Програмований апаратний TOTP-токен у форматі карти
Класичні апаратні TOTP-токени SHA-1 з попередньо встановленими секретними ключами
Програмований апаратний TOTP-токен у форматі брелока
Класичний апаратний TOTP-токен з підтримкою алгоритму SHA-256
Програмований апаратний TOTP-токен у форматі карти
Класичні апаратні TOTP-токени SHA-1 з попередньо встановленими секретними ключами
Програмований апаратний TOTP-токен у форматі брелока
Класичний апаратний TOTP-токен з підтримкою алгоритму SHA-256
Безкоштовний застосунок для двофакторної автентифікації з хмарним бекапом, простим перенесенням токенів на новий телефон, PIN-кодом і біометричною автентифікацією
Безкоштовна доставка OTP через чат-ботів у месенджерах
Доставка одноразових паролів за допомогою SMS-повідомлень
Безкоштовна доставка одноразових паролів електронною поштою
Доставка одноразових паролів через push-повідомлення
Безкоштовний застосунок для двофакторної автентифікації з хмарним бекапом, простим перенесенням токенів на новий телефон, PIN-кодом і біометричною автентифікацією
Безкоштовна доставка OTP через чат-ботів у месенджерах
Доставка одноразових паролів за допомогою SMS-повідомлень
Безкоштовна доставка одноразових паролів електронною поштою
Доставка одноразових паролів через push-повідомлення
Інструкції
За допомогою рішення Protectimus для багатофакторної автентифікації (MFA) ви можете налаштувати двофакторну автентифікацію (2FA) в CentOS за кілька кроків.
Після ввімкнення 2FA у CentOS користувачі повинні будуть вводити два паролі для доступу до своїх облікових записів:
Таким чином, обліковий запис CentOS стає захищеним двома різними факторами автентифікації. Навіть якщо хакер викраде пароль користувача за допомогою фішингу, перебору, соціальної інженерії, підміни даних або будь-якої іншої атаки, він не зможе отримати доступ до облікового запису CentOS без одноразового пароля з 2FA токена користувача.
Ця інструкція пояснює, як налаштувати двофакторну автентифікацію (2FA) в CentOS за допомогою компонента Protectimus RADIUS 2FA для інтеграції з хмарним сервісом Protectimus Cloud 2FA або локальною платформою Protectimus On-Premise MFA.
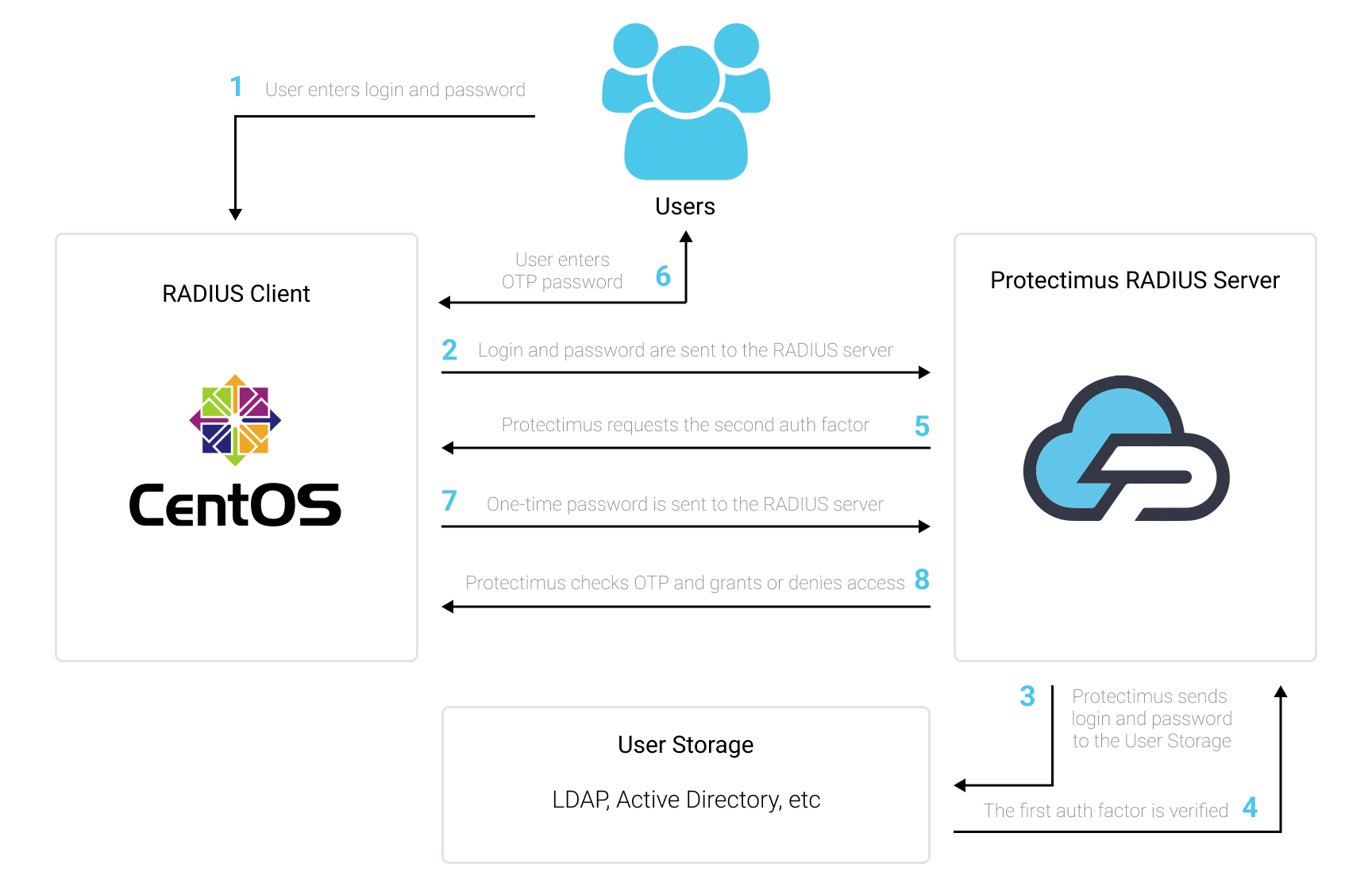
Ви можете налаштувати двофакторну автентифікацію (2FA) в CentOS за допомогою Protectimus, використовуючи протокол RADIUS:
- Зареєструйтеся в SAAS сервісі багатофакторної автентифікації або розгорніть On-Premise платформу MFA Protectimus, а потім налаштуйте базові параметри.
- Встановіть Protectimus PAM модуль для CentOS 2FA
- Встановіть та налаштуйте модуль Protectimus RADIUS Server.
yum -y install epel-release
yum -y install pam_radiusgit clone https://github.com/protectimus/platform-linux.git
cd platform-linux/radius
edit config/radius.yml
docker compose up -dradius:
secret: secret
auth-port: 1812
auth:
# Could be :
# - LDAP
# - PROTECTIMUS_PASSWORD
# - PROTECTIMUS_OTP
# - PROTECTIMUS_PUSH
providers:
- PROTECTIMUS_OTP
protectimus-api:
login: login@domain.com
api-key: aslkjdljsdlaskmWpXjT5K0xqLXkd3
url: https://api.protectimus.com/
resource-name: radius
resource-id: 723# server[:port] shared_secret timeout (s)
127.0.0.1 secret 1ChallengeResponseAuthentication yes#%PAM-1.0
auth required pam_sepermit.so
# protectimus pam radius
auth substack password-auth
auth required pam_radius_auth.so
auth include postlogin
# Used with polkit to reauthorize users in remote sessions
-auth optional pam_reauthorize.so prepareProtectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ірландія: +353 19 014 565
США: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ірландія: +353 19 014 565
США: +1 786 796 66 64


