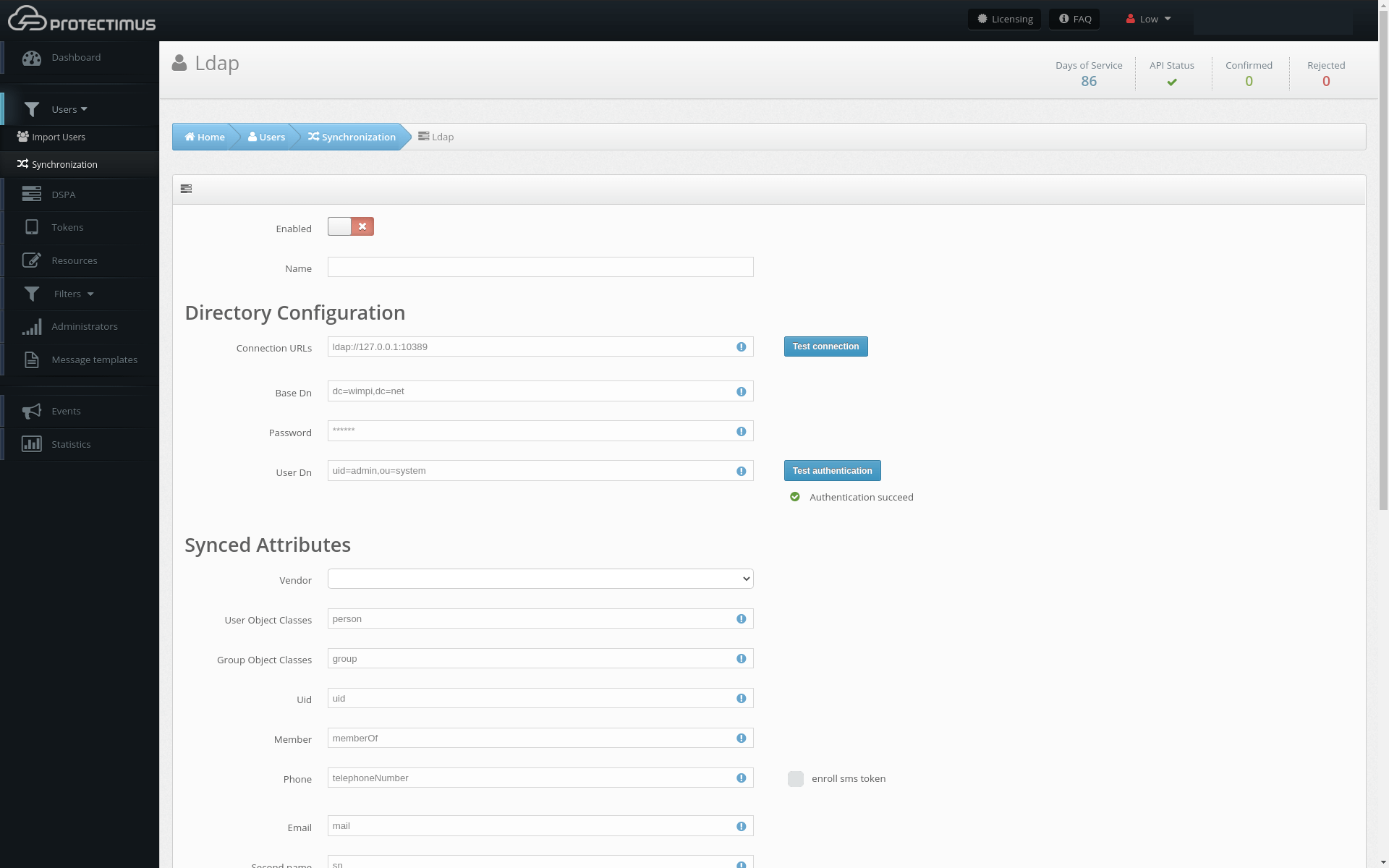
| Field | Value | Note |
| Urls | URL to connect to your LDAP server |
Example:
ldaps://dc1.domain.local:636
A standard way: keytool -import -alias ___ -file '___.cer' -keystore 'C:\Program Files\Java\jre___\lib\security\cacerts' -storepass changeit
|
| Base DN | Full DN of the directory in which your users are stored |
Example:
DC=domain,DC=local
|
| User Dn | DN of the administrator or user who has access to user information |
Example:
CN=Administrator, CN=Users, DC=demo, DC=domain, DC=local
The user must have rights to change passwords |
| Password | The password of the specified user | |
| Filter | A filter to be applied during synchronization |
Use this filter to select only the users you want to synchronize Example: (memberOf=CN=DSPA Group, DC=domain, DC=local)
(mail=*)
|
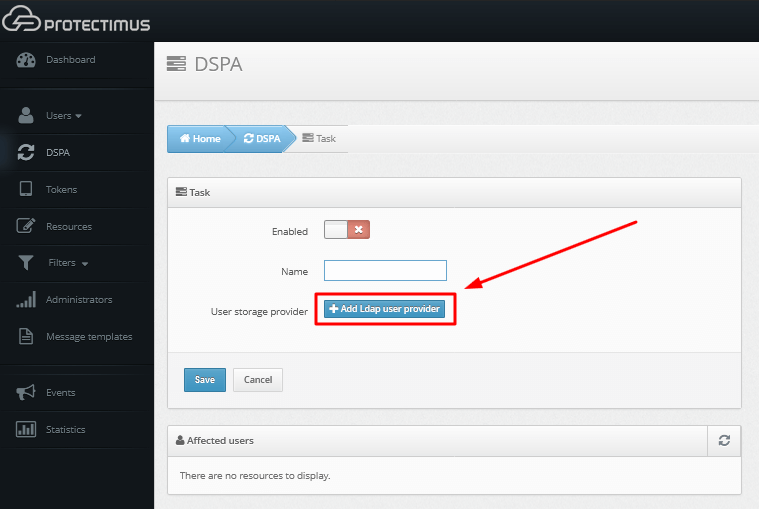
After successfully adding the user provider, you need to synchronize the users in Protectimus system with your user directory.
This can be done in three ways:
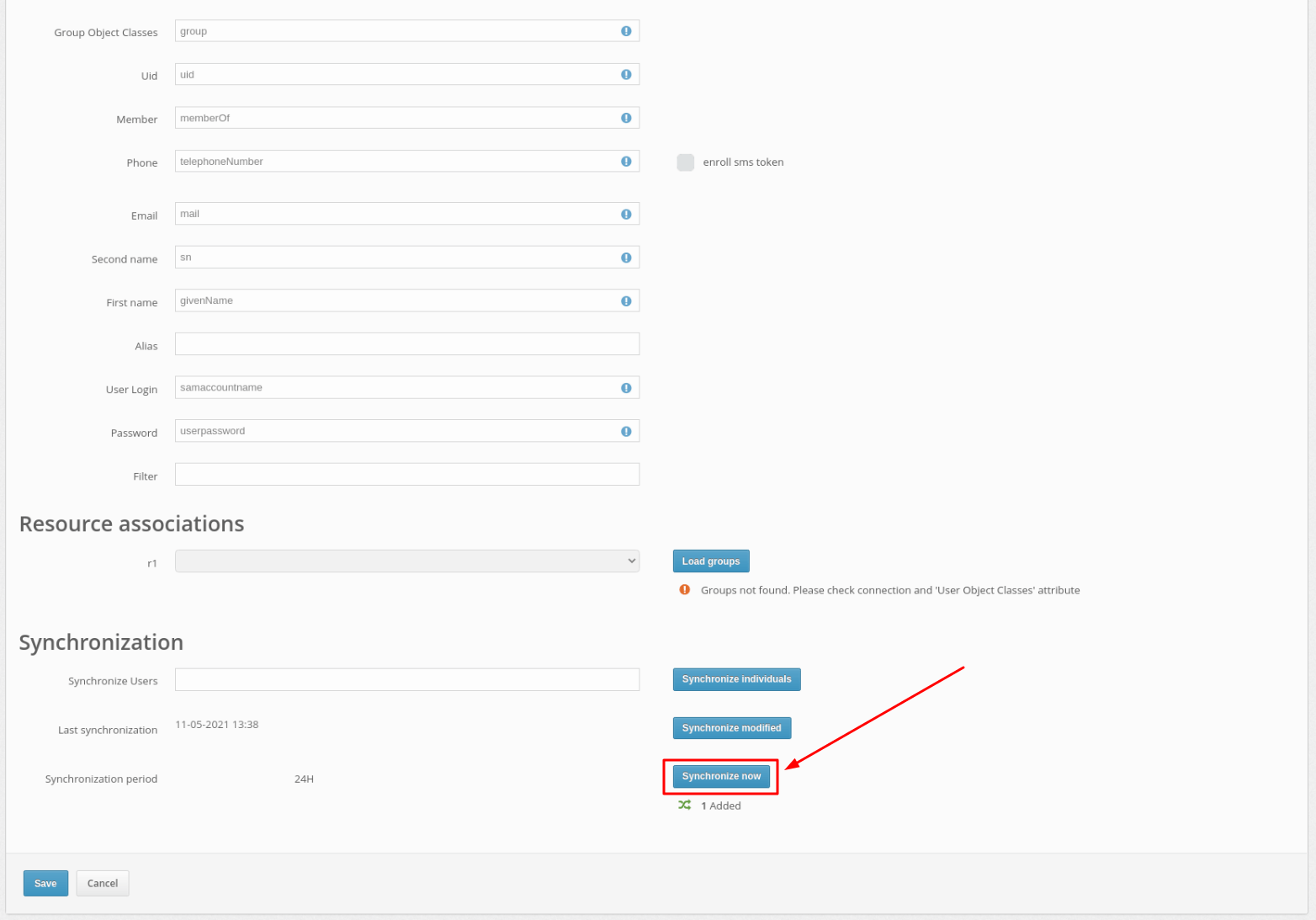
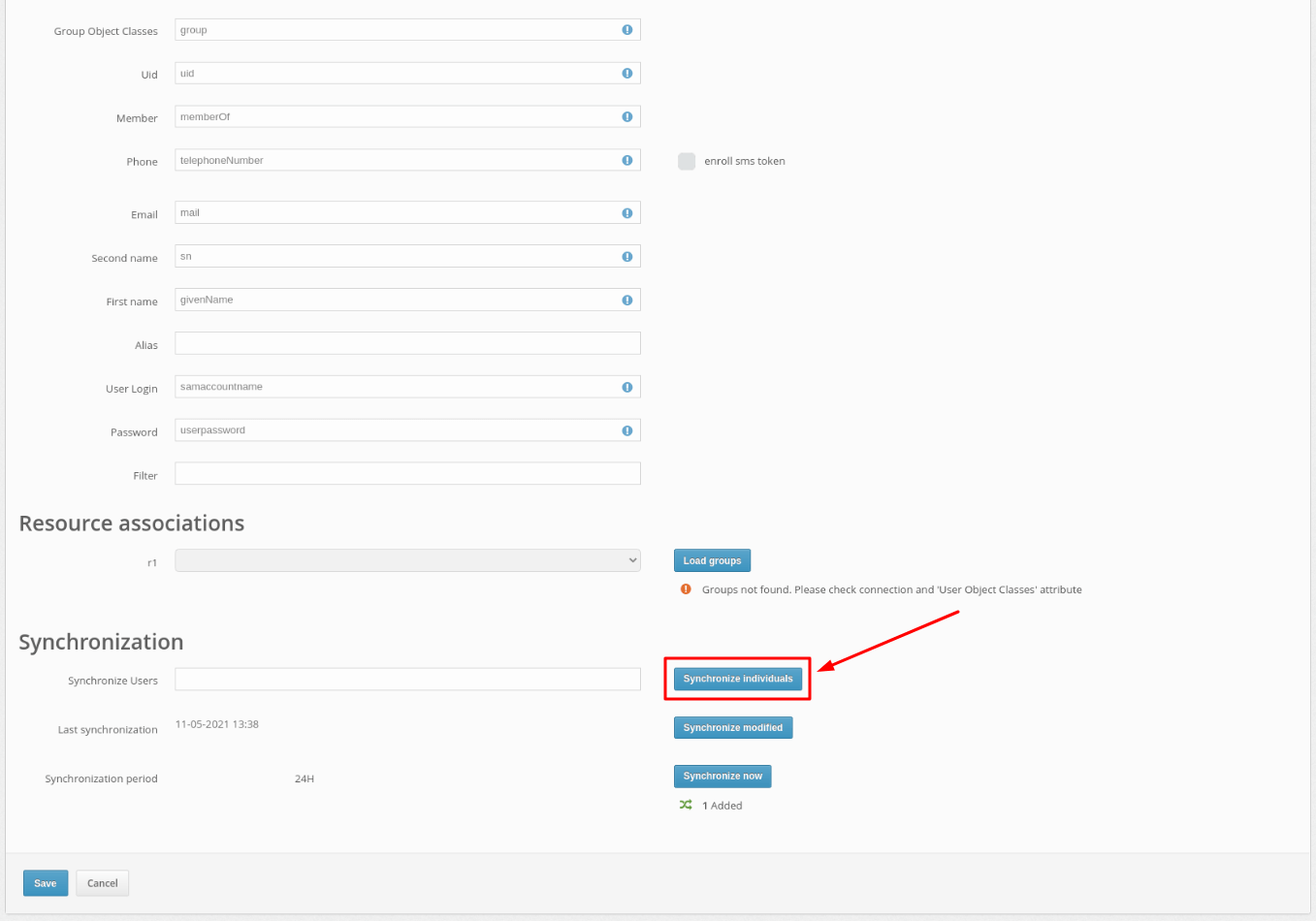
PLEASE NOTE! You can activate the Users’ Self-Service Portal so that your users could add their passwords to the system themselves. Read how to set up a Users’ Self-Service Portal in the Users’ Self-Service Portal Setup Instructions.
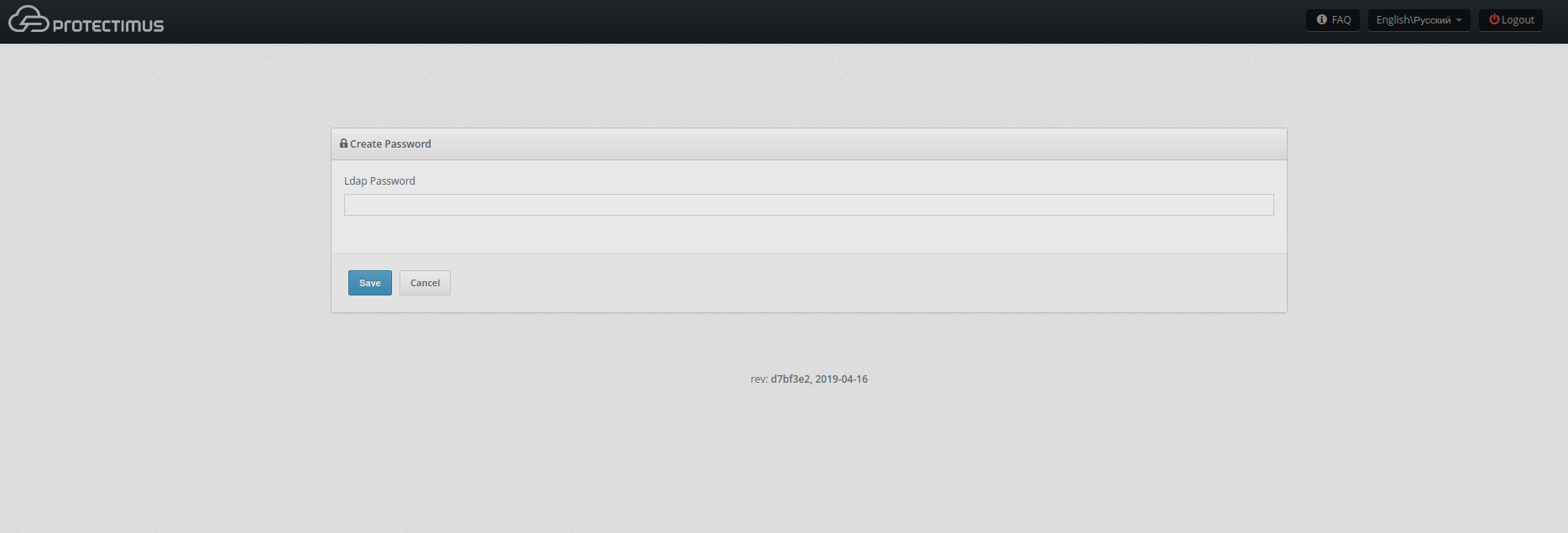
If you prefer to set a password for a user manually:
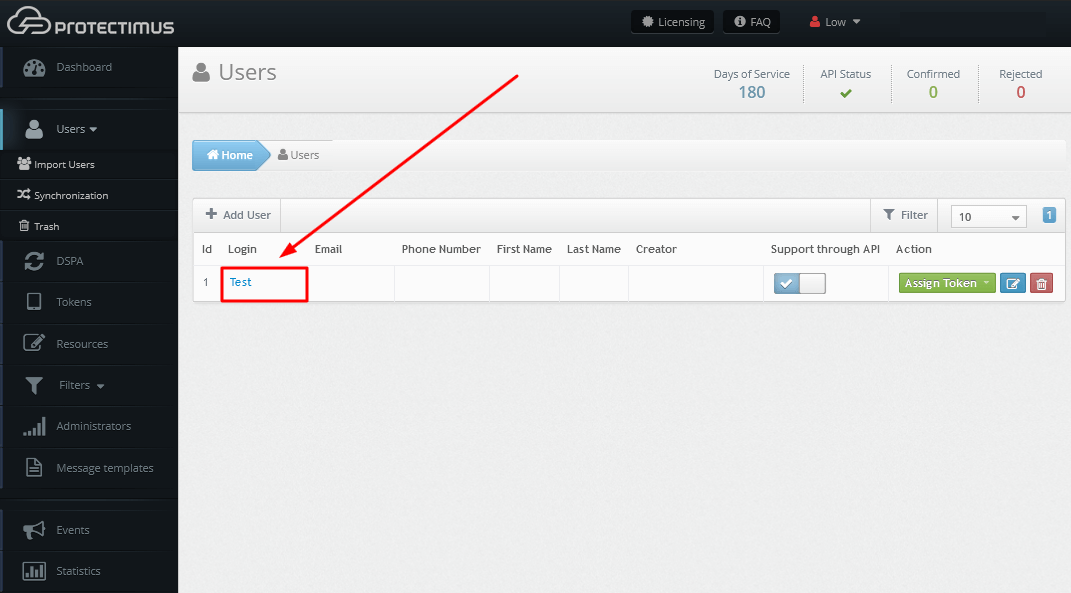
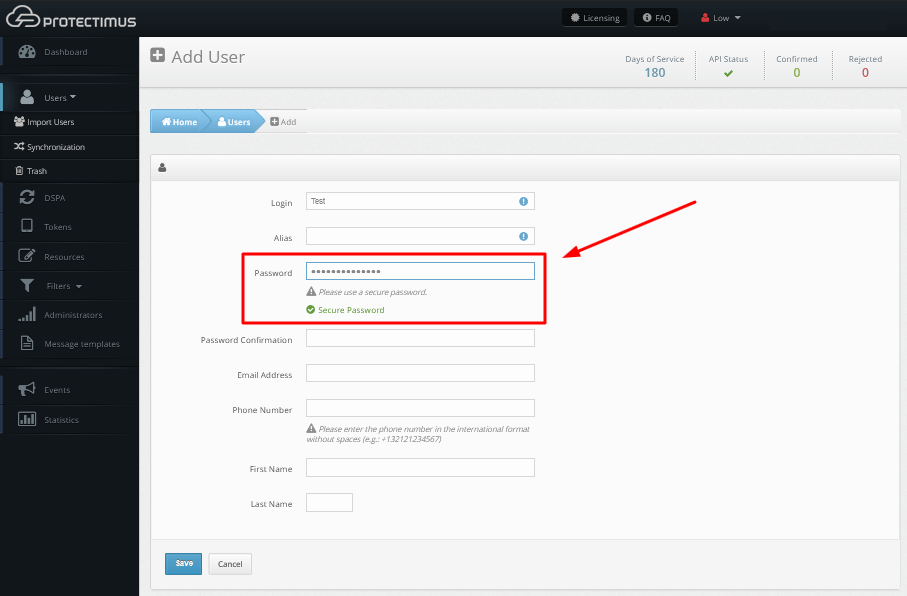
So far, the Protectimus DSPA component is only compatible with the in-app 2FA tokens Protectimus Smart OTP, available on iOS and Android, therefore we recommend activating the User Self-Service Portal so that your end users could issue tokens on their own. Read our Self-Service Portal Setup Guide for detailed instructions.
If you prefer to add tokens to uers manually:
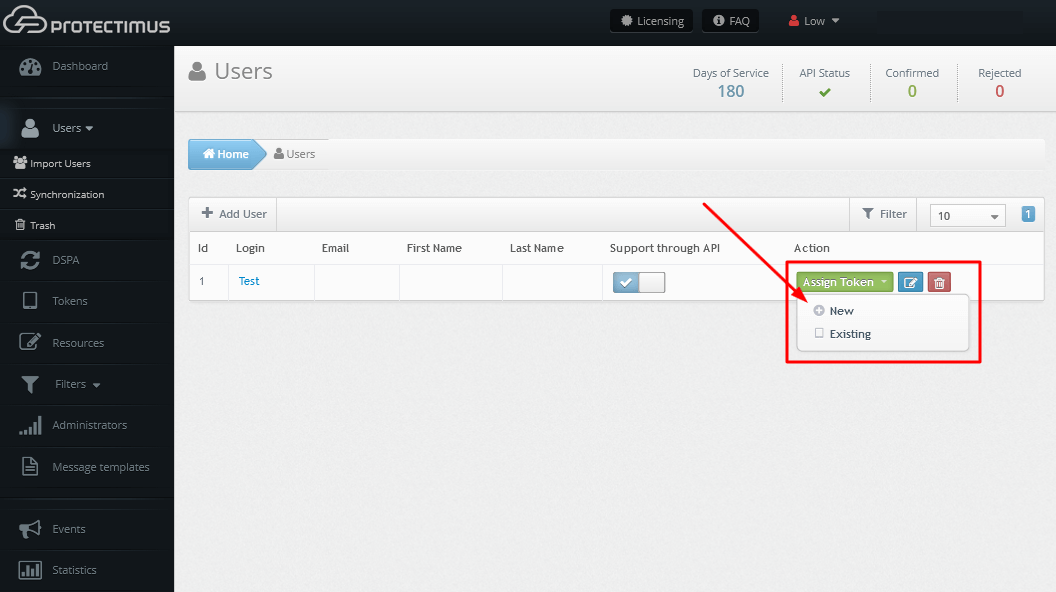
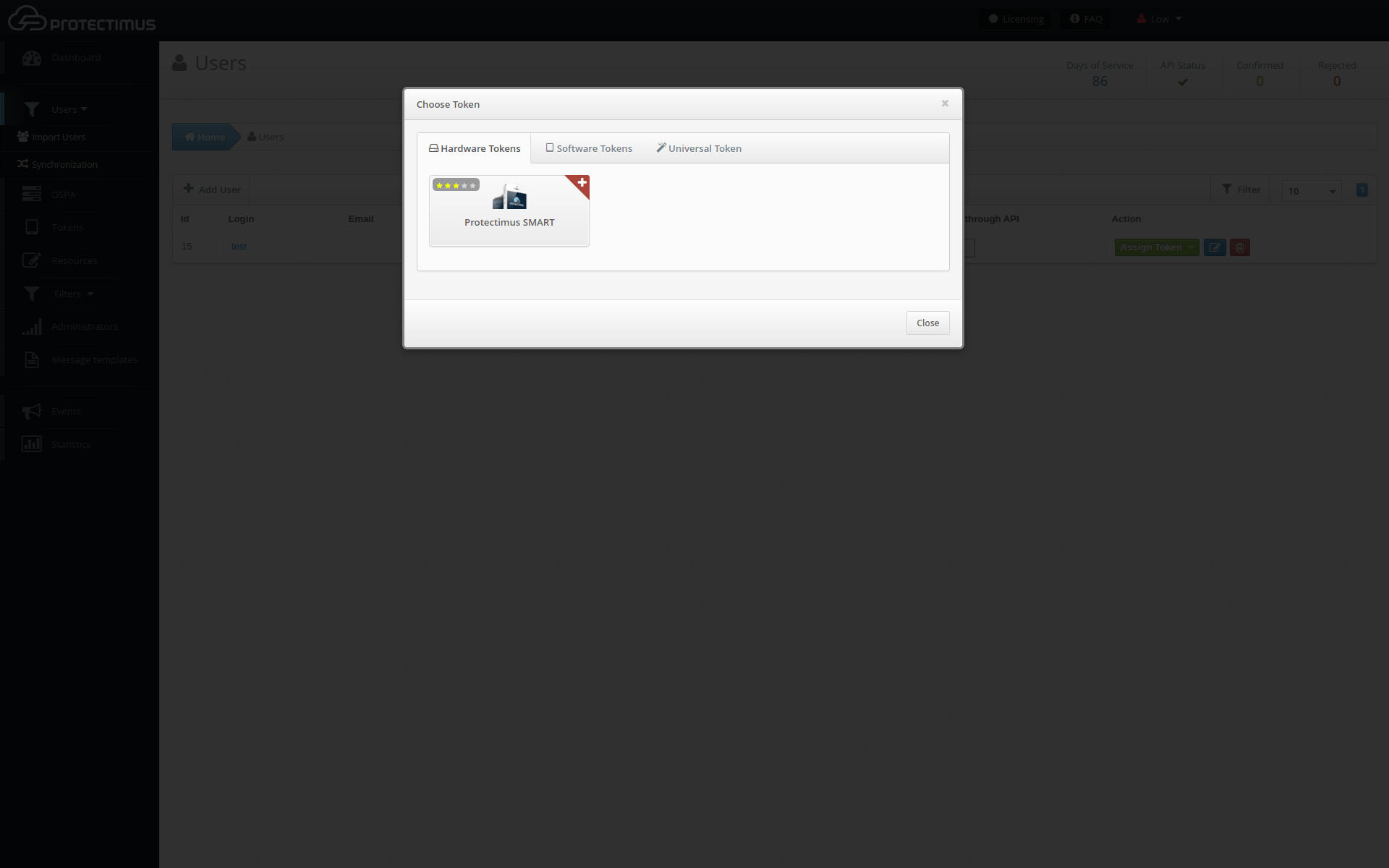
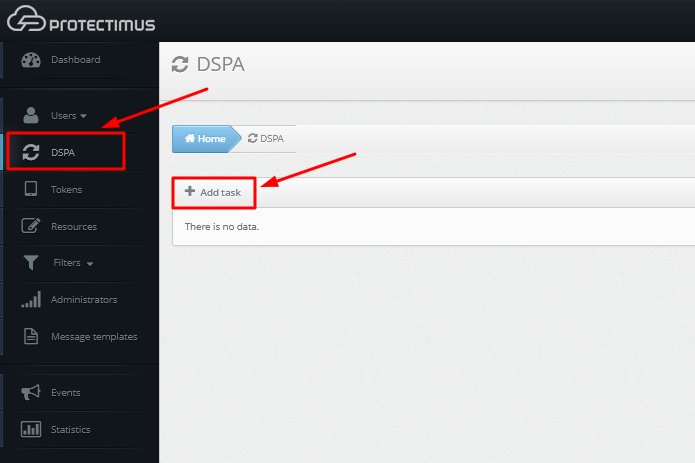
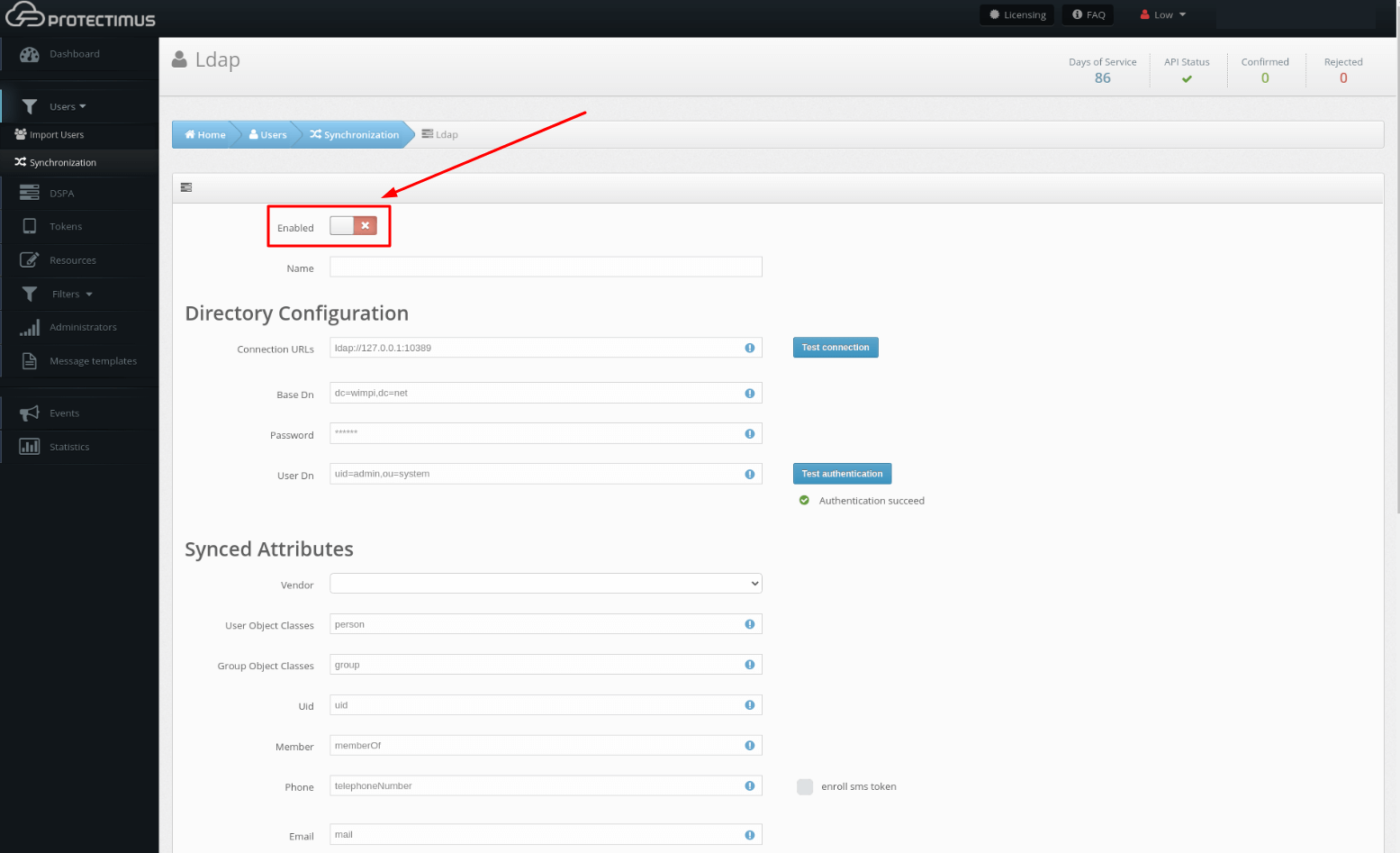
To activate the Protectimus DSPA component, go to the DSPA tab and activate the Enabled parameter.
Accordingly, to deactivate the Protectimus DSPA component, it is necessary to uncheck the Enabled parameter.
When DSPA is disabled, all passwords will be reset automatically (i.e., the dynamic part will be removed).
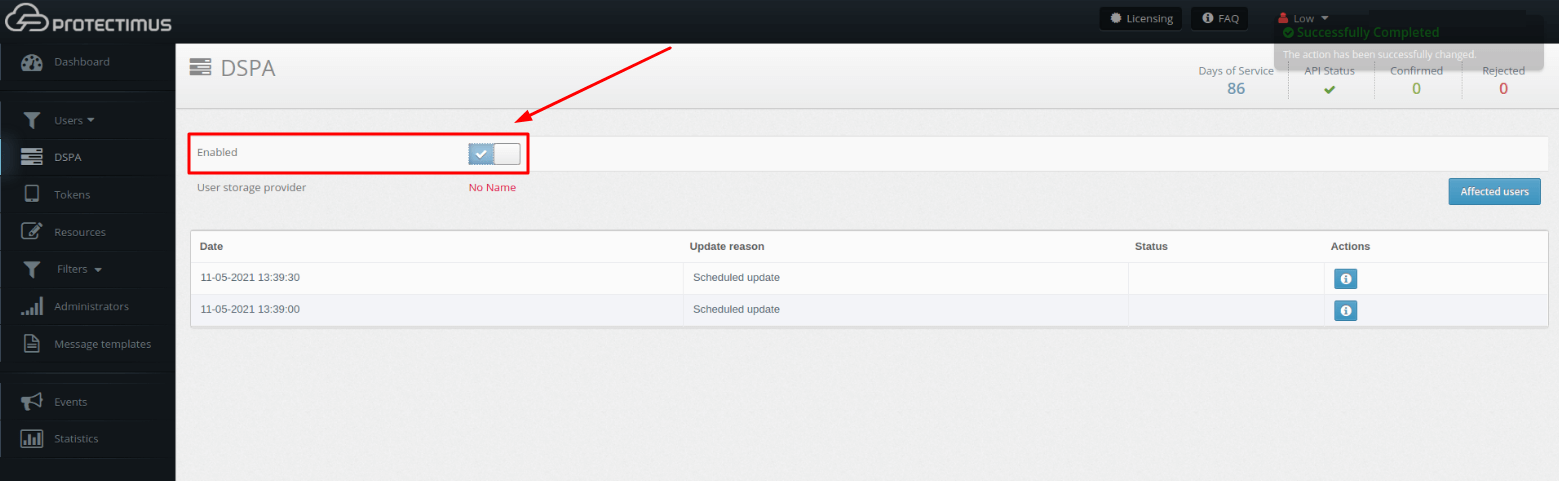
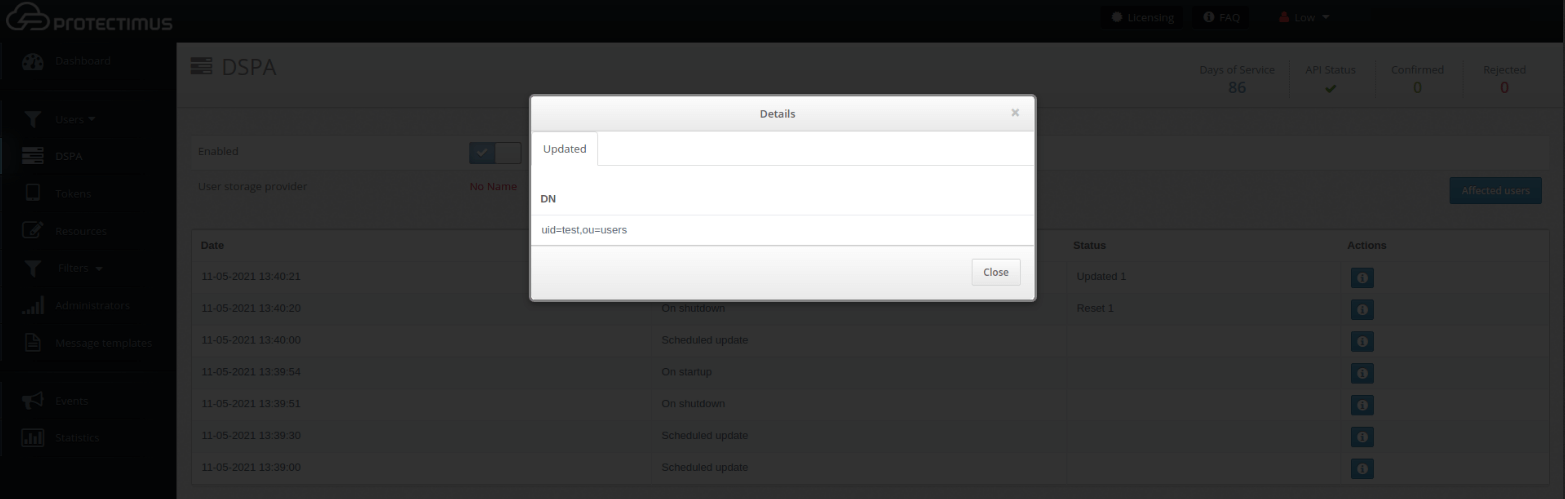
You can check whether these conditions are fulfilled by clicking the Affected users button on the DSPA tab.
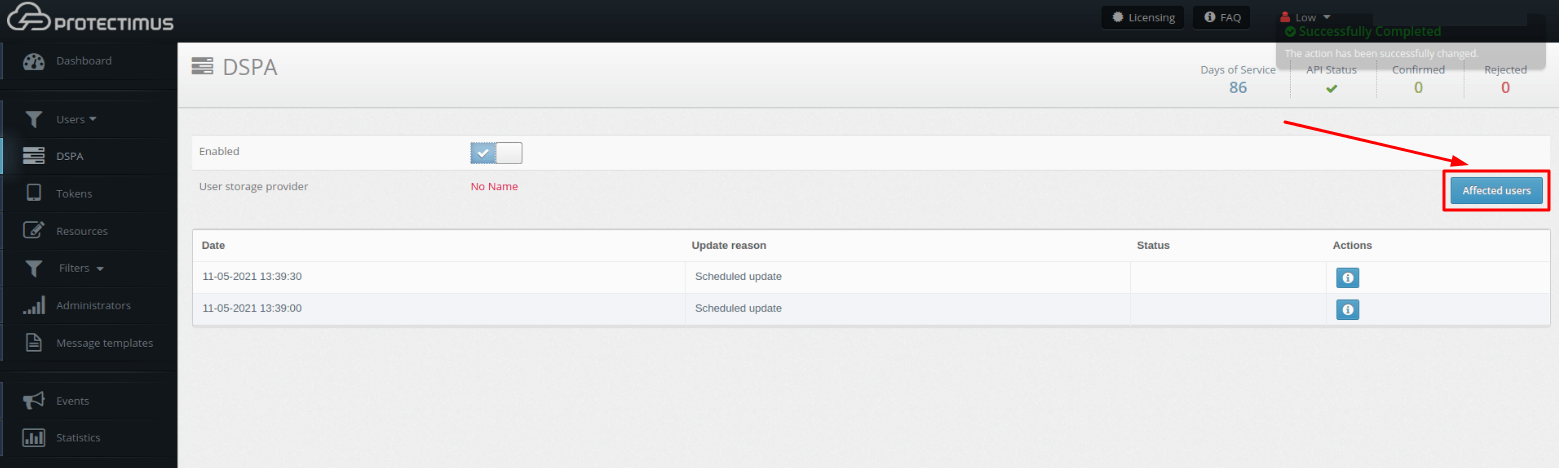
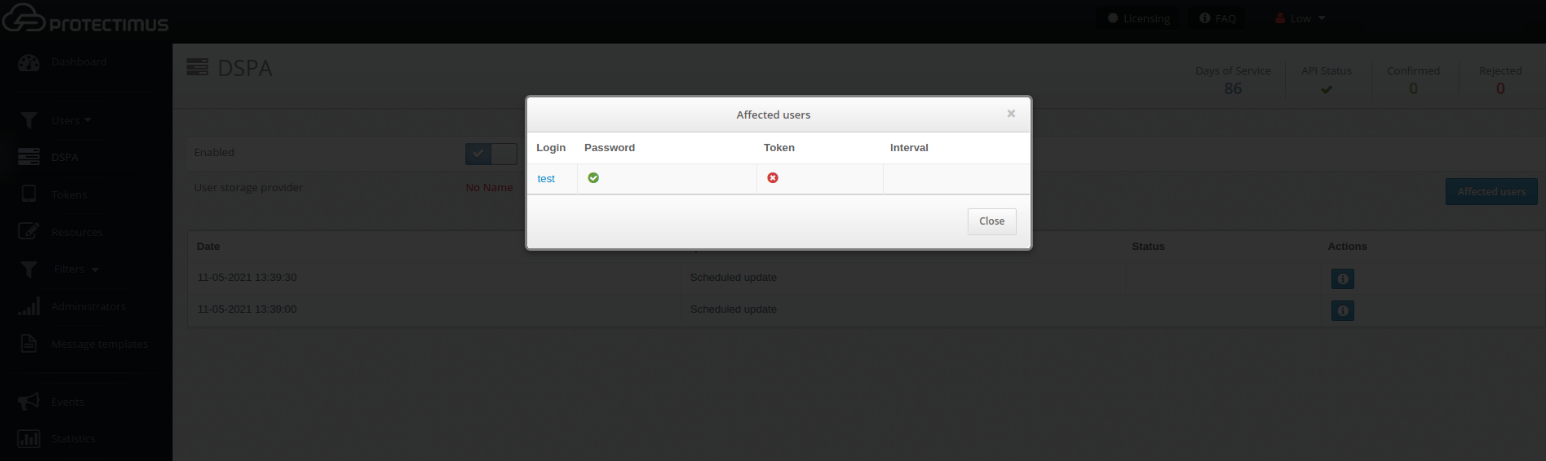
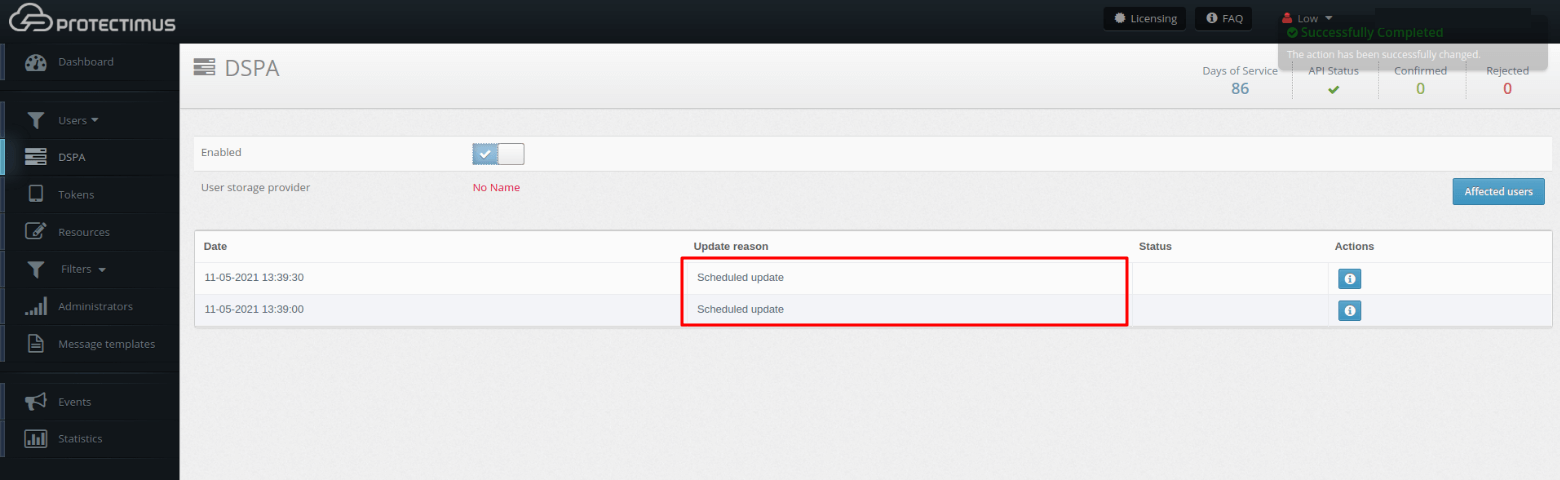
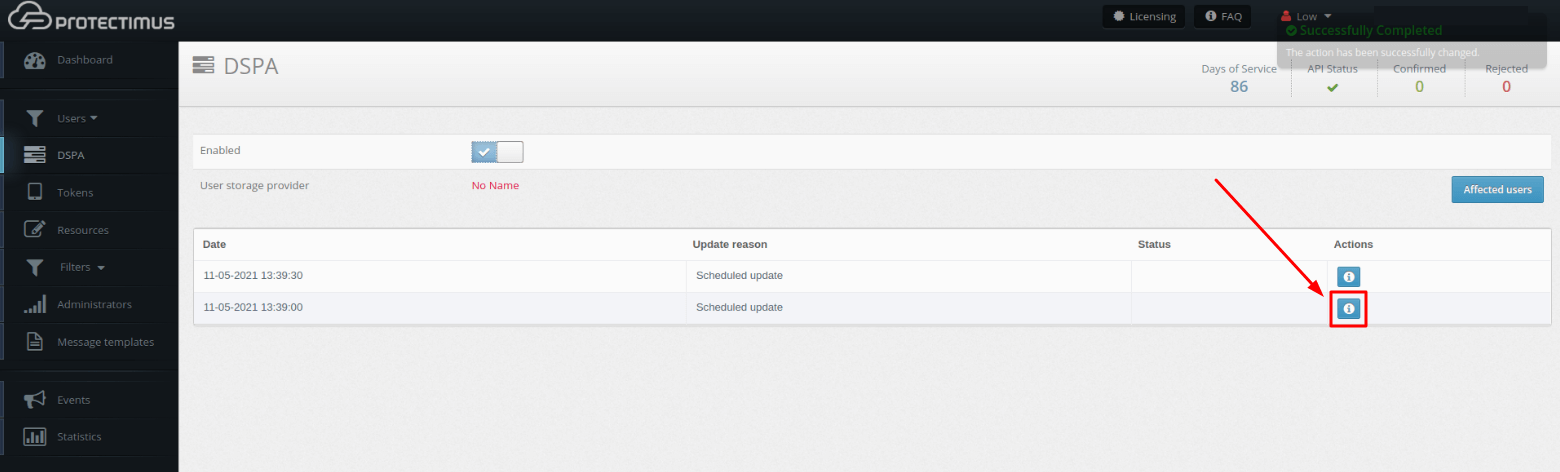
You can see the results of the passwords update in the table below.
When Protectimus DSPA is disabled, all passwords are reset automatically (i.e., the dynamic part is removed).
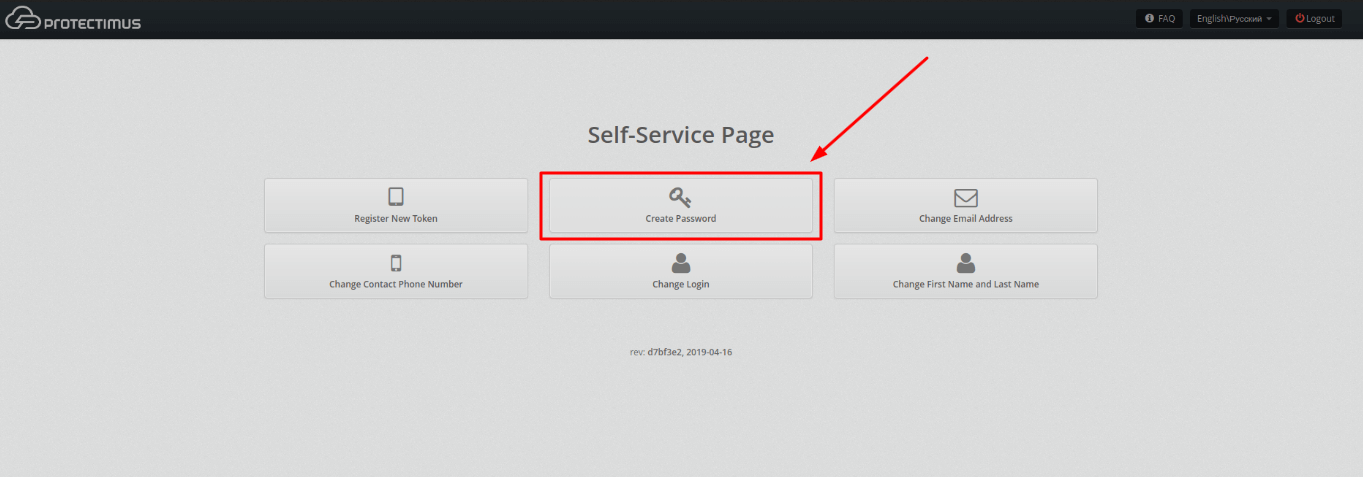
If you want users to enroll tokens and set passwords on their own, use the Users’ Self-Service Portal.
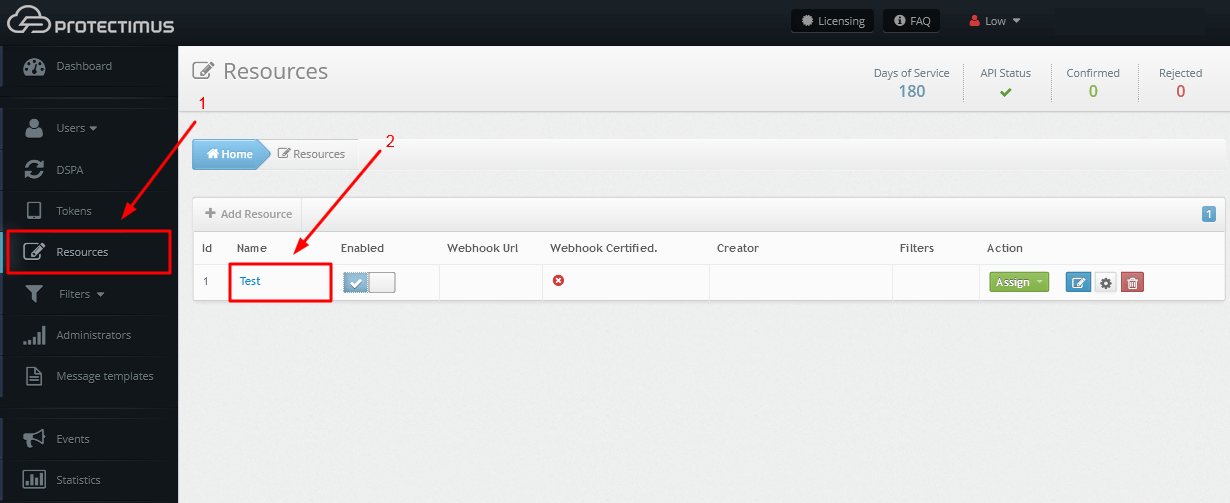
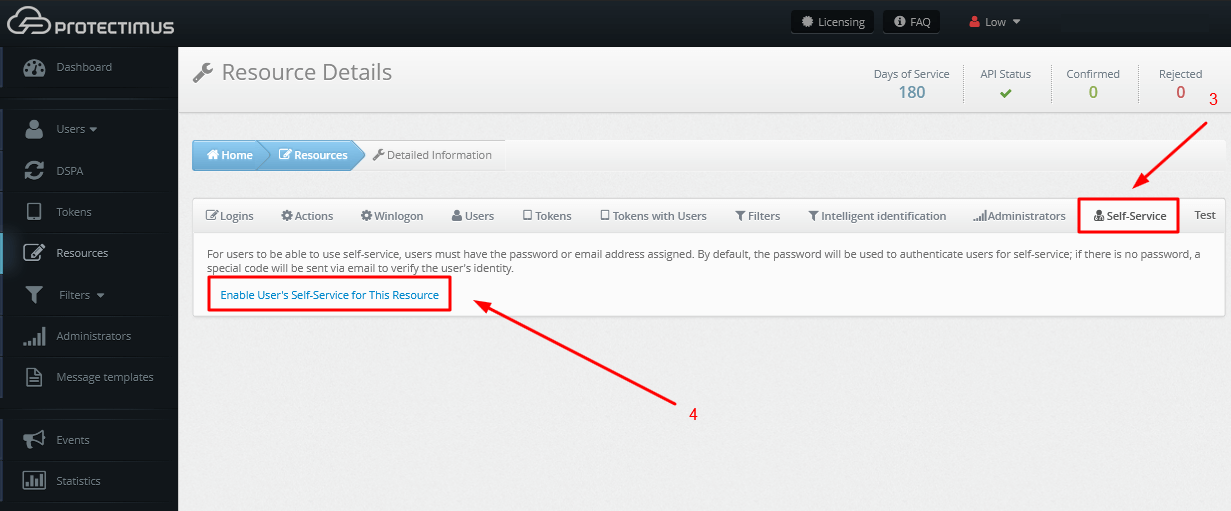
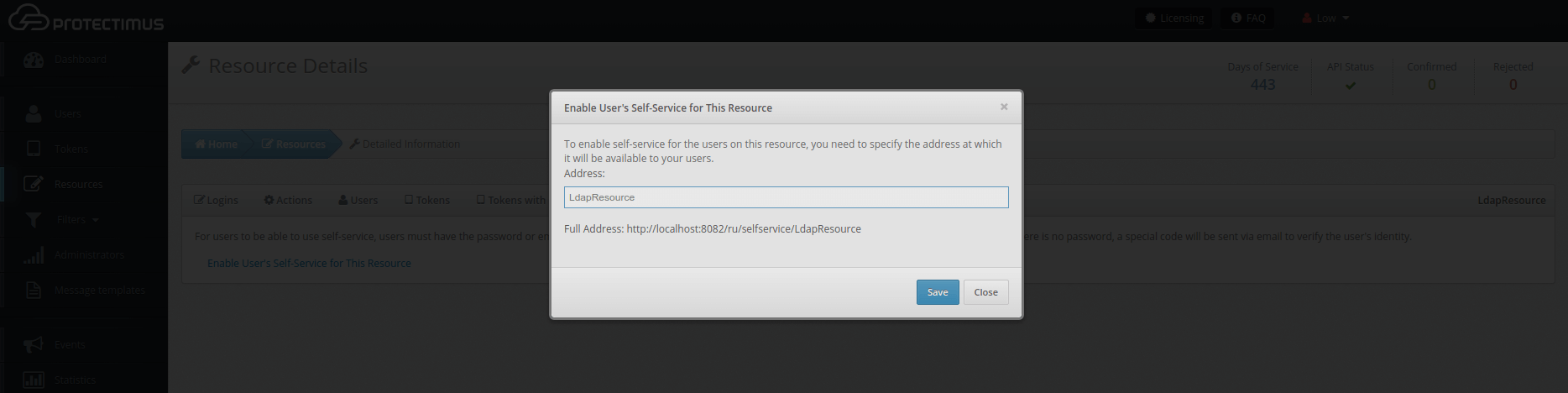
From the Resource information page, navigate to the Self-Service tab. You can enable self-service for a resource after entering the address at which the self-service page will be located. More detailed instructions on how to set up a self-service portal can be found in our Self-Service Portal Setup Guide.
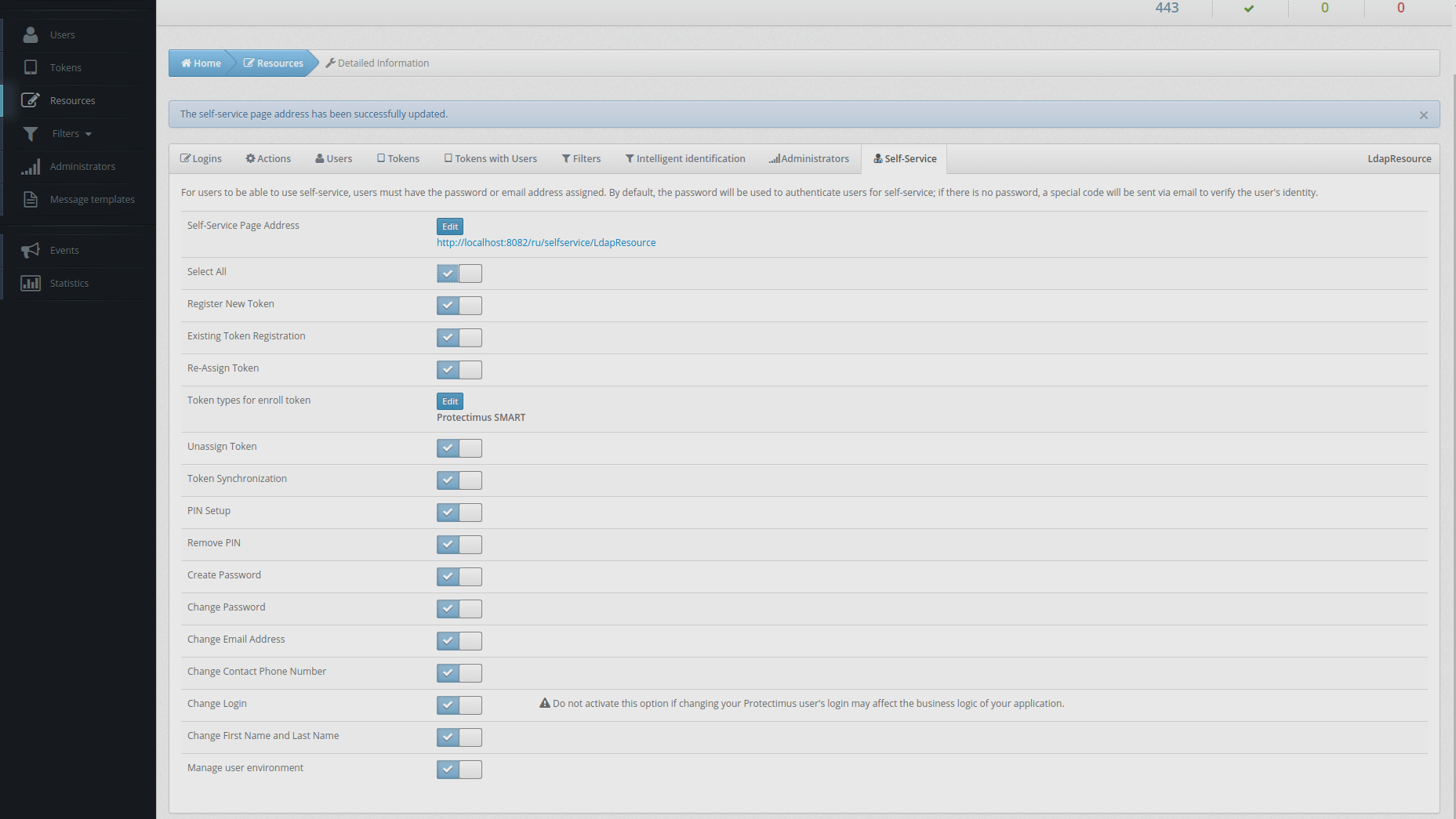
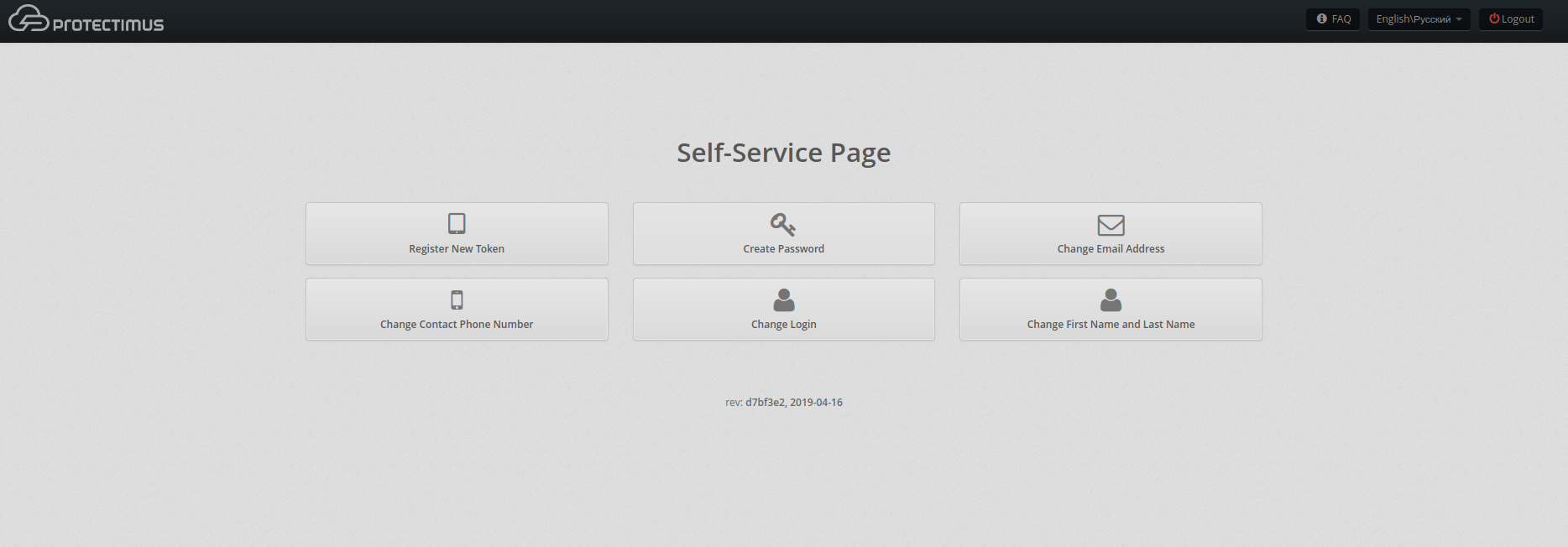
To sign in to their accounts on the Users’ Self-Service Portal, the user needs their login (CN) and one-time password (it will be sent by email).
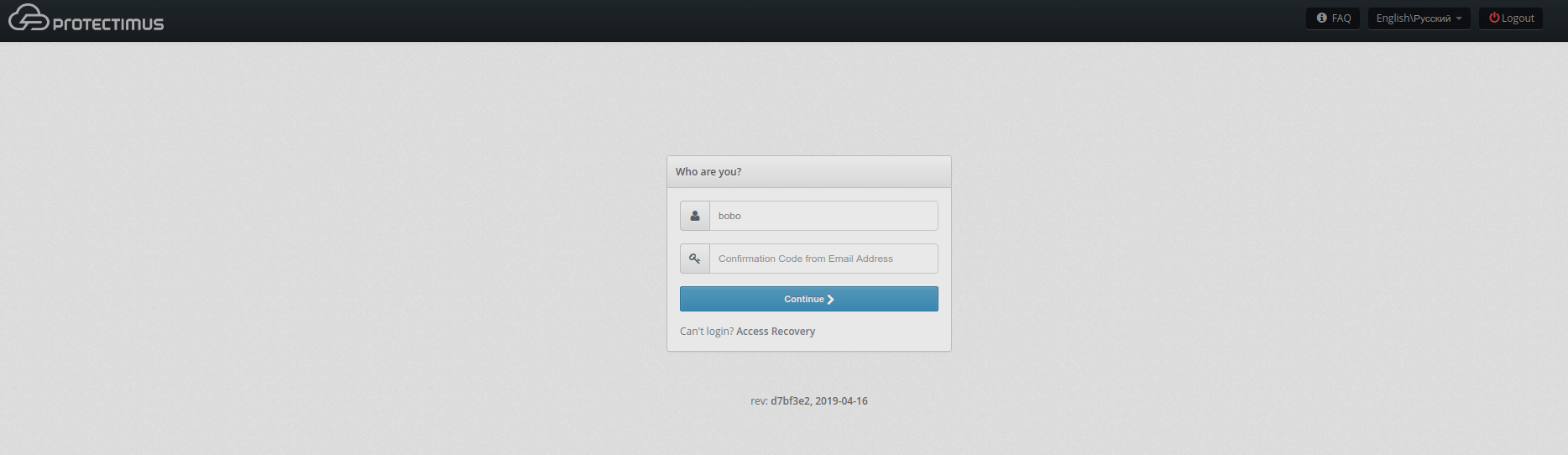
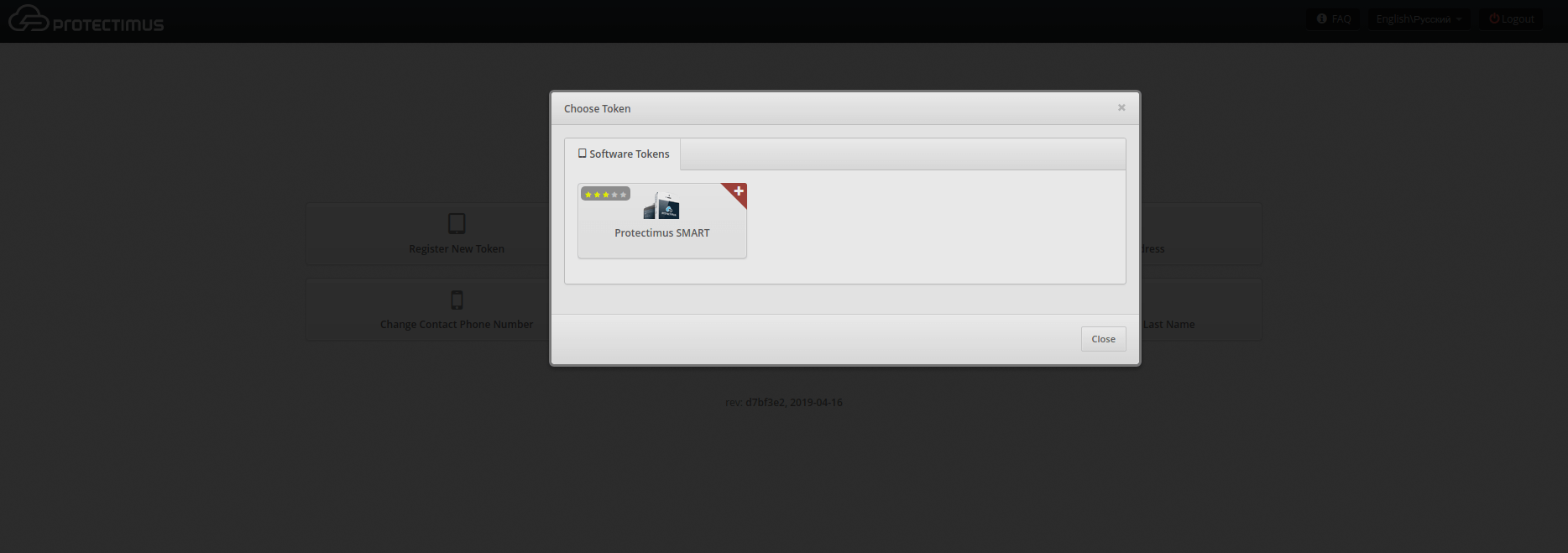
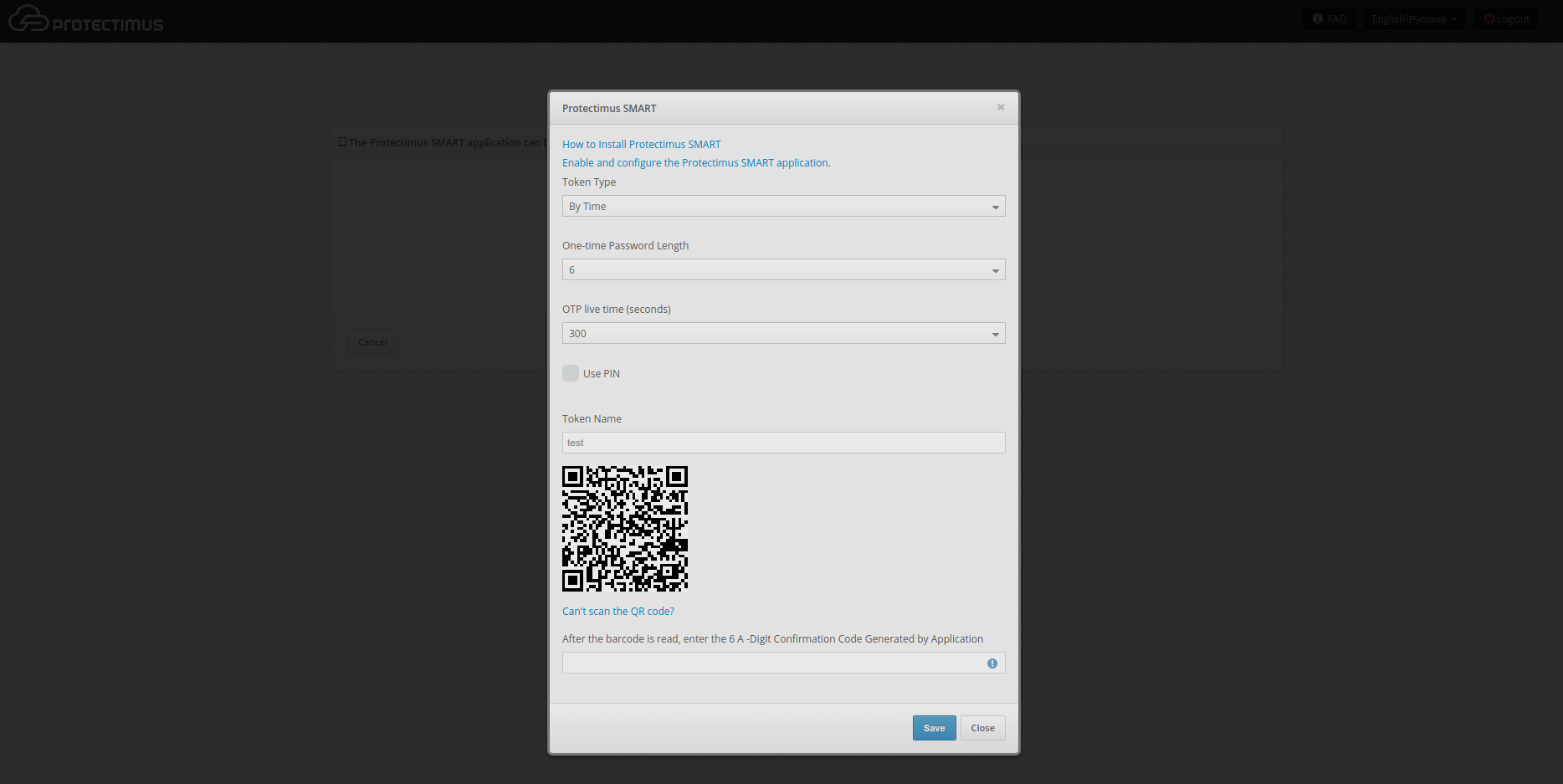
After that the user needs to enter the name of the token, set the length of the one-time password, select the lifetime of the one-time password and click on the “Show QR code” button.
To create a token, the user should scan the QR code using the Protectimus SMART OTP application, having previously installed it on their smartphone. The Protectimus Smart OTP app is available for free on Google Play and the App Store.
And to finish the token enrollment, the user must enter the OTP code generated using the Protectimus SMART OTP application.
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
США: +1 786 796 66 64
Ірландія: +353 19 014 565
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
США: +1 786 796 66 64
Ірландія: +353 19 014 565


