Програмований апаратний TOTP-токен у форматі карти
Класичні апаратні TOTP-токени SHA-1 з попередньо встановленими секретними ключами
Програмований апаратний TOTP-токен у форматі брелока
Класичний апаратний TOTP-токен з підтримкою алгоритму SHA-256
Програмований апаратний TOTP-токен у форматі карти
Класичні апаратні TOTP-токени SHA-1 з попередньо встановленими секретними ключами
Програмований апаратний TOTP-токен у форматі брелока
Класичний апаратний TOTP-токен з підтримкою алгоритму SHA-256
Безкоштовний застосунок для двофакторної автентифікації з хмарним бекапом, простим перенесенням токенів на новий телефон, PIN-кодом і біометричною автентифікацією
Безкоштовна доставка OTP через чат-ботів у месенджерах
Доставка одноразових паролів за допомогою SMS-повідомлень
Безкоштовна доставка одноразових паролів електронною поштою
Доставка одноразових паролів через push-повідомлення
Безкоштовний застосунок для двофакторної автентифікації з хмарним бекапом, простим перенесенням токенів на новий телефон, PIN-кодом і біометричною автентифікацією
Безкоштовна доставка OTP через чат-ботів у месенджерах
Доставка одноразових паролів за допомогою SMS-повідомлень
Безкоштовна доставка одноразових паролів електронною поштою
Доставка одноразових паролів через push-повідомлення
Інструкції
Цей посібник пояснює, як налаштувати багатофакторну автентифікацію (MFA або 2FA) для Parallels RAS (Remote Application Server) за допомогою системи Protectimus.
Коли ви інтегруєте двофакторну автентифікацію Protectimus з Parallels RAS, хмарний сервіс або локальна платформа Protectimus працює як RADIUS сервер через спеціальний конектор — Protectimus RADIUS Server. Parallels RAS у цьому випадку виступає як RADIUS клієнт.
Ось як це працює: конектор Protectimus RADIUS Server передає запити на автентифікацію від Parallels RAS до сервера багатофакторної автентифікації Protectimus (MFA). Залежно від отриманої відповіді, доступ надається або відхиляється.
Нижче наведено приклад інтеграції Protectimus 2FA з Parallels RAS для реалізації багатофакторної автентифікації (MFA) в Parallels RAS
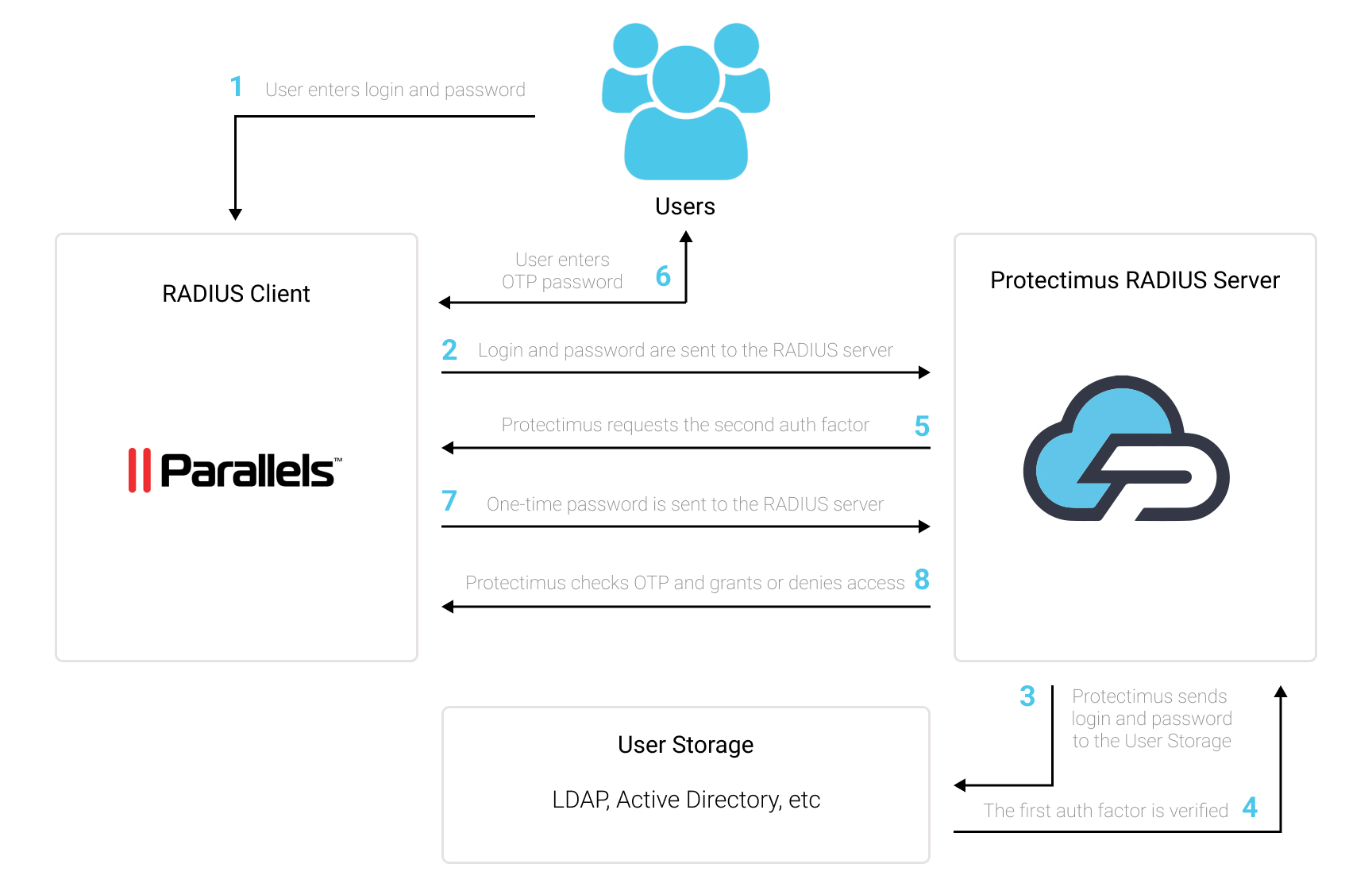
Ви можете налаштувати багатофакторну аутентифікацію (2FA) для Parallels RAS за допомогою Protectimus, використовуючи протокол RADIUS:
- Зареєструйтесь у SAAS сервісі Protectimus або встановіть локальну платформу Protectimus та налаштуйте основні параметри.
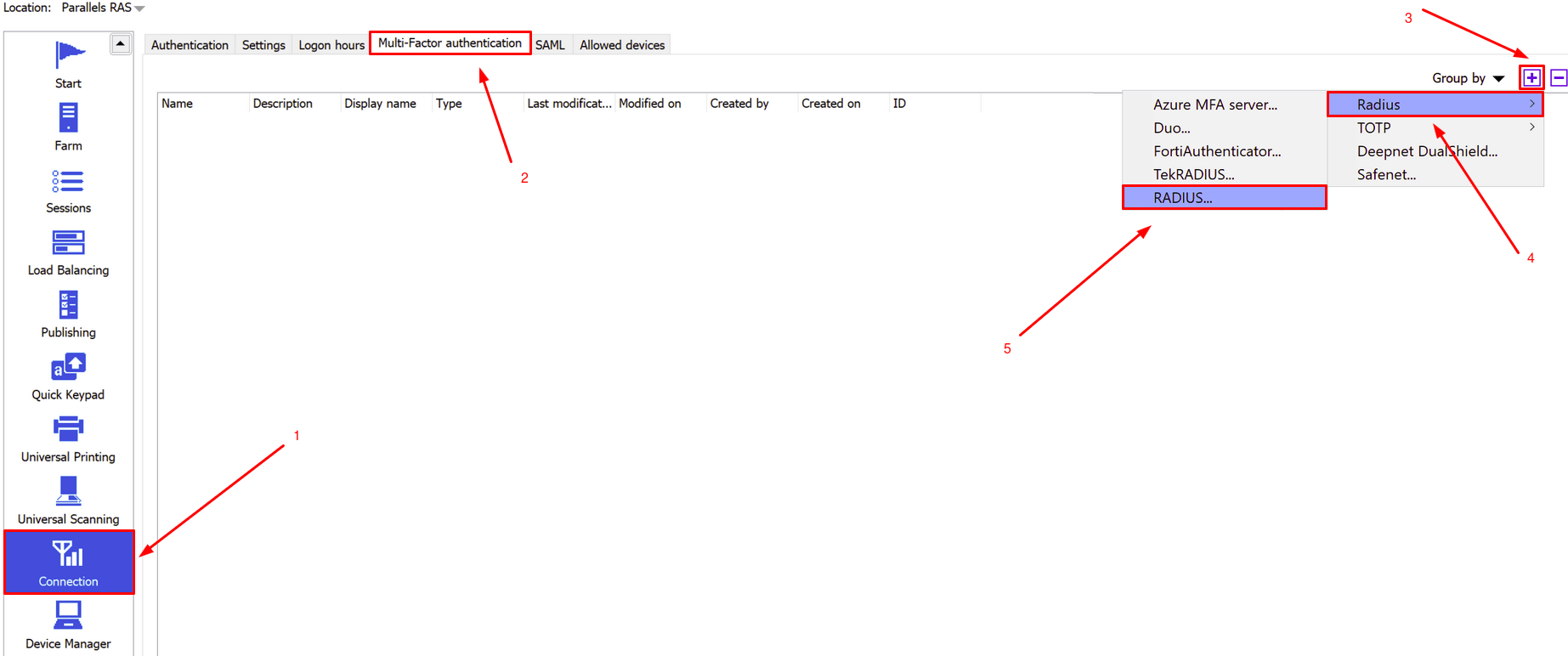
- Встановіть та налаштуйте Protectimus RADIUS Server.
- Додайте Protectimus як RADIUS сервер для Parallels Desktop.
Докладні інструкції щодо встановлення та налаштування Protectimus RADIUS Server для двофакторної автентифікації в Parallels RAS за допомогою RADIUS доступні в нашому Посібнику з встановлення Protectimus RADIUS Server для MFA в Parallels RAS.
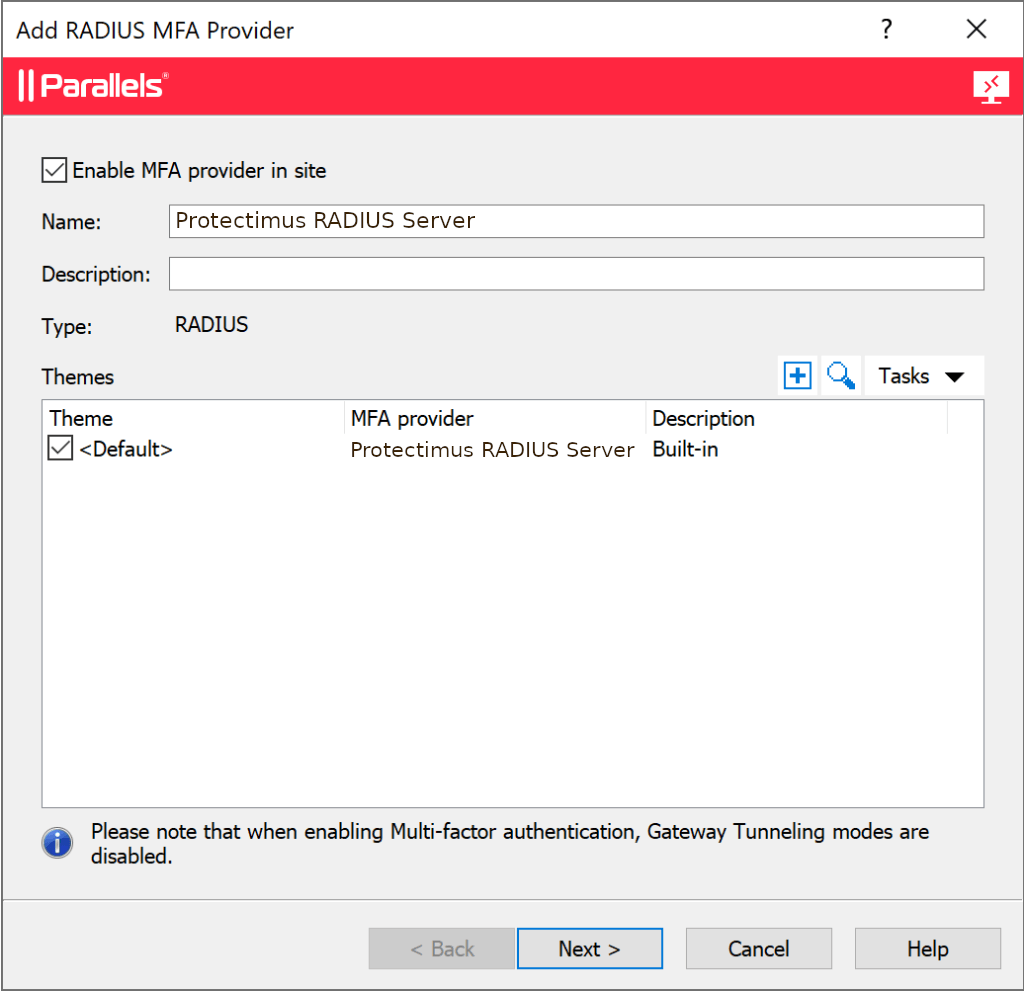
| Display Name | Придумайте назву для вашого RADIUS-сервера. |
| Primary Server | IP-адреса сервера, на якому встановлений компонент Protectimus RADIUS Server. |
| Secondary Server | Просто залиште це поле порожнім. |
| HA Mode | Просто залиште це поле порожнім. |
| Port | Вкажіть 1812 (або той порт, який ви налаштували у файлі radius.yml під час налаштування Protectimus RADIUS Server). |
| Timeout | Встановіть на 60 секунд. |
| Retries | Встановіть на 3. |
| Secret key | Вкажіть секретний ключ, який ви створили у файлі radius.yml (властивість radius.secret) при налаштуванні Protectimus RADIUS Server. |
| Password encoding | Виберіть PAP. |
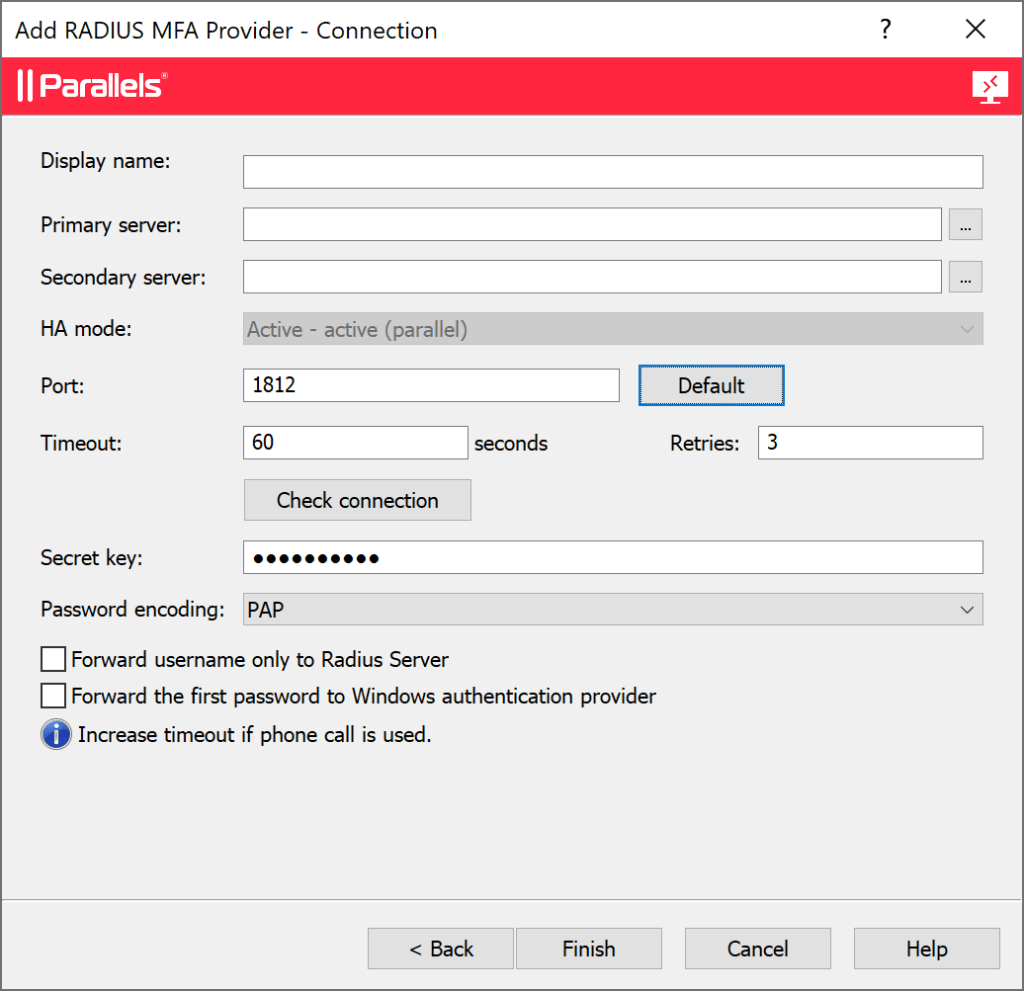
Зверніть увагу: Налаштування MFA для Parallels RAS є унікальним. За замовчуванням, провайдер RADIUS MFA підтримує лише метод автентифікації TOTP, що включає апаратні токени TOTP від Protectimus або додаток 2FA Protectimus SMART OTP. Для використання SMS, чат-бота чи email автентифікації може знадобитися додаткове налаштування. Якщо вам потрібна допомога з цими методами автентифікації, звертайтеся до нашої служби підтримки.
Інтеграція двофакторної автентифікації (2FA/MFA) для вашого Parallels RAS завершена.
Якщо у вас є запитання, зверніться до служби підтримки клієнтів Protectimus.
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ірландія: +353 19 014 565
США: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ірландія: +353 19 014 565
США: +1 786 796 66 64


