Програмований апаратний TOTP-токен у форматі карти
Класичні апаратні TOTP-токени SHA-1 з попередньо встановленими секретними ключами
Програмований апаратний TOTP-токен у форматі брелока
Класичний апаратний TOTP-токен з підтримкою алгоритму SHA-256
Програмований апаратний TOTP-токен у форматі карти
Класичні апаратні TOTP-токени SHA-1 з попередньо встановленими секретними ключами
Програмований апаратний TOTP-токен у форматі брелока
Класичний апаратний TOTP-токен з підтримкою алгоритму SHA-256
Безкоштовний застосунок для двофакторної автентифікації з хмарним бекапом, простим перенесенням токенів на новий телефон, PIN-кодом і біометричною автентифікацією
Безкоштовна доставка OTP через чат-ботів у месенджерах
Доставка одноразових паролів за допомогою SMS-повідомлень
Безкоштовна доставка одноразових паролів електронною поштою
Доставка одноразових паролів через push-повідомлення
Безкоштовний застосунок для двофакторної автентифікації з хмарним бекапом, простим перенесенням токенів на новий телефон, PIN-кодом і біометричною автентифікацією
Безкоштовна доставка OTP через чат-ботів у месенджерах
Доставка одноразових паролів за допомогою SMS-повідомлень
Безкоштовна доставка одноразових паролів електронною поштою
Доставка одноразових паролів через push-повідомлення
Інструкції
Система двофакторної автентифікації (2FA) Protectimus підтримує єдиний вхід (Single Sign-On, SSO), який ініціює постачальник послуг (Service Provider, SP).
Це означає, що ваші користувачі зможуть входити до своїх облікових записів безпосередньо зі сторінки входу захищеного ресурсу. Під час спроби входу запит на авторизацію надсилається до сервісу ідентифікації (Identity Provider), у цьому випадку – Protectimus. Якщо Protectimus підтверджує особу користувача, той одразу отримує доступ до свого акаунта.
Схема взаємодії платформи двофакторної автентифікації Protectimus з Microsoft Office 365 через Keycloak наведена нижче.
Admin -> Show all -> Azure Active Directory -> Custom domain names -> “Add custom domain”
У DNS необхідно створити TXT-запис, щоб підтвердити, що домен додано в Azure AD.
https://www.microsoft.com/en-us/download/details.aspx?id=47594
Continue -> Customize -> Install (No checked options) -> Password Hash Synchronization -> Next -> Connect to Azure AD:
username@[something].onmicrosoft.com pass:
Next -> Add Directory -> domain
Ви можете створити окрему організаційну одиницю ( Organizational Unit; OU) для користувачів, облікові записи яких повинні бути захищені двофакторною автентифікацією, і налаштувати синхронізацію тільки для цієї OU. Кожен користувач в цій OU повинен мати електронну пошту, яка буде використовуватися як UPN (User Principal Name – основне ім’я користувача).
(Перевірте зображення нижче) ↓
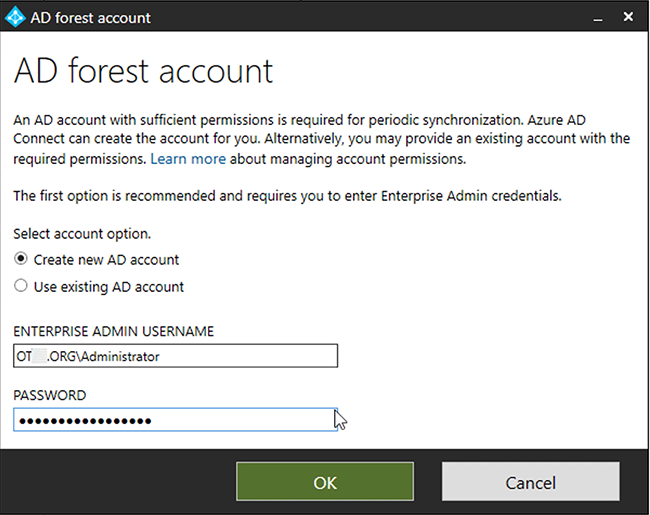
Next -> Next -> Sync Selected Domain
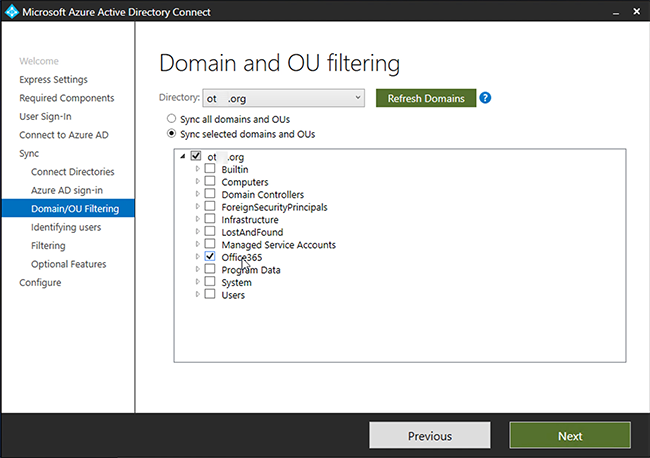
Next -> Next -> Next -> Exit.
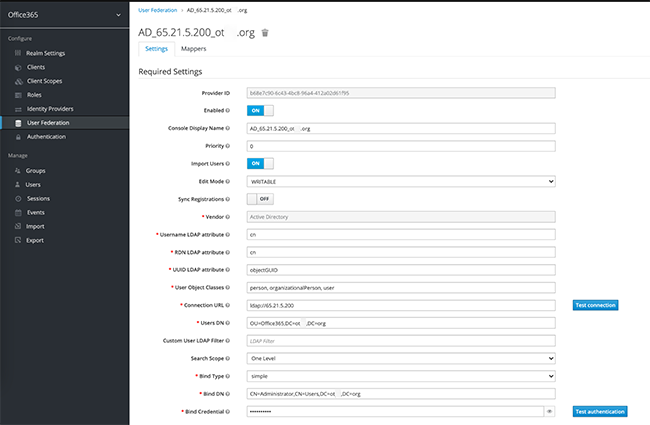
Додайте Realm і назвіть його, наприклад, Office365.
Додайте Mapper:
УВАГА! Важливо, щоб файл був названий: “urn:federation:MicrosoftOnline”
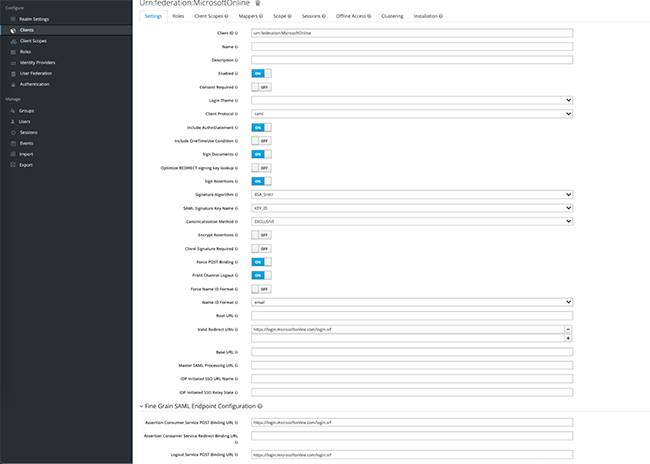
Перш за все, вам потрібно отримати SAML-сертифікат і перевірити його за цією адресою:
https://kc.dev.protectimus.com/auth/realms/[realm name]/protocol/saml/descriptor
Або перевірити сертифікат за допомогою відповідної функції в інтерфейсі – SAML keys.
Якщо система запитає про NuGet і PSGallery, встановіть їх також.
Виконайте наступний скрипт:
# get the public key certificate from keycloak
# https://kc.dev.protectimus.com/auth/realms/2608/protocol/saml/descriptor
# see X509Certificate
$cert="MIICoTCCAYkCBgF3Y+nVLjANBgkqhkiG9w0BAQsFADAUMRIwEAYDVQQDDAlvZmZpY2UzNjUwHhcNMjEwMjAyMTgwMTQ0WhcNMzEwMjAyMTgwMzI0WjAUMRIwEAYDVQQDDAlvZmZpY2UzNjUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC3eE+GuP2ubqH0C2sceb1iBsPr5LNIK0dtW67CQPL2tLM0YlRAFXu2sWRMKwPl8ZULvMzufA855j0Chd5KX1izVi8c6fclqge+OB9iMB05Ew/zGb8zmCXETgVU9+lsQFchd8M/I/i0QKKOatIbP50t9SKJI5daX78wb/IVk2pexB76cqXaQrrddh9ksXo3OFyFpAk1xlCC9Nu77QLCPWK4fBnSEbnzxDP3ZMhPXMQsn3MbD1SHGmHmJ93wMeXFGGIU77aDI/uAYZj1tb7dj/aICqG8RpUVXEolf8BDH/nT2TonYSmMaSqd99wCNJaKJWpyPd2qid7118DtOyPzZza/AgMBAAEwDQYJKoZIhvcNAQELBQADggEBAFglY4CdTJkGTL7/YUY1uBhSTSGvtbv6GiQ+2Uox3JVNVECB1Za63mUU1tTC/r4Jp02jRnTtBfSR7Sra+HDIKgAOkwcVTh2P++i1bk7PiY1Rb2ePrBtXWnb0GC8qCLAOK7b2/y9E1K5Wjg2Qg1dxnNZFys8CLpHkkYwMwChJA6E8DMg/bWUYfighBo4mAUpORAwqkmEB2mC39VbWZAUyBysQ5Cb9xK8RWnOgj7XhZfhpihK815z+uwirQjOFmGhWs2Mxk9PHkPkCFeWdcGGoRPvBuVYaG5/MrWu5hqQFtiu4ZDsySEnBdUqfudD6Iorc6QHVYf6VCunSIdE9L9sIovs="
$uri="https://kc.dev.protectimus.com/auth/realms/Office365/protocol/saml"
$issuer_uri="https://kc.dev.protectimus.com/auth/realms/Office365"
$dom="yourdomain.com"
$cred = Get-Credential
Connect-MsolService -Credential $cred
Set-MsolDomainAuthentication -DomainName $dom -Authentication Federated -ActiveLogOnUri $uri -SigningCertificate $cert -PassiveLogOnUri $uri -IssuerUri $issuer_uri -LogOffUri $uri -PreferredAuthenticationProtocol SAMLPВи можете перевірити, чи успішно виконана операція:
Get-MsolDomainFederationSettings -DomainName domain.nameВиконайте наступний скрипт:
$dom="yourdomain.com"
Set-MsolDomainAuthentication -DomainName $dom -Authentication managedВсе готово, відкрийте office365.com і спробуйте увійти за допомогою облікового запису з AD.
Якщо у вас є запитання, зверніться до нашої служби підтримки.
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ірландія: +353 19 014 565
США: +1 786 796 66 64
Protectimus Ltd
Carrick house, 49 Fitzwilliam Square,
Dublin D02 N578, Ireland
Ірландія: +353 19 014 565
США: +1 786 796 66 64


